Digital Piracy: Difference between revisions
| Line 137: | Line 137: | ||
[http://arstechnica.com/news.ars/post/20070619-the-youtube-effect-http-traffic-now-eclipses-p2p.html The YouTube effect: HTTP traffic now eclipses P2P, 2007] | [http://arstechnica.com/news.ars/post/20070619-the-youtube-effect-http-traffic-now-eclipses-p2p.html The YouTube effect: HTTP traffic now eclipses P2P, 2007] | ||
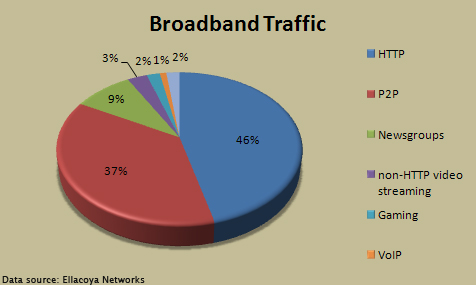
"In the Internet traffic race, P2P used to be way out in front. For years, P2P traffic eclipsed HTTP traffic as broadband users slurped down music and movies, some of which were actually legal. But P2P fell behind this year; for the first time in four years, HTTP traffic is out in front." | |||
"Breaking down the HTTP traffic, Ellacoya says that only 45 percent is used to pull down traditional web pages with text and images. The rest is mostly made up of streaming video (36 percent) and streaming audio (five percent). YouTube alone has grown so big that it now accounts for 20 percent of all HTTP traffic, or more than half of all HTTP streaming video." | |||
<center> | <center> | ||
Revision as of 15:04, 25 June 2007
Narratives
- Trevor is doing a project for school. Since he is very adept at video mashups, he decides to use clips from different TV shows and movies to assist him with the project. After completing the masterpiece, Trevor is very excited about his work and wants not only his class but also the whole world to see his creation. Due to the fact that long segments of copyrighted material were used in the making of this clip, he decides to post the video onto YouTube with an obscure name to avoid detection and uploads it onto five other video sharing services DailyMotion, Revver, GoFish, MySpace Video, and Facebook Video to act as mirrors. He then embeds the clip onto his blog and uses IM, email, text messaging, and Twitter to spread the word about this update.
Involves the use of the following applications: Adobe Premiere, Audacity, Trillian, Thunderbird
And services: YouTube, Daily Motion, Revver, GoFish, MySpace, Facebook, Textem, and Twitter.
- Questions raised from this scenario:
- What constitutes fair use?
- Do copyright laws impede creativity?
- Trevor and friends are hanging out in his basement on a lazy Sunday afternoon. They just watched a trailer of an upcoming blockbuster film and the whole group is very excited -- they canât wait to get in line to see the first midnight showing. Unfortunately, the filmâs release date is one week away. With nothing else to do, Trevor proposes that he could obtain a copy of the film via a private torrent network whose administrator is a member of an infamous release group. A few of his friends brings up the concern about piracy, but since the group is at Trevorâs house, using Trevor's internet connection, nobody objects -- in fact, a few never realized this was possible. After a quick debate about what to do, soon the majority of the group wants the movie downloaded and burned to discs for everyone to have.
Involves the use of the following applications: Quicktime, uTorrent, PeerGuardian 2, DivX Player, XviD Video Codec, AC3 Audio Codec
And services: <Torrent Website>, <Release Group>
- Questions raised from this scenario:
- Who should be more responsible for the piracy? The release group or the end user?
- How does group mentality play affect piracy?
- After seeing Trevor successfully obtain the movie, one of Trevorâs friends decide to get more movies from a P2P program he installed a while back. After firing the application up, his computer freezes. Not knowing what happened, Trevorâs friend does a simple force reboot and after the restart, everything seems fine. In the background processes, however, the P2P program automatically shared his whole media folder to the rest of the P2P community without telling the user.
Involves the use of the following applications: <P2P Application>
- Questions raised from this scenario:
- If a P2P program automatically shares all the media on a user's computer and the user is accused of copyright infringement, who should take the blame? The P2P company or the end user?
- The tech companies hired by the media industries to track down internet pirates is known for only targeting uploaders, rarely downloaders. Is this technique working?
- Trevor's family live in a fairly large condominium complex. Although all the computers in Trevor's house are connected via an encrypted wireless local area connection, Trevor's laptop has the ability to detect and connect to several other neighbor's wireless routers from the comforts of his bedroom. Since his laptop's wireless card is set connect to the closest router, Trevor often surfs the net & downloads copyrighted media using his neighbor's connection.
Involves the use of the following applications: <Wireless Configuration Utility>
- Questions raised from this scenario:
- A large majority of home wireless routers do not ship with WEP and WPA security turned on, causing many personal networks to be exposed to outside threats. If an outsider uses your wireless connection to facilitate illegal file sharing, what rights do you have as the innocently accused?
