Digital Piracy: Difference between revisions
No edit summary |
|||
| (497 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
[[Portal:Digital Piracy]] | |||
= Narratives = | = Narratives = | ||
| Line 37: | Line 38: | ||
= Introduction to Piracy = | = Introduction to Piracy = | ||
[[Image:Pirate dog.jpg|thumb|300px|Pirate Dog]] | |||
In the simplest terms, piracy is obtaining materials without the proper rights of legal ownership. In a broader sense, piracy can represent a whole range of intellectual and physical robbery. Like what the traditional usage of this term suggests, the theft committed by ruthless sea barbarians in the early 1700s is analogous to the present day methods to wrongfully acquire or distribute copyrighted material. Yes, the recent surge in pirated Pirates of the Caribbean films is, least to say, ironic. | In the simplest terms, piracy is obtaining materials without the proper rights of legal ownership. In a broader sense, piracy can represent a whole range of intellectual and physical robbery. Like what the traditional usage of this term suggests, the theft committed by ruthless sea barbarians in the early 1700s is analogous to the present day methods to wrongfully acquire or distribute copyrighted material. Yes, the recent surge in pirated Pirates of the Caribbean films is, least to say, ironic. | ||
The main driving force behind the argument against piracy centers on the degree of copyright infringement. The creator of a new piece of work has exclusive rights or ownership over all individual products of labor. Exclusive rights include but are not limited to distribution, reproduction, the ability to perform and make derivatives of the original. Under United States and most foreign law, copyright infringement is the unauthorized use of any works or materials secured by copyright. Piracy impinges on the copyright ownerâs exclusive rights without a license to do so and thus is considered a form of copyright infringement. | The main driving force behind the argument against piracy centers on the degree of [http://www.digitalnative.org/Digital_piracy#Piracy_.26_Law copyright infringement]. The creator of a new piece of work has exclusive rights or ownership over all individual products of labor. Exclusive rights include, but are not limited to, distribution, reproduction, the ability to perform and make derivatives of the original. Under United States and most foreign law, copyright infringement is the unauthorized use of any works or materials secured by copyright. Piracy impinges on the copyright ownerâs exclusive rights without a license to do so and thus is considered a form of copyright infringement. | ||
Why are copyrights necessary? Copyrights and the consequences of copyright infringement not only help protect intellectual property and ownership but also benefit society as a whole. By prohibiting duplication new products and ideas for a designated period of time after creation, these laws prevent third party profiteers from stealing intellectual property and making a living from hard work of others. Copyrights provide sufficient incentives for individuals to embark on revolutionary research, make their discoveries, and present their own creations | Why are copyrights necessary? Copyrights and the consequences of copyright infringement not only help protect [http://www.digitalnative.org/Digital_piracy#Piracy_.26_Law intellectual property] and ownership but also benefit society as a whole. By prohibiting duplication of new products and ideas for a designated period of time after creation, these laws prevent third party profiteers from stealing intellectual property and making a living from the hard work of others. Copyrights provide sufficient incentives for individuals to embark on revolutionary research, make their discoveries, and present their own creations without having to worry about ownership issues. These laws promote society's scientific and intellectual progress while piracy works as the counterforce. | ||
Currently, the piracy problem spans many corporate sectors. The MPAA, RIAA, ESA, and SIAA representing the movie, music, gaming, and software industries respectively have all taken drastic measures to cope with the repercussions from illegal sharing of their clientsâ copyrighted works. Besides publishing annual damage reports that rave about the millions upon billions of lost profit and issuing pre-litigation notices to | Currently, the piracy problem spans many corporate sectors. The MPAA, RIAA, ESA, and SIAA, representing the movie, music, gaming, and software industries respectively, have all taken drastic measures to cope with the repercussions from illegal sharing of their clientsâ copyrighted works. Besides publishing annual damage reports that rave about the millions upon billions of lost profit and issuing pre-litigation notices to known violators, industries have begun collaborating with educational companies to bring piracy awareness into schools. | ||
Although some critics of these so-called âprofit seekingâ businesses frown upon the use of educational programs designed by paid business partners, the piracy-ridden industries are targeting the right demographics. As studies conducted by third party researchers show, up and coming generations of | Although some critics of these so-called âprofit seekingâ businesses frown upon the use of educational programs designed by paid business partners, the piracy-ridden industries are targeting the right demographics. [http://www.techdirt.com/articles/20060830/193527.shtml] [http://www.techdirt.com/articles/20031023/1349248.shtml] As studies conducted by third party researchers show, up and coming generations of digital natives are more prone than any other age group to experiment with and actually commit piracy. In a 2006 study, L.E.K. consulting group found the typical internet pirate is a male between the ages of 16 and 24. They reported, â44 percent of MPA company losses in the U.S. are attributable to college students.â [http://www.mpaa.org/2006_05_03leksumm.pdf] Growing up in an environment immersed with different technological facets, digital natives confront the copyright issue much earlier in childhood. More and more of our youth are desensitized about piracy and intellectual property rights at younger ages. In a recent PEW study, researchers found that around half of the young students interviewed were not concerned with downloading and sharing of copyrighted content for gratis. Teens who download music online agree, âitâs unrealistic to expect people to self-regulate and avoid free downloading and file-sharing altogether.â [http://www.pewinternet.org/PPF/r/113/press_release.asp] | ||
In a recent PEW study, researchers found that around half of the young students interviewed were not concerned with downloading and sharing of copyrighted content for gratis. Teens who download music online agree, âitâs unrealistic to expect people to self-regulate and avoid free downloading and file-sharing altogether.â [http://www.pewinternet.org/PPF/r/113/press_release.asp] | |||
= Overview = | = Overview = | ||
| Line 55: | Line 57: | ||
== Classifications == | == Classifications == | ||
Since the piracy problem is pertinent across many fields, the definition | Since the piracy problem is pertinent across many fields, the definition of this term and possible classifications have been extremely controversial over the years. While members of the justice system used piracy and theft almost interchangeably, people on the other side of the aisle view this practice as a grand exaggeration of reality. To them, it is unfair to compare downloading a song with real life thievery, or in this case, the carnage of 17th century sea "pirates." Even the organizations representing the large media and software industries do not have standard, unified definition for what they are fighting. MPAA defines piracy as "a serious federal offense." As for the different kinds of piracy, MPAA only mentions "internet piracy of movies, DVD copying, illegal sales and theatrical camcording." To the ISAA, "making additional copies, or loading the software onto more than one machine, may violate copyright law and be considered piracy." RIAA defines piracy as "the illegal duplication and distribution of sound recordings." Each organization is representing its respective industry, only showing pertinent consumers mere pieces of the puzzle. A definitive, yet agreeable definition for piracy and an universal way to classify the many faces of this issue are needed. | ||
Piracy can be classified into two categories - digital and physical. Digital piracy is the illegal duplication and distribution of copyrighted content via electronic means. While the usage of online (peer-to-peer) P2P networks is the most pervasive outlet of digital piracy, hosting copyrighted files such as MP3s, movies, and software on web servers, uploading copyrighted media on video sharing sites, and even simpler ways of distribution such as via email or instant messaging are also considered illegal digital piracy. Similar to digital piracy, physical piracy | Piracy can be classified into two categories - digital and physical. Digital piracy is the illegal duplication and distribution of copyrighted content via electronic means. While the usage of online (peer-to-peer) P2P networks is the most pervasive outlet of digital piracy, hosting copyrighted files such as MP3s, movies, and software on web servers, uploading copyrighted media on video sharing sites, and even simpler ways of distribution such as via email or instant messaging are also considered illegal digital piracy. Similar to digital piracy, physical piracy involves the illegal duplication and distribution of works, but in physical form. Digital media can be illegally burned onto mediums such as CDs, DVDs and sold for a fraction of the retail price. Books, newspapers, magazines, course packs, journals, research and reports can also be duplicated in physical form and distributed. In fact, the MPAA reports, for 2005 "62 percent of the $6.1 billion loss result from piracy of hard goods such as DVDs, 38 percent from internet piracy." [http://www.mpaa.org/2006_05_03leksumm.pdf] Physical piracy of media and other forms of content are much more pervasive on a global scale. This method of copyright infringement can be further classified into individual license, corporate to end-user, reseller and distributor violations. | ||