Introduction to Piracy
In the simplest terms, piracy is obtaining materials without the proper rights of legal ownership. In a broader sense, piracy can represent a whole range of intellectual and physical robbery. Like what the traditional usage of this term suggests, the theft committed by ruthless sea barbarians in the early 1700s is analogous to the present day methods to wrongfully acquire or distribute copyrighted material. Yes, the recent surge in pirated Pirates of the Caribbean films is, least to say, ironic.
The main driving force behind the argument against piracy centers on the degree of copyright infringement. The creator of a new piece of work has exclusive rights or ownership over all individual products of labor. Exclusive rights include, but are not limited to, distribution, reproduction, the ability to perform and make derivatives of the original. Under United States and most foreign law, copyright infringement is the unauthorized use of any works or materials secured by copyright. Piracy impinges on the copyright ownerâs exclusive rights without a license to do so and thus is considered a form of copyright infringement.
Why are copyrights necessary? Copyrights and the consequences of copyright infringement not only help protect intellectual property and ownership but also benefit society as a whole. By prohibiting duplication of new products and ideas for a designated period of time after creation, these laws prevent third party profiteers from stealing intellectual property and making a living from the hard work of others. Copyrights provide sufficient incentives for individuals to embark on revolutionary research, make their discoveries, and present their own creations without having to worry about ownership issues. These laws promote society's scientific and intellectual progress while piracy works as the counterforce.
Currently, the piracy problem spans many corporate sectors. The MPAA, RIAA, ESA, and SIAA, representing the movie, music, gaming, and software industries respectively, have all taken drastic measures to cope with the repercussions from illegal sharing of their clientsâ copyrighted works. Besides publishing annual damage reports that rave about the millions upon billions of lost profit and issuing pre-litigation notices to known violators, industries have begun collaborating with educational companies to bring piracy awareness into schools.
Although some critics of these so-called âprofit seekingâ businesses frown upon the use of educational programs designed by paid business partners, the piracy-ridden industries are targeting the right demographics. [1] [2] As studies conducted by third party researchers show, up and coming generations of digital natives are more prone than any other age group to experiment with and actually commit piracy. In a 2006 study, L.E.K. consulting group found the typical internet pirate is a male between the ages of 16 and 24. They reported, â44 percent of MPA company losses in the U.S. are attributable to college students.â [3] Growing up in an environment immersed with different technological facets, digital natives confront the copyright issue much earlier in childhood. More and more of our youth are desensitized about piracy and intellectual property rights at younger ages. In a recent PEW study, researchers found that around half of the young students interviewed were not concerned with downloading and sharing of copyrighted content for gratis. Teens who download music online agree, âitâs unrealistic to expect people to self-regulate and avoid free downloading and file-sharing altogether.â [4]
Overview
Technological advancements in years saddling the new millennium brought sweeping changes to the way data is transferred across the world. The rapid increase in the availability and acceptance of broadband internet connections has allowed people from the far reaches of the globe to download large multimedia files at much faster speeds than ever before. Sharing files between computers became easier for the general population to understand. The once dominant UseNets and IRC channels slowly gave way to user-friendly graphical user interface (GUI) peer-to-peer (P2P) programs where anyone can make a simple search to produce desirable results. Emerging technologies such as Wikis and BitTorrent coupled with old tools like email and instant messaging provided additional techniques where information can be transferred from one client to the next. Finally, the adoption of standardized media formats improved the sharing experience as a whole. All of these changes, old and new, provided the foundations for the present day's pervasive illegal distribution of copyrighted material.
Classifications
Since the piracy problem is pertinent across many fields, the definition and classification of this term has become extremely controversial over the years. While members of the justice system used piracy and theft almost interchangeably, people on the other side of the aisle view this practice as a grand exaggeration of reality. To them, it is unfair to compare downloading a song with real life thievery, or in this case, the carnage of 17th century sea "pirates." Even the organizations representing the large media and software industries do not have standard, unified definition for what they are fighting. MPAA defines piracy as "a serious federal offense." As for the different kinds of piracy, MPAA only mentions "internet piracy of movies, DVD copying, illegal sales and theatrical camcording." To the ISAA, "making additional copies, or loading the software onto more than one machine, may violate copyright law and be considered piracy." RIAA defines piracy as "the illegal duplication and distribution of sound recordings." Each organization is representing its respective industry, only showing pertinent consumers mere pieces of the puzzle. A definitive, yet agreeable definition for piracy and an universal way to classify the many faces of this issue is needed.
Piracy can be classified into two categories - digital and physical. Digital piracy is the illegal duplication and distribution of copyrighted content via electronic means. While the usage of online (peer-to-peer) P2P networks is the most pervasive outlet of digital piracy, hosting copyrighted files such as MP3s, movies, and software on web servers, uploading copyrighted media on video sharing sites, and even simpler ways of distribution such as via email or instant messaging are also considered illegal digital piracy. Similar to digital piracy, physical piracy involves the illegal duplication and distribution of works, but in physical form. Digital media can be illegally burned onto mediums such as CDs, DVDs and sold for a fraction of the retail price. Books, newspapers, magazines, course packs, journals, research and reports can also be duplicated in physical form and distributed. In fact, the MPAA reports, for 2005 "62 percent of the $6.1 billion loss result from piracy of hard goods such as DVDs, 38 percent from internet piracy." [5] Physical piracy of media and other forms of content are much more pervasive on a global scale. This method of copyright infringement can be further classified into individual license, corporate to end-user, reseller and distributor violations.