Categorizing piracy by methodology only answers the "how" question. "Why" people pirate can be grouped by a measurement of intentionality. Kids and adults alike have different reasons for why they choose to download from P2P networks or buy counterfeit media. Some, however, are quite unaware of their actions while others are completely oblivious between what is right and wrong. In a recent ZDNet report on UK businesses running Windows, "Microsoft would not put a figure on how much it loses from unintentional piracy, but said that while 85 percent of UK small businesses run Microsoft software, only 15 percent pay for it." [http://news.zdnet.co.uk/itmanagement/0,1000000308,2095743,00.htm] All of this, of course hinges on intentionality. Individuals who are completely aware of their actions are considered director facilitators of digital or physical piracy. From the acquirers of prerelease content, to the online intermediaries, from the distributors to the customers, this group includes people anywhere on the piracy chain. Intentional piracy usually involves some sort of monetary gain at the loss of the copyright holder. Individuals somewhat aware of piracy are usually consumers of counterfeit content. They understand to an extent what they are doing is wrong but choose to go ahead with it for various reasons such as personal enjoyment or curiosity. | Categorizing piracy by methodology only answers the "how" question. "Why" people pirate can be grouped by a measurement of intentionality. Kids and adults alike have different reasons for why they choose to download from P2P networks or buy counterfeit media. Some, however, are quite unaware of their actions while others are completely oblivious between what is right and wrong. In a recent ZDNet report on UK businesses running Windows, "Microsoft would not put a figure on how much it loses from unintentional piracy, but said that while 85 percent of UK small businesses run Microsoft software, only 15 percent pay for it." [http://news.zdnet.co.uk/itmanagement/0,1000000308,2095743,00.htm] All of this, of course, hinges on intentionality. Individuals who are completely aware of their actions are considered director facilitators of digital or physical piracy. From the acquirers of prerelease content, to the online intermediaries, from the distributors to the customers, this group includes people anywhere on the piracy chain. Intentional piracy usually involves some sort of monetary gain at the loss of the copyright holder. Individuals somewhat aware of piracy are usually consumers of counterfeit content. They understand to an extent what they are doing is wrong but choose to go ahead with it for various reasons such as personal enjoyment or curiosity. Educating these indirect facilitators the wrongs of piracy is the recording industries' best chance at curbing this problem. Finally, consumers completely unaware of piracy are usually those who are victims of counterfeit scammers or those whose computer or personal network has been hijacked to illegally contribute copyrighted material. | ||
== Origins == | == Origins == | ||
In the last millennium, there were only a few landmark innovations affecting the dissemination of media content. Gutenbergâs invention of the printing press in 1450 allowed for easy and inexpensive duplication of paper works. With the assistance of moveable type, productivity of scribes (now hired machine workers) increased exponentially. As profit margins shot through the roof, the publishing industry was born. In the late 1970s, early 1980s, the introduction of the Sony Walkman gave humans the capability to record audio while the videocassette system did the same for video. In the 1990s, the popularization of CD/DVD optical disk technology gave birth to the new era of digital recording. The 21st century ushered in the acceptance of new digital mediums. Combined with the enormous success of the internet, computers and newly developed network protocols took information sharing to a new level. Each one of these new "machines" included a "mechanism" for which a certain "media" was affected. Each innovation established or revolutionized an industry. Each provided a faster, even better way to spread information. Each, however, brought with it intellectual property issues, for each forced or is forcing policy makers to amend copyright standards. | In the last millennium, there were only a few landmark innovations affecting the dissemination of media content. Gutenbergâs invention of the printing press in 1450 allowed for easy and inexpensive duplication of paper works. With the assistance of moveable type, productivity of scribes (now hired machine workers) increased exponentially. As profit margins shot through the roof, the publishing industry was born. In the late 1970s, early 1980s, the introduction of the Sony Walkman gave humans the capability to record audio while the videocassette system did the same for video. In the 1990s, the popularization of CD/DVD optical disk technology gave birth to the new era of digital recording. The 21st century ushered in the acceptance of new digital mediums. Combined with the enormous success of the internet, computers and newly developed network protocols took information sharing to a new level. Each one of these new "machines" included a "mechanism" for which a certain "media" was affected. Each innovation established or revolutionized an industry. Each provided a faster, even better way to spread information. Each, however, brought with it intellectual property issues, for each forced or is forcing policy makers to amend copyright standards. | ||
{| border="1" | |||
<center> | |||
{| border="1" cellpadding="5" cellspacing="0" | |||
!Media | |||
!Mechanism | |||
!Machine | |||
|- | |- | ||
| | |Paper | ||
| | |Movable Type Publishing | ||
| | |Printing Press | ||
|- | |- | ||
| | |Cassette/VHS Tape | ||
|Magnetic Recording | |||
|Walkman/VHS Machine | |||
|- | |- | ||
| | |CD/DVD | ||
|Optical Disk Recording | |||
|CD/DVD Recorder | |||
|- | |- | ||
|Standardized Computer Files | |||
|P2P/Torrent Networks | |||
|Standardized Computer Files | |Personal Computer | ||
|} | |} | ||
</center> | |||
[[Image: Shawn Fanning.jpg|thumb|right|200px|Shawn Fanning]] | |||
On June 1st, 1999, Shawn Fanning, a student from Northeastern University, released what would be called "the godfather of peer to peer programs" â Napster. At that time, although there were other technologies facilitating the sharing of media, "Napster specialized exclusively in music ... and presented a user-friendly interface." [http://en.wikipedia.org/w/index.php?title=Napster&oldid=97019220] Soon after being launched, this easy to use, cost-free program became wildly popular because everyday computer users had enough basic technical knowledge to contribute to the file sharing movement. Napster's sensation, however, was short lived. Its "facilitation of transferring copyrighted material raised the ire of the Recording Industry Association of America (RIAA), which almost immediately â in December 1999 â filed a lawsuit against the popular service." [http://en.wikipedia.org/w/index.php?title=Napster&oldid=97019220] Because Fanning earned profits through advertisements and operated the project via a client-server protocol with a centralized file list, the RIAA push for intentional copyright infringement ultimately succeeded. | On June 1st, 1999, Shawn Fanning, a student from Northeastern University, released what would be called "the godfather of peer to peer programs" â Napster. At that time, although there were other technologies facilitating the sharing of media, "Napster specialized exclusively in music ... and presented a user-friendly interface." [http://en.wikipedia.org/w/index.php?title=Napster&oldid=97019220] Soon after being launched, this easy to use, cost-free program became wildly popular because everyday computer users had enough basic technical knowledge to contribute to the file sharing movement. Napster's sensation, however, was short lived. Its "facilitation of transferring copyrighted material raised the ire of the Recording Industry Association of America (RIAA), which almost immediately â in December 1999 â filed a lawsuit against the popular service." [http://en.wikipedia.org/w/index.php?title=Napster&oldid=97019220] Because Fanning earned profits through advertisements and operated the project via a client-server protocol with a centralized file list, the RIAA push for intentional copyright infringement ultimately succeeded. | ||
Napster's immense success planted the seed for today's P2P debacle. On one hand, this innovation sparked the countermovement by the RIAA and other recording companies to curtail infringement. On the other hand, Fanning's concept of dedicated media distribution GUI programs inspired next generations of P2P coders to create iterations of the Napster design even more insusceptible to the current copyright laws. The 1986 "Betamax case" allowed Sony to manufacture VCRs "because the devices were sold for legitimate purposes and had substantial non-infringing uses" (Betamax). In the cases brought up against these new P2P projects, even though the prosecution was successful in proving the Betamax argument invalid, the victory in the courtroom only fueled the rapid spawning of new P2P projects. " | Napster's immense success planted the seed for today's P2P debacle. On one hand, this innovation sparked the countermovement by the RIAA and other recording companies to curtail infringement. On the other hand, Fanning's concept of dedicated media distribution GUI programs inspired next generations of P2P coders to create iterations of the Napster design even more insusceptible to the current copyright laws. The 1986 "Betamax case" allowed Sony to manufacture VCRs "because the devices were sold for legitimate purposes and had substantial non-infringing uses" (Betamax). In the cases brought up against these new P2P projects, even though the prosecution was successful in proving the Betamax argument invalid, the victory in the courtroom only fueled the rapid spawning of new P2P projects. | ||
In March 2001, the FastTrack protocol allowed for a more distributed network without a centralized sever. Faster computers in the network now has the ability to become supernodes, or machines with server-like capabilities to help out slower clients. Newer P2P programs like KaZaa, Grokster, and iMesh successfully implemented this protocol and gained millions of users. Two years later, "FastTrack was the most popular file sharing network, being mainly used for the exchange of music mp3 files. Popular features of FastTrack are the ability to resume interrupted downloads and to simultaneously download segments of one file from multiple peers." [http://en.wikipedia.org/wiki/FastTrack] During the same decade, true distributed network protocols such as the open source Gnutella and eDonkey 2000 also caught on with mainstream P2P file sharers. Likewise spawning other P2P clients, Limewire, Morpheus, and eDonkey. Compared to Napster, these newer networks were able to attain higher maximum speeds because every client also had the capability to share files. Also, since the copyrighted material were stored on individual computers, with the proper disclaimers, the P2P client companies were able to brush off the majority of legal accusations. | |||
The acceptance of the mp3 format in the mid 1990s allowed users to compress songs into several megabyte files, all of which were easily distributable throughout the digital world. In the early 2000s, DivX, a newly developed video compression codec did the same for video. As more households switched over to broadband internet, the ability to transfer large files finally became plausible. However, even with DivXâs help, typical compressed DVD rips still hovered above 600 MB. Since traditional P2P protocols could not handle the new bandwidth demand efficiently, a newer distributive protocol called BitTorrent was quickly adopted. | |||
[[Image: Bram Cohen.jpg|thumb|left|200px|Bram Cohen]] | |||
BitTorrent was developed by Bram Cohen in 2001. By splitting large files into sizable pieces, data can be widely distributed and shared "without the original distributor incurring the entire costs of hardware, hosting and bandwidth resources." [http://en.wikipedia.org/wiki/BitTorrent] For a client to download additional data, one must supply requested chunks of the larger file to newer recipients. Cohen's implementation not only proved to be incredibly efficient, but also managed to exploit a legal loophole. While the initial releases of the BitTorrent system depended on trackers to operate, these servers answered the requests clients only by giving them the <i>location</i> of other computers who are concurrently sharing the same sought after file. Since tracker servers did not host any of the copyrighted content, the prosecution had a harder time shutting down these organizations. BitTorrent soon grew to become the sharing mechanism of choice. | |||
Digital piracy only constitutes a portion of the whole picture. True, today's extensive counterfeit CD/DVD markets are largely fueled by the established presence of piracy in the digital realm. Resellers and distributors usually get the content to copy from online sources. But, the history of physical piracy can be traced back to the days of floppy disks and cassette tapes. In 1964, the Philips company brought compact audio cassette technology to the United States. Although there were other magnetic cartridge technologies available, Philip's decision to license the format for free made compact cassettes the most accepted recording medium during this time. [http://en.wikipedia.org/wiki/Compact_Cassette] In the 1970s and 1980s, cheaper multi-track recording mechanisms for artists and the consumer compact cassette boom prolonged the popularity of this new medium. The trading of these recordable cassettes among music fans across the U.S. and U.K. via the mail was dubbed "cassette culture." [http://en.wikipedia.org/wiki/Cassette_culture] Acceptance of floppy disk technology starting from the early 1980s provided users an easy way to copy computer related files. Copyrighted computer software and games especially could be easily duplicated using these disks. Of course, anti-piracy campaigns also started as a reaction to these new fads. The British Phonographic Industry, a music trade group in the 1980s, launched an anti-piracy campaign with the slogan "Home Taping Is Killing Music." Similar to the RIAA's concerns today, the BPI was afraid that the rise of a new recording medium (in their case, the cassette tapes) would hurt legitimate record sales. In 1992, the Software Publishers Association produced an anti-piracy campaign centered around a video commercial called "Don't Copy That Floppy." [http://www.archive.org/details/dontcopythatfloppy] | |||
== Current Methodologies == | == Current Methodologies == | ||
''' | Advent of the internet and the rapid increase of personal computers means more people than ever before have the capability to share information online. Though these advancements give users unprecedented access to the world's data, enforcing proper copyright restrictions while allowing justifiable sharing freedoms have not been attained. Thus, many have pointed to these new technologies as the facilitators of so-called "digital piracy." Today, users employ many different applications and services to illegally transfer copyrighted material. Factoring intentionality out of the equation, this section aims to introduce these online trade tools. | ||
=== Local sources === | |||
<i>Highlights: Live Messenger, E-mail, YouSendIt, MyTunes</i> | |||
The easiest and often times fastest way a person obtains copyrighted materials is from local, direct sources. Friends, family members, classmates -- an individual's immediate relations are commonly the people one asks when in need of a song, copy of a TV show, or a recent movie. Popular chat software like Microsoft's Live Messenger, AOL's IM, even Yahoo Messenger all support some form of a file transferring mechanism allowing these exchanges to happen. A few clicks and a potentially copyrighted file is on its way. Thanks to the recent milestones in the email industry, ever increasing account quotas and attachment size restrictions removed the barriers for sending decent sized files via traditional email. As of June 2007, popular services like Google's GMail and Windows Live Hotmail offer 2 GB of free space. Yahoo Mail even went as far as offering unlimited storage. [http://help.yahoo.com/l/us/yahoo/mail/yahoomail/tools/tools-08.html] For larger files such as bundled music albums and films that exceed the maximum attachment caps, users turn to dedicated file uploading services like YouSendIt. After the file is uploaded, a notification is sent to the intended recipient with a retrieval URL. Recently, programs like MyTunes managed exploit sharing capabilities of the widely used music player iTunes, allowing users on the same local network to share their music libraries. All in all, in these proposed cases, the user is obtaining material from known, local sources on an personal basis via the internet. | |||
=== P2P networks === | |||
<i>Highlights: Kazaa, eMule, LimeWire, the original Napster</i> | |||
Peer-to-peer (P2P) networks comprise of computers across the internet linked together with special file sharing protocols implemented by different P2P programs. Popular protocols vary by two qualities: centralization and structure. Centralized P2P network protocols, like one used by the first version of Napster, rely on dedicated severs to record client information and store pieces of the shared data. Newer, decentralized P2P networks like FastTrack (used by popular P2P programs like KaZaa and Grokster) depend on individual clients to relay information; each computer on the network can act both as the sender and receiver of traffic. The way in which computers are connected inside of a P2P network determines its structure. When a client joins unstructured network, the computer only has access to files shared by known sources, barring access from the rest of the computers. Trying to locate a rare file is a lot harder because of the connection limitations. Structured P2P networks have streamlined methodologies for unique searches. Using technologies like distributed hash tables (DHT), it is incredibly efficient to find a file on the other side of the web. The beauty of P2P protocols and client/server networks relies on its user base. The combined processing power and bandwidth capabilities of these networked computers provide unprecedented levels of digital resources. With enough contributers, people can easily find and quickly download every piece of digitized work ever made. | |||
The original Napster was the first P2P program to achieve mainstream status. In 2001, the final ruling of the case A&M Records, Inc. v. Napster, Inc. found this file sharing giant liable for illegal "contributory infringement of plaintiff record company's copyrights." [http://en.wikipedia.org/wiki/A_%26_M_Records%2C_Inc._v._Napster%2C_Inc.] Even though Napster was consider a P2P program, it worked in a far more centralized way. The A&M Records' lawyers had incontestable evidence showing the defendant's role in facilitating copyright infringement, for clients depended on servers to talked to other clients. After Napster's demise, other P2P applications using newer, more efficient P2P protocols found their place in this industry. Popular programs like KaZaa (FastTrack protocol), eMule (eMule 2000 protocol), Limewire (Gnutella protocol) employed more decentralized and more structured ways of data exchange. These iterations of the original design, thus in a sense, are considered true peer-to-peer technologies. | |||
=== Torrent networks: Torrent indexers, trackers & clients === | |||
<i>Highlights: ThePirateBay, MiniNova, µTorrent, Azureus</i> | |||
The Torrent network is another file sharing alternative. BitTorrent was developed by programmer Bram Cohen during the summer of 2001. [http://en.wikipedia.org/wiki/Bram_Cohen] The main quality that sets BitTorrent apart from other P2P technologies is its ability to efficiently transfer large amounts of data quickly and efficiently. When a user downloads something via traditional P2P means, most of the data usually comes from a couple of individuals who are sharing the same completed file. Unlike KaZaa, eMule, and LimeWire, all data on the torrent network are broken up into small pieces and simultaneously shared by huge pools of users. Each individual's Torrent client has the ability to connect to hundreds of other clients who are sharing pieces of the same sought after file. The relationship between clients are symbiotic. In order for computers to download pieces of a file, they too have to share similar pieces with other computers. This forced reciprocity and piece-wise sharing technique provides noticeable boosts productivity and speed. A 2004 report from CacheLogic claimed "Online movie trading is skyrocketing, but onetime leader Kazaa is tumbling in use" Andrew Parker, CacheLogic's founder and chief technology officer said, "The overall level of file sharing has increased. Users have migrated from Kazaa onto BitTorrent." [http://news.com.com/Survey%3A+Movie-swapping+up%2C+Kazaa+down/2100-1025_3-5267992.html?tag=nefd.top] Because computer users are increasingly downloading larger files like movies and software, in the first few years of this decade, P2P traffic on the internet surpassed all other types of data. [http://www.readwriteweb.com/archives/p2p_growth_trend_watch.php] | |||