Categorizing piracy by methodology only answers the "how" question. "Why" people pirate can be grouped by a measurement of intentionality. Kids and adults alike have different reasons for why they choose to download from P2P networks or buy counterfeit media. Some, however, are quite unaware of their actions while others are completely oblivious between what is right and wrong. In a recent ZDNet report on UK businesses running Windows, "Microsoft would not put a figure on how much it loses from unintentional piracy, but said that while 85 percent of UK small businesses run Microsoft software, only 15 percent pay for it." [6] All of this, of course, hinges on intentionality. Individuals who are completely aware of their actions are considered director facilitators of digital or physical piracy. From the acquirers of prerelease content, to the online intermediaries, from the distributors to the customers, this group includes people anywhere on the piracy chain. Intentional piracy usually involves some sort of monetary gain at the loss of the copyright holder. Individuals somewhat aware of piracy are usually consumers of counterfeit content. They understand to an extent what they are doing is wrong but choose to go ahead with it for various reasons such as personal enjoyment or curiosity. Educating these indirect facilitators the wrongs of piracy is the recording industries' best chance at curbing this problem. Finally, consumers completely unaware of piracy are usually those who are victims of counterfeit scammers or those whose computer or personal network has been hijacked to illegally contribute copyrighted material.
Origins
In the last millennium, there were only a few landmark innovations affecting the dissemination of media content. Gutenbergâs invention of the printing press in 1450 allowed for easy and inexpensive duplication of paper works. With the assistance of moveable type, productivity of scribes (now hired machine workers) increased exponentially. As profit margins shot through the roof, the publishing industry was born. In the late 1970s, early 1980s, the introduction of the Sony Walkman gave humans the capability to record audio while the videocassette system did the same for video. In the 1990s, the popularization of CD/DVD optical disk technology gave birth to the new era of digital recording. The 21st century ushered in the acceptance of new digital mediums. Combined with the enormous success of the internet, computers and newly developed network protocols took information sharing to a new level. Each one of these new "machines" included a "mechanism" for which a certain "media" was affected. Each innovation established or revolutionized an industry. Each provided a faster, even better way to spread information. Each, however, brought with it intellectual property issues, for each forced or is forcing policy makers to amend copyright standards.
| Media | Mechanism | Machine |
| Paper | Movable Type Publishing | Printing Press |
| Cassette/VHS Tape | Magnetic Recording | Walkman/VHS Machine |
| CD/DVD | Optical Disk Recording | CD/DVD Recorder |
| Standardized Computer Files (.mp3/.avi/.wmv/.mp4) | P2P/Torrent Networks | Personal Computer |
On June 1st, 1999, Shawn Fanning, a student from Northeastern University, released what would be called "the godfather of peer to peer programs" â Napster. At that time, although there were other technologies facilitating the sharing of media, "Napster specialized exclusively in music ... and presented a user-friendly interface." [7] Soon after being launched, this easy to use, cost-free program became wildly popular because everyday computer users had enough basic technical knowledge to contribute to the file sharing movement. Napster's sensation, however, was short lived. Its "facilitation of transferring copyrighted material raised the ire of the Recording Industry Association of America (RIAA), which almost immediately â in December 1999 â filed a lawsuit against the popular service." [8] Because Fanning earned profits through advertisements and operated the project via a client-server protocol with a centralized file list, the RIAA push for intentional copyright infringement ultimately succeeded.
Napster's immense success planted the seed for today's P2P debacle. On one hand, this innovation sparked the countermovement by the RIAA and other recording companies to curtail infringement. On the other hand, Fanning's concept of dedicated media distribution GUI programs inspired next generations of P2P coders to create iterations of the Napster design even more insusceptible to the current copyright laws. The 1986 "Betamax case" allowed Sony to manufacture VCRs "because the devices were sold for legitimate purposes and had substantial non-infringing uses" (Betamax). In the cases brought up against these new P2P projects, even though the prosecution was successful in proving the Betamax argument invalid, the victory in the courtroom only fueled the rapid spawning of new P2P projects.
In March 2001, the FastTrack protocol allowed for a more distributed network without a centralized sever. Faster computers in the network now has the ability to become supernodes, or machines with server-like capabilities to help out slower clients. Newer P2P programs like KaZaa, Grokster, and iMesh successfully implemented this protocol and gained millions of users. Two years later, "FastTrack was the most popular file sharing network, being mainly used for the exchange of music mp3 files. Popular features of FastTrack are the ability to resume interrupted downloads and to simultaneously download segments of one file from multiple peers." [9] During the same decade, true distributed network protocols such as the open source Gnutella and eDonkey 2000 also caught on with mainstream P2P file sharers. Likewise spawning other P2P clients, Limewire, Morpheus, and eDonkey. Compared to Napster, these newer networks were able to attain higher maximum speeds because every client also had the capability to share files. Also, since the copyrighted material were stored on individual computers, with the proper disclaimers, the P2P client companies were able to brush off the majority of legal accusations.