There are three integral components of the Torrent system; each provides a specific function that is uniquely independent of the others. Torrent indexers like ThePirateBay and Mininova stores databases full of ".torrent" files which contain the locations of both public and private torrent trackers. These tracker servers help client computers loaded with compatible torrent programs like µTorrent and Azureus connect with other candidates from all across the web. While anyone can download from public trackers, there are exclusive invite-only private trackers that provide even faster connections. Clients act as individual nodes on the network; their main job is to communicate with other clients to trade copied pieces of the requested file until all the pieces are downloaded. An user commences a download by loading a small ".torrent" file retrieved from a torrent index site into the torrent client. The client then communicates to the given server(s) and retrieves a list of IP addresses where pieces of the same file are being hosted. In case a server is down or not responding, clients also have the ability to use DHT (Distributed Hash Table) and PE (Peer Exchange) technology to find the locations of other clients without the assistance of trackers. | |||
=== Warez networks === | |||
<i>Highlights: Astalavista.box.sk, Cracks.ms</i> | |||
Warez is technical slang that stands for a broad spectrum of online counterfeit content. Ripped computer programs, music, movies, books and any copyrighted content published in a organized but illegal fashion can be considered Warez. Underground organizations called "release groups" operate on a minute by minute basis in constant search for new, unreleased music albums and features film to push on the web. In a 2005 Wired Magazine article, Erik Malinowski describes the five step "trickle-down file-sharing" system. [http://www.wired.com/wired/archive/13.01/topsite.html?pg=4] He divides up the piracy chain into the insider, the packager, the distributor, the couriers, and the public. According to Malinowski, majority of the high quality content that reaches the internet prematurely originate from insiders. Appointed screeners, workers at optical disk manufacturing plants, and moles within the production industry feed unreleased copies of albums, films, or computer programs to these release groups. In return, these people are usually provided with monetary contributions and access to terabytes of high quality media stored on the release groups' servers. Once a copy of unreleased media content gets into a release group, packagers working non-stop to encode and compress the content into smaller sized, easily transferable files. The content is then stamped with the release group's name or logo, zipped with a NFO file or (information file) giving credit to a release group, and passed on to the distributor. On the digital end, most release groups have relationships with "topsites" or "highly secretive sites on the top of the online distribution pyramid." [http://www.wired.com/wired/archive/13.01/topsite.html?pg=4] When a topsite operator publicizes the file on its networks, couriers immediately begin pushing the package to more accessible P2P and Torrent networks for the public to access. On the physical end, release groups can simultaneously sell copies of unreleased content to disc piracy manufacturers all around the globe. Immediately, people in the counterfeit disc business will begin mass producing copied CDs/DVDs to sell to audiences on the streets. | |||
Even though most insiders and people associated with release groups do not know their acquaintances in person, members of these select organizations develop strong bonds with each other, for getting a new piece of media into the public takes teamwork and precision. The race to be first at offering the latest copyrighted content stirs up immense amounts of competition among release groups. Once a copy of an publicly unavailable content reaches the web, the value of such file or files drops close to zero. Over the years these underground networks of moes, hackers, crackers, and rippers were dubbed "The Scene." [http://www.wired.com/wired/archive/13.01/topsite.html] | |||
Besides producing ripped films and other media, release groups also have been known for cracking licensed software. Instead of insiders, the these groups depend on software crackers to supply the goods. Reverse engineering programmers spend their days trying to figure out how to defeat embedded license protection mechanisms. Crack/CD-key aggregators like Astalavista and Cracks.ms store hundreds upon thousands of key generators, patches, and other forms of cracks for a wide range of software. Users who can't find a prepackaged release from BitTorrent often resort to this manual search method. Though, one must wade through a lot of pornographic content, spyware exploits, and virus ridden files before finding anything useful. For amateur computer users, the risk of endangering their computers' integrity by exposing them to these malicious sites is too great; thus, they turn to traditional legal means. | |||
=== Web mediums: Media sharing & aggregation === | |||
[[Image:Broadband traffic.jpg|thumb|476px|right|Ellacoya Networks June 2007 Report]] | |||
<i>Highlights: Tv-Links.co.uk, PeekVid, YouTube, Veoh</i> | |||
With help from YouTube, online video sharing and streaming websites have caught on as top accessed online services among mainstream internet users. The analysis of internet traffic has always been a great way to measure the popularity of different protocols. For example, typical web browsing will amount to HTTP traffic. (When browsing the internet, notice websites usually have the letters âHTTPâ in front of the URLs.) Likewise, accessing FTP servers will generate FTP traffic, using P2P networks such as KaZaa or BitTorrent will generate P2P traffic, and so forth. For the first few years of the twentieth century, P2P data has dwarfed other forms of transferred traffic largely due to the immense popularity of music and video sharing. In a 2007 study, however, Ellacoya found âfor the first time in four years, P2P traffic finally fell behind HTTP. Chalk it up to YouTube and other Internet video sharing sites. The surge in HTTP traffic is largely a surge in the use of streaming media, mostly video.â Specializing in IP service control, Elacoya said, âBreaking down the HTTP traffic, only 45 percent is used to pull down traditional web pages with text and images. The rest is mostly made up of streaming video (36 percent) and streaming audio (five percent). YouTube alone has grown so big that it now accounts for 20 percent of all HTTP traffic, or more than half of all HTTP streaming video." [http://arstechnica.com/news.ars/post/20070619-the-youtube-effect-http-traffic-now-eclipses-p2p.html] | |||
YouTubeâs popularity comes with a cost. "New web sites are making it even easier for anyone who can click a mouse to access copyrighted content across the net. You no longer need to know your way around IRC or understand what a .torrent file is. Instead you can just stream them over any number of social video sites." [http://www.techcrunch.com/2007/07/11/top-50-videos-google-is-pirating/] Since there are little to no physical restrictions that prevent users from uploading copyrighted content, individuals often times believe sharing an episode of Family Guy or Friends on YouTube is just. While some companies like CBS allow segments of their popular shows to be streamed online as means of free advertising, other TV stations and media networks retaliated in full force, taking Google's YouTube and Google Video to court. Since the start of the lawsuits two years ago, Google has "agreed to remove more than 100,000 video clips produced by Viacom properties, including MTV Networks, Comedy Central, BET and VH-1, according to a YouTube statement." [http://news.com.com/2100-1026_3-6155771.html] Of course without an extensive filtering system, people often find ways to sneak copyrighted content onto these services. A recent report titled "Is Google Promoting Video Piracy?" form the NLPC (National Legal and Policy Center) found "Google Video hosted apparently pirated copies of current major films as "Sicko" and "Evan Almighty." Both were posted without the permission or knowledge of the copyright owners. This follows a lawsuit against Google by media giant Viacom seeking $1 Billion in damages." [http://www.nlpc.org/view.asp?action=viewArticle&aid=2082] As of June 12th, 2007, Google is preparing to test it's video screen technology that will hopefully flag potential copyrighted material once they are uploaded. [http://www.techcrunch.com/2007/06/12/youtube-prepares-to-test-copyright-screening-technology/] | |||
Other online video hosting companies like Veoh, VideoEgg, DailyMotion, GoFish are also stepping up their anti-piracy awareness in fear of lawsuits. Because of this, pieces of copyrighted content are scattered in random locations across the net. Video aggregation sites like the infamous PeekVid and recently popular TV-Links.co.uk compile these hard to find links into one location. In return for these services, these webmasters earn revenue from the pervasive amount of advertisements on their websites. | |||
=== Conventional means: FTP, Webservers, IRC, USENET === | |||
Owners of web and FTP servers have the ability to publish copyrighted content accessible by the internet audience. Since most of these servers are rented by individuals for personal or small business use, these methods of distribution are much slower than dedicated file hosts such as YouSendIt. If something popular is discovered to be hosted on a non-password protected server, the surge in bandwidth during a short period of time can easily cause a system crash. Most of these uploaded copyrighted content stored for either backup or limited sharing among known relations. Unfortunately, search bots or page crawlers such as Googlebot, frequently indexes pages containing these files. There are certain searches techniques one can use to pull up copyrighted content such as songs, movies, or TV shows. Using IRC (Instant Relay Chat) Channels and USENETs to acquire copyrighted content still can be done, but definitely have fallen below main stream usage. Even though both methodologies prove to be extremely fast ways to download files, both require above average computer know-how and connections within online communities that share such content. | |||
<center> | |||
{| border="0" | |||
|+ | |||
=== Gallery: Digital Methodologies === | |||
! [[Image:Digital astalavista.box.sk.jpg|thumb|175px|center|Astalavista.box.sk]] | |||
! [[Image:Digital cracks.ms.jpg|thumb|175px|center|Cracks.ms]] | |||
! [[Image:Digital emule.jpg|thumb|175px|center|eMule]] | |||
! [[Image:Digital kazaa.jpg|thumb|175px|center|KaZaa]] | |||
|- | |||
! [[Image:Digital ftp.jpg|thumb|175px|center|FTP]] | |||
! [[Image:Digital limewire.png|thumb|175px|center|LimeWire]] | |||
! [[Image:Digital msn.jpg|thumb|175px|center|MSN Messenger]] | |||
! [[Image:Digital mytunes.png|thumb|175px|center|MyTunes]] | |||
|- | |||
! [[Image:Digital napster.png|thumb|175px|center|The Original Napster]] | |||
! [[Image:Digital peekvid.jpg|thumb|175px|center|PeekVid]] | |||
! [[Image:Digital thepiratebay.jpg|thumb|175px|center|The Pirate Bay]] | |||
! [[Image:Digital tv-links.co.uk.jpg|thumb|175px|center|TV-Links]] | |||
|- | |||
! [[Image:Digital utorrent.png|thumb|175px|center|µTorrent]] | |||
! [[Image:Digital veoh.jpg|thumb|175px|center|Veoh]] | |||
! [[Image:Digital yousendit.jpg|thumb|175px|center|YouSendIt]] | |||
! [[Image:Digital youtube.jpg|thumb|175px|center|YouTube]] | |||
|} | |||
</center> | |||
By understanding methodologies | |||
Every copyable form of media, from mass printing back in the 15th century to the cassette tape technology in the second half of the 20th century, was illegally exploited for profit. Before the popularization of digital formats and the increased accessibility of the internet, illegal distribution of physical copyrighted material was the prevalent form of piracy. Today's global physical piracy can be categorized into three sections: individual license violation, corporate to end-user violation, and reseller/distributor violation. | |||
=== Individual license violation === | |||
The simplest form of physical piracy is committed by the everyday computer user. Factoring intentionality out of the equation, these transactions involve little to no net profit and is pertinent to all kinds of media. People who do not understand or do not care to understand licensing for a specific media product oftentimes overuse or misuse their given rights. Of course, different forms of media have different user agreements. A list of things one can and cannot do with a purchased DVD differs from what one agrees to when installing a computer program. True, some of these rights are innate. The ability to watch a DVD or start Microsoft Word whenever you want comes without question prepackaged in the original deal. After all, one is paying money for ownership. | |||
Many restrictions concerning duplication and distribution, however, are not explicitly outlined in the perplexing user agreements. For example, installing single copy of a popular software on multiple computers is a perfect example of license overuse. The SIAA dubbed this behavior "softlifting." [http://www.siia.net/piracy/whatis.asp] Other forms of manipulative techniques for personal financial benefit are listed as follows. Falsifying one's identity to obtain additional upgrade features or manufacturer discounts, using academic or non-retail software for commercial purposes, copying/distributing licensed software and locked media with immediate relations are all considered individual license piracy. Because these interactions are on a local level, authorities rarely bother to trace this form of physical piracy. | |||
Camcording is a huge issue the movie industry has to face on a daily basis. The term refers to the process where individuals capture featured films with portable recording devices. According to the MPAA, "ninety percent of pirated copies of movies are still playing in theaters. Once a camcorded copy is made, illegal movies often appear online within hours or days of a movie premiere." [http://mpaa.org/piracy_theatrical_cam.asp] Recently, stronger legislation have been put in place to discourage people from committing this crime. President Bush in 2005 signed the Family Entertainment and Copyright Act into law. It "makes camcording in a theater a federal felony and establishes new penalties for pirating works that have not yet been released commercially. First-time violators can be sentenced from up to three and five years in prison, and fined up to $250,000 for these kinds of crimes." [http://mpaa.org/piracy_theatrical_cam.asp] While some of the amateur camcorder pirates keep these recordings for at home viewing pleasure, most confront the risk for profit or other forms of personal gain. As mentioned before in a previous section, if the moles inside the movie industry do not leak the screener before a specific movie hits theaters, the release groups than depend solely on these lower quality camcorder versions to publish on the internet. These pirates also sell these recordings to "illicit source labs where they are illegally duplicated, packaged and prepared for sale on the black market, then distributed to bootleg dealers across the country and overseas. Consequently, the film appears in street markets around the world just days after the US theatrical release and well before its international debut." [http://mpaa.org/piracy_theatrical_cam.asp] In this case, these camcorder pirates can also be categorized in the reseller/distributer group because they are also a vital part of that physical piracy chain. | |||
=== Corporate to end-user === | |||
Corporate to end-user piracy involves the misuse of software licensing within businesses and other organizations, such as schools, universities, and government funded programs. Unlike individual license piracy, the misuse of software licenses in this case are backed by the administrations representing these respective institutions. In the process of increasing productivity by installing better software while keeping costs to a minimum, the higher ups sometimes overlook the obvious legality issues behind allowing the proliferation of intangible things like computer programs. | |||
There are three main forms of corporate piracy. The first form involves installing single-licensed software on multiple computers. Like individual license overuse, when company IT departments hands out free copies of Office 2007 or Adobe Photoshop to their employees, the end-users are benefiting at the loss of Microsoft and Adobe. Many organizations chose to buy volume licensing for expensive software titles. Because it is fiscally inefficient to purchase a copy of software for every single employee, companies oftentimes use keyed servers & keyed programs to reduce costs. This way, only a set amount of licenses needs to be bought for a bigger pool of users; however, thanks to the management of the keyserver, only that set number of users can access this program at any given time. Client-server overuse occurs when this keyserver fails to control the number of people who can access a program at the same time. Finally, hard-disk loading means illegally installing licensed software on computers' hard drives before they are given to employees or sold to costumers. Again, in this case, the end-user is put in a situation where they are unaware that their usage of certain computer programs is unlawful. | |||
Because corporate to end-user piracy improves profit margins (or increases losses from the perspective of the programmers) at a much larger scale than the illegal individual sharing of copyrighted content, the software companies have more incentives to seek compensations. Anti-piracy organizations specializing in hunting down software pirates such as the SIIA (Software & Information Industry Association) and the BSA (Business Software Alliance) have been assisting today's most prominent software companies like Apple, Microsoft, and Adobe fight this and other types of piracy for quite some time now. While both the SIIA and BSA publish reports concerning the latest piracy statistics worldwide, the SIIA even has elaborate online form for company whistle-blowers to report the misuse of software licensing within their organizations. There is even a up to $1 million reward depending on how the pervasiveness of piracy. [http://www.siia.net/piracy/report_software.asp] | |||
=== Reseller and distributor === | |||
Over a period of 18 months, LEK surveyed 20,600 movie consumers from 22 countries and found "62 percent of the $6.1 billion loss (reported by the movie industry) result from piracy of hard goods such as DVDs, 38 percent from internet piracy." [http://www.mpaa.org/2006_05_03leksumm.pdf] Despite recent telecommunication advances and increasing numbers of broadband computer users, compared to online digital piracy, physical piracy still plays a larger role in the global piracy market. The reason for this phenomenon is largely due to the well built infrastructure and well engraved ideologies in select regions of the world. People in countries like Armenia, Moldova, and Azerbaijan, where over 90% of the software are obtained illegally, do not believe in paying for software. [http://w3.bsa.org/globalstudy//upload/2007-Piracy-Study-Findings.pdf] Lifetime habits, after all, are hard to change. Of course, larger piracy-ridden countries like China, India, and most of Southeast Asia also play huge roles in fostering the continual growth of this illegal act. Resellers and distributors of copyrighted material contribute to the largest portion of today's worldwide physical piracy. | |||
[[Image:Auctioning off cdkeys.jpg|thumb|right|200px|Case Study #1]] | |||
Unlike corporate and individual piracy, resellers and distributors work in closely knit, well built networks of sellers and buyers, all of whom have the ultimate profit seeking goal in mind. In a way, these collections of physical pirates analogous to the previously discussed online release groups. With speed and style in mind, these people deliver top notch replications of the latest unreleased content in a matter of hours after something is leaked. Reseller and distributor physical piracy can apply to all different forms of media. From software to movies, from music to games, all digitally formatted content have the risk of being physically copied and sold. Selling copied or counterfeit software for a reduced price as street vendors or in counterfeit stores, running unlicensed movie theaters or rental facilities, illegal direct resell and auctions of improperly licensed media are all considered physical piracy. | |||
'''Case Study #1: What is wrong with this picture?''' | |||