The acceptance of the mp3 format in the mid 1990s allowed users to compress songs into several megabyte files, all of which were easily distributable throughout the digital world. In the early 2000s, DivX, a newly developed video compression codec did the same for video. As more households switched over to broadband internet, the ability to transfer large files finally became plausible. However, even with DivXâs help, typical compressed DVD rips still hovered above 600 MB. Since traditional P2P protocols could not handle the new bandwidth demand efficiently, a newer distributive protocol called BitTorrent was quickly adopted.
BitTorrent was developed by Bram Cohen in 2001. By splitting large files into sizable pieces, data can be widely distributed and shared "without the original distributor incurring the entire costs of hardware, hosting and bandwidth resources." [10] For a client to download additional data, one must supply requested chunks of the larger file to newer recipients. Cohen's implementation not only proved to be incredibly efficient, but also managed to exploit a legal loophole. While the initial releases of the BitTorrent system depended on trackers to operate, these servers answered the requests clients only by giving them the location of other computers who are concurrently sharing the same sought after file. Since tracker servers did not host any of the copyrighted content, the prosecution had a harder time shutting down these organizations. BitTorrent soon grew to become the sharing mechanism of choice.
Digital piracy only constitutes a portion of the whole picture. True, today's extensive counterfeit CD/DVD markets are largely fueled by the established presence of piracy in the digital realm. Resellers and distributors usually get the content to copy from online sources. But, the history of physical piracy can be traced back to the days of floppy disks and cassette tapes. In 1964, the Philips company brought compact audio cassette technology to the United States. Although there were other magnetic cartridge technologies available, Philip's decision to license the format for free made compact cassettes the most accepted recording medium during this time. [11] In the 1970s and 1980s, cheaper multi-track recording mechanisms for artists and the consumer compact cassette boom prolonged the popularity of this new medium. The trading of these recordable cassettes among music fans across the U.S. and U.K. via the mail was dubbed "cassette culture." [12] Acceptance of floppy disk technology starting from the early 1980s provided users an easy way to copy computer related files. Copyrighted computer software and games especially could be easily duplicated using these disks. Of course, anti-piracy campaigns also started as a reaction to these new fads. The British Phonographic Industry, a music trade group in the 1980s, launched an anti-piracy campaign with the slogan "Home Taping Is Killing Music." Similar to the RIAA's concerns today, the BPI was afraid that the rise of a new recording medium (in their case, the cassette tapes) would hurt legitimate record sales. In 1992, the Software Publishers Association produced an anti-piracy campaign centered around a video commercial called "Don't Copy That Floppy." [13]
Current Methodologies
Advent of the internet and the rapid increase of personal computers means more people than ever before have the capability to share information online. Though this technology advancement gives users unprecedented access to the rest of the world's data, balancing proper copyright restrictions and justifiable sharing freedoms have not been attained. Thus, many have pointed to these new technologies as the facilitators of so-called "digital piracy." Today, users employ many different applications and services to illegally transfer copyrighted material. Factoring intentionality out of the equation, this section aims to introduce these digital trade tools.
Direct connection
Highlights: Live Messenger, YouSendIt, MyTunes
The easiest and fastest way for a person to obtain copyrighted materials is from direct sources. Friends, family, classmates -- an individual's immediate relations are great sources to
P2P networks
Highlights: Kazaa, eMule, the original Napster
Torrent networks: Torrent indexers & clients
Highlights: ThePirateBay, MiniNova, uTorrent, Azureus
Survey: Movie-swapping up; Kazaa down, 2004
"Online movie trading is skyrocketing, but onetime leader Kazaa is tumbling in use, according to a new worldwide survey of file-swapping traffic from network management company CacheLogic."
"The overall level of file sharing has increased," said Andrew Parker, CacheLogic's founder and chief technology officer. "Users have migrated from Kazaa onto BitTorrent."
"The company's observations add to what have been growing indications of a generational shift under way in the peer-to-peer world, with computer users increasingly downloading big files such as movies and software, and reducing reliance on onetime file-sharing king Kazaa."
"Kazaa, by contrast, is less efficient for big files, and may be used more widely to trade MP3 music files, which can be a hundredth the size of a movie file."
Warez networks
Highlights: Astalavista.box.sk, Cracks.ms
FTP and web servers
Web mediums: Media aggregators & sharing websites
Highlights: Tv-Links.co.uk, PeekVid, YouTube, Veoh
The YouTube effect: HTTP traffic now eclipses P2P, 2007
"In the Internet traffic race, P2P used to be way out in front. For years, P2P traffic eclipsed HTTP traffic as broadband users slurped down music and movies, some of which were actually legal. But P2P fell behind this year; for the first time in four years, HTTP traffic is out in front."