In this eBay auction, the seller is attempting to sell a valid Windows OEM license. He states in the description of the auction "the computer died but your winning bid the license can live on. Since the original system died, this Windows XP Home Edition license can be activated on another system. This is an auction for one license key only. No software is included. It is branded Toshiba but will work on any system. You may need to call Microsoft's 800 number to activate." Whether or not the seller made a genuine offer is besides the fact, for when one posts the a readable picture of the serial number, what is there left to "purchase"? $39.95 is a heavy price to pay when one can just copy down the number. Surprisingly, there were 12 bids on this auction when this screen shot was taken. | |||
<center> | |||
{| border="0" | |||
|+ | |||
=== Gallery: Physical Methodologies === | |||
! [[Image:Physical auction.jpg|thumb|175px|center|Illegal Online Auctions]] | |||
! [[Image:Physical corp.to.end.user.jpg|thumb|175px|center|Corp to End User Violation]] | |||
! [[Image:Physical individual.license.jpg|thumb|175px|center|Individual License Violation]] | |||
! [[Image:Physical reseller.1.jpg|thumb|175px|center|Reseller]] | |||
|- | |||
! [[Image:Physical reseller.2.jpg|thumb|175px|center|Reseller]] | |||
! [[Image:Physical reseller.3.jpg|thumb|175px|center|Reseller]] | |||
|} | |||
</center> | |||
By understanding methodologies behind these commonly used utilities and practices, we can have a better understanding of piracy's role in the lives of digital natives. | |||
= Piracy & Law = | = Piracy & Law = | ||
The chain reaction that instigated copyright regulations dates back to the fifteenth century. Gutenbergâs printing press marked the beginning of a new era of information distribution. True, this device facilitated the mass production and dissemination of human knowledge; however, it also carried repercussions. The formerly tedious task of duplication by hand was sped up to a | The chain reaction that instigated copyright regulations dates back to the fifteenth century. Gutenbergâs printing press marked the beginning of a new era of information distribution. True, this device facilitated the mass production and dissemination of human knowledge; however, it also carried repercussions. The formerly tedious task of duplication by hand was sped up to a rate that warranted tighter controls. When this technology arrived in England, the "need for protection of printed works was inevitable." [http://www.open-spaces.com/article-v2n1-loren.php] In 1710, the English Parliament passed the first official law concerning copyrights. The Statue of Anne "established the principles of authorsâ ownership of copyright and a fixed term of protection of copyrighted works." [http://www.arl.org/info/frn/copy/timeline.html] Almost three hundred years have elapsed since this passing of this statue. Although some ideological remnants still remain, todayâs US copyright law "has been revised to broaden the scope of copyright, to change the term of copyright protection, and to address new technologies." [http://www.arl.org/info/frn/copy/timeline.html] | ||
Present day US copyright regulations stemmed from the first days of nationhood. When Americaâs founding fathers composed the United States Constitution in 1787, they gave Congress the power "to promote the progress of science and useful arts, by securing for limited times to authors and inventors the exclusive right to their respective writings and discoveries." [http://www.law.cornell.edu/constitution/constitution.articlei.html] This line of text in Article I, section 8 bestowed upon the State fundamental rights to a monopoly over the copyright industry. It was the governmentâs job to asset, distribute, and control all copyrights. "The First Congress implemented the copyright provision of the U.S. Constitution in 1790," modeled quite similarly to the Statue of Anne. [http://www.arl.org/info/frn/copy/timeline.html] Since then there had been three major revisions which occurred in the years 1870, 1909, and 1976. | Present day US copyright regulations stemmed from the first days of nationhood. When Americaâs founding fathers composed the United States Constitution in 1787, they gave Congress the power "to promote the progress of science and useful arts, by securing for limited times to authors and inventors the exclusive right to their respective writings and discoveries." [http://www.law.cornell.edu/constitution/constitution.articlei.html] This line of text in Article I, section 8 bestowed upon the State fundamental rights to a monopoly over the copyright industry. It was the governmentâs job to asset, distribute, and control all copyrights. "The First Congress implemented the copyright provision of the U.S. Constitution in 1790," modeled quite similarly to the Statue of Anne. [http://www.arl.org/info/frn/copy/timeline.html] Since then there had been three major revisions which occurred in the years 1870, 1909, and 1976. | ||
With arrival of the digital age, Congress amended the copyright act to "prohibit commercial lending of computer software" in 1990. [http://www.arl.org/info/frn/copy/timeline.html] This revision did not solve all the problems, for technology was evolving at a rapid pace. Computer savvy individuals were finding ways to bypass government copyright regulations. For example, under copyright laws up to the No Electronic Theft (NET) Act of 1997, people who intentionally distributed copyrighted software without receiving monetary benefits could not be prosecuted. The NET Act amended this loophole. [http://www.gseis.ucla.edu/iclp/hr2265.html] Following NET, 1998 was also a big year for copyright in the technological realm. The â98 Digital Millennium Copyright Act (DMCA) laid the foundations for RIAAâs cases half a decade down the line. Besides making "it a crime to circumvent anti-piracy measures built into most commercial software," the DMCA most importantly "limits internet service providers from copyright infringement liability for simply transmitting information over the internet." [http://www.gseis.ucla.edu/iclp/dmca1.htm] Known as the "safe harbor provision," DMCA Title II (OCILLA) creates a "safe harbor" for internet service providers (ISPs) from being liable for content stored or transmitted via their servers as long as they take swift steps to remove the copyrighted content when asked. This Online Copyright Infringement Liability Limitation Act also gave plaintiffs the right to subpoena user information from the ISPs to carry out individual lawsuits. | |||
As of January 2007, there are two portions of the United States code detailing domestic copyright regulations. USC Title 17 provides a comprehensive breakdown of every copyright guideline while section 2319 of Title 18 lists possible consequences for criminal infringement of a copyright. Under these laws, not everything conceived by the mind is eligible for copyright. According to chapter 1 section 102 of Title 18, the United States copyright law protects "original works of authorship fixed in any tangible medium of express." [http://www.law.cornell.edu/uscode/html/uscode17/usc_sup_01_17.html] This includes "literary, musical, dramatic works, pantomimes, choreographic, pictorial, graphic, sculptural works, motion pictures and other audiovisual works, sound recordings, and architectural works." [http://www.law.cornell.edu/uscode/html/uscode17/usc_sup_01_17.html] Ideas, not yet formulated on such "tangible mediums," thus, do not qualify. When a work is classified as copyrighted, section 106 of chapter 1 gives only the proper owner of the work the rights to reproduce, prepare derivate works, distribute, publicly perform, and publicly display the creation. In addition, these exclusive rights must be granted by the owner in order for third parties to use the copyrighted material. | As of January 2007, there are two portions of the United States code detailing domestic copyright regulations. USC Title 17 provides a comprehensive breakdown of every copyright guideline while section 2319 of Title 18 lists possible consequences for criminal infringement of a copyright. Under these laws, not everything conceived by the mind is eligible for copyright. According to chapter 1 section 102 of Title 18, the United States copyright law protects "original works of authorship fixed in any tangible medium of express." [http://www.law.cornell.edu/uscode/html/uscode17/usc_sup_01_17.html] This includes "literary, musical, dramatic works, pantomimes, choreographic, pictorial, graphic, sculptural works, motion pictures and other audiovisual works, sound recordings, and architectural works." [http://www.law.cornell.edu/uscode/html/uscode17/usc_sup_01_17.html] Ideas, not yet formulated on such "tangible mediums," thus, do not qualify. When a work is classified as copyrighted, section 106 of chapter 1 gives only the proper owner of the work the rights to reproduce, prepare derivate works, distribute, publicly perform, and publicly display the creation. In addition, these exclusive rights must be granted by the owner in order for third parties to use the copyrighted material. | ||
| Line 138: | Line 251: | ||
When one or more exclusive rights such as the ones listed above have been breeched by an individual or a corporation, this respective party is considered to have committed a "copyright infringement." Although there are limitations to the power of these exclusive rights, such as cases where the violation has been deemed legitimate under the four conditions of "fair use" or other exceptions for special educational organizations, in most cases where the copyrighted content has been duplicated and/or distributed without the prior consent from the owner, infringement most likely occurred. | When one or more exclusive rights such as the ones listed above have been breeched by an individual or a corporation, this respective party is considered to have committed a "copyright infringement." Although there are limitations to the power of these exclusive rights, such as cases where the violation has been deemed legitimate under the four conditions of "fair use" or other exceptions for special educational organizations, in most cases where the copyrighted content has been duplicated and/or distributed without the prior consent from the owner, infringement most likely occurred. | ||