"Breaking down the HTTP traffic, Ellacoya says that only 45 percent is used to pull down traditional web pages with text and images. The rest is mostly made up of streaming video (36 percent) and streaming audio (five percent). YouTube alone has grown so big that it now accounts for 20 percent of all HTTP traffic, or more than half of all HTTP streaming video."
Before the popularization of digital formats and the increased accessibility of the internet, illegal distribution of physical copyrighted material was the prevalent form of piracy.
Individual license violation
(no profit margin, software & media)
- Installing software on multiple computers, overusing licenses
- Exploiting upgrade options
- Using academic or other non-retail software for commercial purposes
- Copying licensed software or locked media
- Distributing / sharing copied content with immediate relations
Corporate to end-user
(improves profit margin, mainly software)
- Installing software on multiple computers, overusing licenses
- Client-server overuse
- Hard disk loading
Reseller and distributor
(pure profit, software & media)
- Selling copied or counterfeit software for a reduced price
- Street vendors & illegal stores
- Online distribution of software via mail (direct resell, auctions)
- Unlicensed movie theaters & rental facilities
Over a period of 18 months, LEK surveyed 20,600 movie consumers from 22 countries and found "62 percent of the $6.1 billion loss result from piracy of hard goods such as DVDs, 38 percent from internet piracy." [14]
By understanding methodologies and motivations behind these commonly used utilities, we can have a better understanding of piracy as plays out in the lives of digital natives.
Piracy & Law
The chain reaction that instigated copyright regulations dates back to the fifteenth century. Gutenbergâs printing press marked the beginning of a new era of information distribution. True, this device facilitated the mass production and dissemination of human knowledge; however, it also carried repercussions. The formerly tedious task of duplication by hand was sped up to a rate that warranted tighter controls. When this technology arrived in England, the "need for protection of printed works was inevitable." [15] In 1710, the English Parliament passed the first official law concerning copyrights. The Statue of Anne "established the principles of authorsâ ownership of copyright and a fixed term of protection of copyrighted works." [16] Almost three hundred years have elapsed since this passing of this statue. Although some ideological remnants still remain, todayâs US copyright law "has been revised to broaden the scope of copyright, to change the term of copyright protection, and to address new technologies." [17]
Present day US copyright regulations stemmed from the first days of nationhood. When Americaâs founding fathers composed the United States Constitution in 1787, they gave Congress the power "to promote the progress of science and useful arts, by securing for limited times to authors and inventors the exclusive right to their respective writings and discoveries." [18] This line of text in Article I, section 8 bestowed upon the State fundamental rights to a monopoly over the copyright industry. It was the governmentâs job to asset, distribute, and control all copyrights. "The First Congress implemented the copyright provision of the U.S. Constitution in 1790," modeled quite similarly to the Statue of Anne. [19] Since then there had been three major revisions which occurred in the years 1870, 1909, and 1976.
With arrival of the digital age, Congress amended the copyright act to "prohibit commercial lending of computer software" in 1990. [20] This revision did not solve all the problems, for technology was evolving at a rapid pace. Computer savvy individuals were finding ways to bypass government copyright regulations. For example, under copyright laws up to the No Electronic Theft (NET) Act of 1997, people who intentionally distributed copyrighted software without receiving monetary benefits could not be prosecuted. The NET Act amended this loophole. [21] Following NET, 1998 was also a big year for copyright in the technological realm. The â98 Digital Millennium Copyright Act (DMCA) laid the foundations for RIAAâs cases half a decade down the line. Besides making "it a crime to circumvent anti-piracy measures built into most commercial software," the DMCA most importantly "limits internet service providers from copyright infringement liability for simply transmitting information over the internet." [22] Known as the "safe harbor provision," DMCA Title II (OCILLA) creates a "safe harbor" for internet service providers (ISPs) from being liable for content stored or transmitted via their servers as long as they take swift steps to remove the copyrighted content when asked. This Online Copyright Infringement Liability Limitation Act also gave plaintiffs the right to subpoena user information from the ISPs to carry out individual lawsuits.
As of January 2007, there are two portions of the United States code detailing domestic copyright regulations. USC Title 17 provides a comprehensive breakdown of every copyright guideline while section 2319 of Title 18 lists possible consequences for criminal infringement of a copyright. Under these laws, not everything conceived by the mind is eligible for copyright. According to chapter 1 section 102 of Title 18, the United States copyright law protects "original works of authorship fixed in any tangible medium of express." [23] This includes "literary, musical, dramatic works, pantomimes, choreographic, pictorial, graphic, sculptural works, motion pictures and other audiovisual works, sound recordings, and architectural works." [24] Ideas, not yet formulated on such "tangible mediums," thus, do not qualify. When a work is classified as copyrighted, section 106 of chapter 1 gives only the proper owner of the work the rights to reproduce, prepare derivate works, distribute, publicly perform, and publicly display the creation. In addition, these exclusive rights must be granted by the owner in order for third parties to use the copyrighted material.