Consequences for infringement vary from case to case. | Consequences for infringement vary from case to case. The prosecution may choose to sue for measures at its discretion; however, the US Code does outline maximum and minimum sentences for different scenarios. Section 504 for Title 17 allows for the plaintiff to charge the defendant for actual and statutory monetary damages. Detailed evidence proving losses directly linked with the case is needed to recover actual monetary damages. As for statutory damages, the allowable compensation range from $200 to $150,000 per each infringed copyrighted work. If the prosecution can further prove that the defendant has used the copyrighted material either "for purposes of commercial advantage or private financial gain" or have reproduced or distributed content "which have a total value of more than $1,000," criminal charges found in section 2319 of Title 18 may apply. According to this section of US Code, if the defendant has been found in violation of copyright for personal financial gain, the maximum sentence is 5 years imprisonment for the first offense. Similar subsequent offenses carry 10 years imprisonment per offense. If the defendant has been found in violation of copyright for which the content had a total value more than $1,000, the maximum penalty is 3 years imprisonment for the first offense and 6 years for each additional offense in the future. These criminal charges are additions to monetary damages incurred from section 504 and even possible attorney fees of the plaintiffâs party from section 505 of Title 17. | ||
== Fair Use == | |||
The United States Fair use doctrine is a method of defense that can be employed when an individual is being accused of copyright infringement. Fair use allows for legal incorporation of copyrighted content in a new piece of work without prior agreement from the original author. [http://www.chillingeffects.org/fairuse/faq.cgi] United States Code, Section 107, states usage of another's work "for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright." However, because this law can be applied to situations with drastically different circumstances, the ruling of a specific case is hard to discern. To solve this problem, Section 107 "Limitations of exclusive rights" lays down four factors to be considered when judging the validity of Fair use: "the purpose and character of the use, including whether such use is of a commercial nature or is for nonprofit educational purposes; the nature of the copyrighted work; the amount and substantiality of the portion used in relation to the copyrighted work as a whole; and the effect of the use upon the potential market for or value of the copyrighted work." [http://www.law.cornell.edu/uscode/html/uscode17/usc_sec_17_00000107----000-.html] The judge presiding over a case involving Fair use must weigh these four factors in a balancing test. | |||
<center> | |||
{| border="1" cellpadding="5" cellspacing="0" | |||
!Fair use | |||
!Copyright infringement | |||
|- | |||
|Advances public knowledge | |||
|Fails to do so | |||
|- | |||
|Transformative use | |||
|Less transformative use | |||
|- | |||
|Little to no commercial use | |||
|Commercial use | |||
|- | |||
|More creative, less purely factual | |||
|Less creative, more purely factual | |||
|- | |||
|Copying published works | |||
|Copying unpublished works | |||
|- | |||
|Small portions of the work copied | |||
|Huge portions of the work copied | |||
|- | |||
|Derivative work does not harm potential market | |||
|Derivative work harms potential market | |||
|} | |||
</center> | |||
There are four main factors that determine whether or not a case can qualify as fair use. Factor one -- "purpose and character" states, if the usage of a work advances public knowledge, is very transformative, and has little to no commercial purposes, then it is easier to argue for fair use. Factor two -- "nature of the copyright work" states, more creative, less purely factual usages of published works have stronger protection against copyright infringement. Copying unpublished works without the author's consent usually weakens the defendant's case for fair use. Factor three -- "amount and sustantiality of portion defendant used" is more straightforward than the first two factors. The larger the portion of copyrighted work used, the more prone the ruling will be in favor of copyright infringement and vice versa. The final factor -- "effect of defendant's use on potential market of copyrighted work" plays the most important role in determining the right to Fair use. If the derivative work endangers the original work's potential market opportunities, then the court will most likely be in favor of the prosecution. Criticism or parodies that may put the original work in a bad light are allowed even though it might damage the potential market. [http://www.chillingeffects.org/fairuse/faq.cgi] | |||
= Piracy Among Digital Natives = | = Piracy Among Digital Natives = | ||
| Line 150: | Line 299: | ||
* Curiosity & standing trends | * Curiosity & standing trends | ||
* Weak repercussions | * Weak repercussions | ||
* Online disinhibition effect | |||
* Anonymity | |||
[http://www.foxnews.com/story/0,2933,94960,00.html Online Piracy: The Ultimate Generation Gap, 2003] | |||
* FOX News report on youth piracy | |||
Newly developed technologies of the last decade are giving users unprecedented freedom and control over media. Since embracing novel technologies and keeping current with the latest trends are crucial to the cultural standard of | "The generation before us had to pay for music," said recent college grad Joshua, 24, of New York City. "Now you have no reason to purchase the music or movie in physical form. Everything is digital." | ||
"Kids really don't care," said college freshman Ben, 18, of Upper Nyack, N.Y. "We all copy music and download movies because the chances of them cracking down on us specifically are slim." | |||
"The lawsuits are both futile and counterproductive," said Fred von Lohmann, senior staff attorney at the Electronic Frontier Foundation. "Not only will they not stop file sharing, but they'll alienate customers." | |||
"We're hopeful we haven't lost this generation," said Bob Kruger, enforcement vice president of the Business Software Alliance, which fights software piracy. | |||
"It makes me feel kind of bad â like, 'oh no, I'm doing something illegal,'" said Melissa, the Florida teen. "I'm probably downloading a little less." | |||
[http://www.law.uchicago.edu/Lawecon/WkngPprs_151-175/162.ls.file-swapping.pdf Charismatic Code, Social Norms, and the Emergence of Cooperation on the File-Swapping Networks] | |||
* Strahilevitz's analysis of P2P networks | |||
"Virtually everyone who participates in one of the file-swapping networks is breaking the law in the process. Ordinarily, people are unlikely to trust lawbreakers, especially anonymous lawbreakers. Yet a remarkable sense of trust permeates these networks. ... [I]t is possible to observe significant levels of cooperative behavior, very little by way of destructive behavior, and substantial trust among the anonymous users of these networks. Furthermore, the networks have survived and thrived largely because of their users' dogged willingness to engage in unlawful activities." | |||
Charismatic code-- "a technology that presents each member of a community with a distorted picture of his fellow community members by magnifying cooperative behavior and masking uncooperative behavior." | |||
* "the applications harness the actual members of the community to become actors for norm enforcement purposes by magnifying the actions of those who cooperate and masking the actions of those who do not" | |||
* "the applications act as a substitute for the community of actors and enforcers, inculcating in their users those norms most likely to lead to the success and expansion of the networks" | |||
* "the applications act as a substitute for the community of actors and enforcers, inculcating in their users those norms most likely to lead to the success and expansion of the networks" | |||
Distorted image-- (Gnutella network) "Charismatic code is the primary tool in that effort. Because of the way the networks are structured, the actions of those who share content are quite visible, while the actions of those who do not share content are virtually invisible. ... The architecture of the networks is such that although many users on the networks do not share, the networks create an appearance that sharing is the norm. This dynamic - the magnified visibility of sharers and the invisibility of non-sharers - exists on every successful file-swapping application I have seen." | |||
"By the same token, these affinities normalize file-swapping: Members of the file-swapping networks stop being identified as 'rogue software pirates' and start being identified as 'people who, like me, have excellent musical taste.'" | |||
Reciprocity-- "Technologies that magnify cooperative behavior and mask uncooperative behavior can succeed by tapping into deeply held social norms. In this instance, the file-swapping networks have been successful in large part because they have managed to tap into internalized norms of reciprocity. ... The networks' creators are drawing upon reciprocal intuitions that their users are likely to possess. Once again, the software is designed to exploit those intuitions." | |||
* MusicCity and KaZaa's upload/download page | |||
* Forced reciprocity implementation in 2001 | |||
== Piracy & Tech Culture == | |||
Newly developed technologies of the last decade are giving users unprecedented freedom and control over media. Since embracing novel technologies and keeping current with the latest trends are crucial to the cultural standard of digital natives, such innovations provided the foundations for today's piracy. | |||
* Software innovations | * Software innovations | ||
| Line 167: | Line 355: | ||
** "Hardware synergy" | ** "Hardware synergy" | ||
At heart, below the layers of accessories and fancy gadgets, the youth generation of | At heart, below the layers of accessories and fancy gadgets, the youth generation of today are not so different from the previous generations. Your typical teenager has a rebellious streak. Such teenage mentality drives counter-mainstream adult ideologies, which incites piracy. | ||
[http://web.lexis-nexis.com.ezp2.harvard.edu/universe/document?_m=d520576e58ef5bf18134cf4f3ffe3834&_docnum=1&wchp=dGLbVlb-zSkVA&_md5=643a0a82adff308c7207a0ab3b00cb00 We're a pirate nation, 2007] | |||
* Newspaper article concerning Canadian piracy | |||
"Hollywood can help itself by doing business with iTunes Canada and providing a library of legal content to download. That, and some stronger legislation from Ottawa, would go a long way to keeping us honest." | |||
"Based on a survey polling wired Canadians in February, we not only bootleg directly from the screen, but we also like to download pirated booty - a lot. A whopping 93% of those downloading movies in this country are doing so illegally. And it's not just tech-savvy teenagers. Nearly 50% are over age 46." | |||
"And pinning it on in-theater theft seems to fly in the face of a 2003 study done by AT&T, which concluded that Hollywood was prone to insider attacks, which resulted in leaked screener copies of 77% of 312 movies studied." | |||