When one or more exclusive rights such as the ones listed above have been breeched by an individual or a corporation, this respective party is considered to have committed a "copyright infringement." Although there are limitations to the power of these exclusive rights, such as cases where the violation has been deemed legitimate under the four conditions of "fair use" or other exceptions for special educational organizations, in most cases where the copyrighted content has been duplicated and/or distributed without the prior consent from the owner, infringement most likely occurred.
Consequences for infringement vary from case to case. The prosecution may choose to sue for measures at its discretion; however, the US Code does outline maximum and minimum sentences for different scenarios. Section 504 for Title 17 allows for the plaintiff to charge the defendant for actual and statutory monetary damages. Detailed evidence proving losses directly linked with the case is needed to recover actual monetary damages. As for statutory damages, the allowable compensation range from $200 to $150,000 per each infringed copyrighted work. If the prosecution can further prove that the defendant has used the copyrighted material either "for purposes of commercial advantage or private financial gain" or have reproduced or distributed content "which have a total value of more than $1,000," criminal charges found in section 2319 of Title 18 may apply. According to this section of US Code, if the defendant has been found in violation of copyright for personal financial gain, the maximum sentence is 5 years imprisonment for the first offense. Similar subsequent offenses carry 10 years imprisonment per offense. If the defendant has been found in violation of copyright for which the content had a total value more than $1,000, the maximum penalty is 3 years imprisonment for the first offense and 6 years for each additional offense in the future. These criminal charges are additions to monetary damages incurred from section 504 and even possible attorney fees of the plaintiffâs party from section 505 of Title 17.
Piracy Among Digital Natives
Reasons for Piracy
- Saving time & money
- Digital natives are used to having immediate access to digital media. They aren't familiar with having to go to a record store and buy the latest CD or even having to record on a VCR a favorite show -- they can get the materials almost as quickly as they come out.
- Supply & demand + youth popularity
- Method of self expression
- Curiosity & standing trends
- Weak repercussions
- Online disinhibition effect
- Anonymity
Online Piracy: The Ultimate Generation Gap
Piracy & Tech Culture
Newly developed technologies of the last decade are giving users unprecedented freedom and control over media. Since embracing novel technologies and keeping current with the latest trends are crucial to the cultural standard of digital natives, such innovations provided the foundations for today's piracy.
- Software innovations
- Fast, efficient transfer protocols
- User friendly file sharing applications
- Online advertisement system
- Software communications boom
- Hardware innovations
- The personal computer
- MP3 players
- Portable multimedia players
- Storage medium technologies
- "Hardware synergy"
At heart, below the layers of accessories and fancy gadgets, the youth generation of today are not so different from the previous generations. Your typical teenager has a rebellious streak. Such teenage mentality drives counter-mainstream adult ideologies, which incites piracy.
Repercussions
For those who download through peer-to-peer (P2P) networks, the MPAA and RIAA have brought up the many potential risks one faces when accessing these servers. In the parental resources section of the MPAA website, the organization warns about four dangers of P2P programs: âSubject users to pornography, open personal files on your home computer to strangers online, increase the risk of a computer virus, lure kids into illegally downloading movies and music, which can lead to jail time and finesâ [25].
The first three concerns the MPAA notes are typical risks users face when acquiring content through such systems. Many online hackers exploit the P2P search system for monetary gains. By analyzing the trends of high demand movies or music, these profiteers simply manipulate the file names of the viruses and malware they want to spread to match the names of popular song artists and movie titles. Average users who are unaware of these tactics often times are gullible enough to execute these masked programs without realizing the fileâs identity. Even the ever-popular P2P software Limewire admits to the existence of viruses and other harmful material on their networks. In its online FAQ, the programmers warn Limewireâs users, âif you attempt to download a virus-infected file using LimeWire, you will be vulnerable to any viruses contained in that fileâ [26].
In addition to harmful materials one can download, many of these free P2P programs are packaged with third party spyware programs that will slowly but surely retard the speed and reliability of a computer. Like the infamous AOL installation back in the day, a handful of these shareware clients come bundled with various harmful third party applications. By means of a deceptive installation wizard or simply packing other software with the executable, oblivious individuals get much more than what they originally wanted.
Finally, users face the possibility of legal consequences due to copyright infringement. Since most P2P search requests will pull up media across the whole copyright spectrum, the MPAA does not want children to get the impression certain copyrighted content can be acquired without charge. The legal consequences does not discriminate by age. From a warning to a petty fine of $200 to $150,000 and 5 years in jail, the potential cost of piracy is very real [27].
Solutions
Eliminating piracy in the foreseeable future is a next to impossible task. There will always be people seeking ways to circumvent laws for a variety of reasons. There is hope, however. Even though wiping out piracy is not feasible, reducing this theft of digital material can be accomplished.
Raising Awareness
- Getting the message across to the new generations of Digital Natives
It is human nature to want to fit in with the rest of the populace. For example, if the majority of Trevorâs peers does not condone or commit piracy, it is highly unlikely Trevor will spend Friday nights at home downloading the latest blockbuster for he will be at the movie theatre watching the film with his friends. Thus, it is necessary to embed piracyâs immoral ideologies as early as possible in the heads of rising digital natives.
Although the representatives of the entertainment industry are currently pushing massive anti-piracy educational campaigns onto the public sphere, their efforts are not enough. The facts about piracy need to be incorporated into public school curriculums across the country. High school government classes should stress the consequences of copyright infringement. Parents should take part in addressing the dangers of piracy before they teach their children how to use computers. With a solid piracy awareness educational program in place, next generations of internet users will be ready to make rational and informed decisions about electronic theft.
- Programs in place for kids in secondary schools
- Programs in place for college students
- Information sites
- Opposing viewpoints
Improve Business Strategies
Steps the software, entertainment, and gaming industries can take to adapt to the stubborn mindsets of digital natives.
- Adapting to the new digital environment
- Embrace the inevitable online music movement
- Develop better technologies to aid sales
- Providing legal, more attractive alternatives
- Reduce material costs of current physical albums
- Renew incentives to collect
- Good examples
- Apple iTunes Music Store
- The New Naspter
- BitTorrent and MPAA Join Forces [28]
The main incentive to obtain pirated files instead of purchasing them from a legitimate seller is because of the undesirable high prices of genuine media. In a study conducted by the RIAA, the consumer prices of producing a CD nearly rose 60% between the years of 1983 and 1996. Fortunately, the price of blank CDs fell 40% during this period, otherwise âaverage retail price of a CD in 1996 would have been $33.86 instead of $12.75â [29]. The RIAA notes because âthe amount of music provided on a typical CD has increased substantially, along with higher quality in terms of fidelity, durability, ease of use, and range of choices,â not to mention todayâs insanely over the top marketing strategies, the prices of production has been consistently on the rise.
This price trend also is occurring in the DVD sales industry. With the DVD player penetration rate in American households up from 23.6% in 2001 to 76.2% in 2005, DVDs are definitely on demand [30]. The average price of a DVD title, however, rose from $20.52 to $21.35 from 2001 to 2005 while the price of blank DVDs were falling lower and lower [31]. Consumers who are always hunting for deals turn to free P2P services or cheaper pirated versions of media because the real stuff is simply too expensive.
Adjust Policies & Enforcement Techniques
- Creating new policies that clarifies digital fair use
- Setting the examples (for the prosecution)
The RIAA announced in July 2003 its intent to start gathering evidence in order to sue end users for illegally downloading copyrighted content via file sharing networks. Several months later, the big day finally came. On September 8th, 2003, the RIAA issued the first 261 lawsuits in what was to become an onslaught of charges. By May of 2006, newspapers have reported "the RIAA had sued more than 182,000 individuals for illegal downloading of music." [34] Although there were several cases that were fought extensively by the defendants, on average, each suit was settled for around $3000. The Motion Pictures Association of America, an organization that serves "as the voice and advocate of the American motion picture, home video and television industries," was not far behind in its user litigation endeavor. [35] Around one year after the RIAA's announcement, the newly appointed CEO of MPAA, Dan Glickman, declared at a UCLA press conference that "the studios will begin suing online movie swappers in the next few weeks." [36] Commenting on the recording industry's pursuit of piracy, Glickman told USA Today - "we wanted to watch their progress first and have some time to evaluate options. In the short term, it caused them some problems, but long term they were helped greatly by the campaign."
Problems? Since the day the RIAA initiated its first wave of copyright infringement suits, there have been many complaints voiced by analysts over the practice of suing loyal consumers. Wharton legal studies professor Richard Shell proclaimed that the RIAA "has gone one step too far with its latest legal move. Industries have a completely different strategic relationship with customers than they do with rivals. And this sort of strategy does not play well in the court of public opinion." The questionable effectiveness of this controversial business strategy was hyped to an even higher level when some targets of the RIAA became simply ridiculous. Curious media networks, always hungry for another eye catching story, had a field day when people like Sarah Ward received her lawsuit in the mail. For some odd reason, Ward, a grandmother residing in Massachusetts was charged for downloading "hard-core rap music." [37] It turns out this wasn't the only obscure case, given that little girls and old grandpas were also part of the pool of 261 unlucky individuals hit by RIAA's first round of lawsuits. "Brianna Lahara, a twelve-year-old girl living with her single mother in public housing in New York City" and "Durwood Pickle, a 71-year-old grandfather in Texas" were both charged for downloading copyrighted content through illegal file sharing networks. [38] The profiling of stereotypically awkward individuals did not stop here. In the years following the first lawsuits, the RIAA had inspired many sardonic headlines - "RIAA drops case against mom; sues her kids", "RIAA Sues Deceased Grandmother," and "RIAA Sues Yet Another Person Without A Computer" just to list several examples. Though some of these cases did turn out to be mistakes, the majority of them actually were legitimate accusations. Nevertheless, the large majority of the populace on popular forums, blog sites, and the news media concur with Professor Shell's belief. In their opinion, chastising, ridiculing, and sometimes flat out mocking the RIAA's foolish actions made sense.
- Good examples
- Creative Commons (Policy)
- DRM (Enforcement)
Reflections
Numbers Tell the Story
- Discuss the latest trends among Digital Natives relating to how they perceive piracy
- Gender differences
- Social-economic differences
- Family influences
- Group mentality phenomenon
Other Side of the Debate
Is piracy really causing problems for the programming/entertainment industries?
- Russian teacher fined for MS piracy [39]
- Piracy in developing countries
Piracy is no doubt a huge problem overseas. Although most countries have anti-piracy legislation in place, the enforcement of these laws are not up to par with global standards. Especially in developing countries where local governments have no incentives of protecting foreign intellectual property, whole industries have been built around the concept of illegally duplicating and distributing media for individual gains. The Motion Pictures industry in 2005 claimed that there were "more than 34,000 cases of piracy and assisted law enforcement officials in conducting more than 10,500 raids. These activities resulted in the seizure of more than 34 million illegal optical discs, 55 factory optical disc production lines and 3,362 optical disc burners, as well as the initiation of more than 8,000 legal actions." [40] Despite these proactive measures, MPA still projected a sum total of more than one billion dollars in lost potential revenue for 2005 in the Asia-Pacific region alone.
While the entertainment industry frantically tries to control piracy overseas, software businesses have a lighter view on this issue. Although software piracy is no better compared to media piracy abroad, there is less concern from the corporate side. In these developing countries, the biggest competitors for legitimate software companies are open source organizations. Since, software engineers are vying to attract a larger portion of the new population to use their product, strategists have have concluded piracy may actually help companies defeat the open source movement. Take the software giant Microsoft for example. It "acknowledges that piracy sometimes helps the company establish itself in emerging markets and fend off threats from free open-source programs." [41] In countries like China and India, even though a huge portion of the population operates on counterfeit versions of Windows and unactivated versions of Office, at the end of the day they are still using Microsoft made products. If the strategy to empower both the legitimate and illegitimate user base works out as planned, when a country's economy matures in the long run, the majority of the population will be more willing to buy Microsoft's genuine software. Just look at Vietnam, "which at more than 90% has the highest piracy rate in the world, has improved from 100% in 1994. The No. 1 software firm in Vietnam: Microsoft." [42]
The debate about whether or not severe anti-piracy measures are necessary in developing countries is an hot issue, for there are good supporting arguments for both parties. The value of a piece of software varies directly with the size of its user base. Without a substantial base of users, software products cannot survive. In these developing countries where the majority of the population cannot afford many of life's luxuries, asking them to dump several hundred dollars for a copy of Windows Vista is ridiculous. But, for every pirated of Vista bought Microsoft is loosing potential revenue. So, the final question to be asked is -- constituents a potential sale?
Relevant Research
SIIA Anti-Piracy: What is Piracy?
10 Big Myths about copyright explained
The YouTube effect: HTTP traffic now eclipses P2P
Youth & Piracy
Majority of Youth Understand âCopyright,â But Many Continue To Download Illegally, 2004
Parents pick up piracy from kids
Online Piracy: The Ultimate Generation Gap
The Effects of Piracy in a University Setting
Youth & Technology
US youths use internet to create, 2005
PDF: Teen Content Creators and Consumers, 2005 [43]
Anti-Piracy
(Gaming Industry) ESA: Intellectual Property
(Movie Industry) MPAA: Anti-Piracy
(Music Industry) RIAA: Anti-Piracy
(Software & Other Content) SIAA: Anti-Piracy
Pro-Piracy
Russian teacher fined for MS piracy, 2007
Profits from Piracy: Microsoft in China
Possible Solutions
Suing Your Customers: A Winning Business Strategy?, 2003
Hong Kong enlists youth to fight piracy
Legal News
Viacom the Latest Company to Misunderstand the Internet, Jason Kolb, 2007
YouTube-Viacom Page on TopTenSources, Various Editors, 2007
Viacom Terrorizes YouTube, Cory Doctorow at Boing Boing, 2007
LA Times: Is Copying a Crime? Wellâ¦, 2006
Which Videos Are Protected? Lawmakers Get a Lesson, 2007
MPAA copyright victory is 'website killer', 2005
BitTorrent and MPAA Join Forces
Piracy stats don't add up, 2006
Indiana man jailed for selling counterfeit software on eBay
Movie Swappers Put on Notice, 2004
Poughkeepsie Online: Music Swappers Sued, 2003
Music Theft on 19 Campuses Targeted in Wave of RIAA Pre-Lawsuit Letters
In Court's View, MP3 Player is Just a 'Space Shifter', 1999
Anti-iTunes DRM demonstrations across the USA tomorrow
DRM-free iTunes Songs Have Embedded User Info
Apple, EMI Ink DRM-Free Music Plan
Legal Notes
Cornell Law School Legal Information Institute - US Code: Title 17, Copyrights
Cornell Law School Legal Information Institute - Constitution: LII