"It's commonly known that Montreal is a hot spot," says Dewolde. "In Canada there's no law against camcordering, so it's hard to stop these guys. The worst they can get charged with is trespassing. It's a huge issue." | |||
"At first blush, it looks as if Canadians are more liable to piracy than their counterparts in the U.S.," says Phil Dwyer in a release. "In reality, many of these illegal downloads are taking place because of the lack of legal alternatives. The market is more mature in the U.S., and the experience there shows that if you give consumers a legal, convenient and fairly priced alternative to piracy, the majority will use it." | |||
"We're pretty polite pirates. Give us a legal way to download movies and you'll see a sea change. No doubt many people have looked longingly at the growth of content on iTunes before downloading that torrent." | |||
[http://www.newstatesman.com/pdf/CounterfeitingCulture2006.pdf Counterfeiting Culture, 2006] | |||
* Transcript of a round table discussion about counterfeiting in general | |||
Roz Groome - "What has been highlighted are the different strains of harm that are going on. Physical harm, financial harm and social harm - the connection between counterfeiting, piracy, organised crime and other antisocial behaviour. Then also, there is economic harm for the industries and to the Treasury, because no tax flows back on counterfeit goods. People need to realise that they are not just lining the pockets of the rich and famous. For every musical hit there are ten failures and most musicians do not earn what Robbie Williams earns. In terms of creativity, and in terms of ensuring that consumers pay for the product, it is important to ensure that the money flows back to the people who are responsible for creating it and many of those people will not be rich and famous." | |||
Michelle Childs - "Jo has done some interesting research about the motivation of consumers to purchase counterfeit goods. It raises some interesting competition questions. When you are talking about motivation to buy fake DVDs, 56 per cent of respondents bought them because they wanted to see a film as quickly as possible. So perhaps consumers are giving market signals. Perhaps they are saying that some of the old ways of doing things, such as having windows for releasing DVDs in different markets or only releasing music in certain formats, are not what they want and are not going to work." | |||
Jo Bryce - "The answer might be to fill that market gap, rather than to get tough with criminal sanctions." | |||
"If anything, they seemed to believe that the rip-off that was taking place was in the price charged for legitimate goods, rather than the counterfeit ones." | |||
Mike Smith - "The counterfeit manufacturing and duplicating of CDs and DVDs and selling them through markets is highly visible. But on the internet, your children, 17 or 18 year olds, are swapping files and it is not so freely visible." | |||
Mike Smith - "These young people are music enthusiasts, so it is ironic that, by swapping and downloading these music files, they are hacking into the profits of the record companies and taking money that should, by rights, be paid to the songwriters and artists." | |||
Mike Smith - "There is an argument that the future may perhaps not consist of record sales, except in a more niche, particularly high-fidelity market. Essentially music may be seen as a commodity, as a utility, as something that you get streamed to your mobile phone and that you can access constantly, wherever you go. Maybe you will pay a monthly subscription and get your music constantly coming into your life, so that it almost seems like a free commodity. What the record companies need to work out is how the people that are still manufacturing and marketing most of that music also manage to get paid for it - how our artists get paid and the people writing the songs get paid." | |||
Mike Smith - "No. So there is a degree of education to be done. There is also, to a degree, an acknowledgement that we are trying to turn back the tide and we cannot; itâs too late. We need to acknowledge that this is possibly the future and we need to adapt our business practices to reflect that." | |||
Roz Groome - "They will not, but I tell you who is concerned: their parents. We have conducted a massive litigation campaign against egregious uploaders. These are not people downloading, they are uploading. They are behaving like mini free retailers. They are making available thousands of files to millions of people, constantly. Everything is available on filesharing software; everything is out there. I have spoken to the parents and they are horrified. They have copied their CD collections on to their computers to enjoy them, to put them on their iPods or whatever. Then their children have come home from school and downloaded some file-sharing software on to the family computer system, which has then made available to the world their entire CD collection. Incidentally, it is not just their CDs but anything that happens to be in their shared drive. This can include the family photographs, the Expedia receipts; I have seen bank account details, it is all there. That is where consumer education needs to come in. The people doing this need to see the harm it is causing." | |||
Jeff Randall - "Once you can access music for free, people assume it is free. They do not think it through and they do not really care. That would be my view. It is a terribly cynical view, but the music industry, clearly, is facing that problem because that is what people are doing." | |||
Mike Smith - "The music industry has to adapt in order to survive. What we are trying to do with BPI is legitimate protection of our copyrights. We have to do that, but the world is changing dramatically, and the way that a record company gets its revenues is not going to be reliant solely upon sales of records. We are going to have to become music companies, not record companies, and we may come to look upon records as being a loss leader." | |||
Mike Smith - "All this could be a positive force. The internet could be the best thing that ever happened to the music industry." | |||
== Repercussions == | == Repercussions == | ||
| Line 177: | Line 409: | ||
In addition to harmful materials one can download, many of these free P2P programs are packaged with third party spyware programs that will slowly but surely retard the speed and reliability of a computer. Like the infamous AOL installation back in the day, a handful of these shareware clients come bundled with various harmful third party applications. By means of a deceptive installation wizard or simply packing other software with the executable, oblivious individuals get much more than what they originally wanted. | In addition to harmful materials one can download, many of these free P2P programs are packaged with third party spyware programs that will slowly but surely retard the speed and reliability of a computer. Like the infamous AOL installation back in the day, a handful of these shareware clients come bundled with various harmful third party applications. By means of a deceptive installation wizard or simply packing other software with the executable, oblivious individuals get much more than what they originally wanted. | ||
Finally, users face the possibility of legal consequences due to copyright infringement. Since most P2P search requests will pull up media across the whole copyright spectrum, the MPAA does not want children get the impression certain copyrighted content can be acquired without charge | Finally, users face the possibility of legal consequences due to copyright infringement. Since most P2P search requests will pull up media across the whole copyright spectrum, the MPAA does not want children to get the impression certain copyrighted content can be acquired without charge. The legal consequences does not discriminate by age. From a warning to a petty fine of $200 to $150,000 and 5 years in jail, the potential cost of piracy is very real [http://www.law.cornell.edu/uscode/html/uscode17/usc_sup_01_17.html]. | ||
= Solutions = | = Solutions = | ||
Eliminating piracy in the foreseeable future is a next to impossible task. There will always be people seeking ways to circumvent laws | Eliminating piracy in the foreseeable future is a next to impossible task. There will always be people seeking ways to circumvent laws for a variety of reasons. There is hope, however. Even though wiping out piracy is not feasible, reducing this theft of digital material can be accomplished. | ||
== | == Raising Awareness == | ||
* Getting the message across to the new generations of Digital Natives | * Getting the message across to the new generations of Digital Natives | ||
It is human nature to want to fit in with the rest of the populace. For example, if the majority of Trevorâs peers does not condone or commit piracy, it is highly unlikely Trevor will spend Friday nights at home downloading the latest blockbuster for he will be at the movie theatre watching the film with his friends. Thus, it | It is human nature to want to fit in with the rest of the populace. For example, if the majority of Trevorâs peers does not condone or commit piracy, it is highly unlikely Trevor will spend Friday nights at home downloading the latest blockbuster for he will be at the movie theatre watching the film with his friends. Thus, it is necessary to embed piracyâs immoral ideologies as early as possible in the heads of rising digital natives. | ||
Although the representatives of the entertainment industry are currently pushing massive anti-piracy educational campaigns onto the public sphere, their efforts are not enough. The facts about piracy need to be incorporated into public school curriculums across the country. High school government classes should stress the consequences of copyright infringement. Parents should take part in addressing the dangers of piracy before they teach their children how to use computers. With a solid piracy awareness educational program in place, | Although the representatives of the entertainment industry are currently pushing massive anti-piracy educational campaigns onto the public sphere, their efforts are not enough. The facts about piracy need to be incorporated into public school curriculums across the country. High school government classes should stress the consequences of copyright infringement. Parents should take part in addressing the dangers of piracy before they teach their children how to use computers. With a solid piracy awareness educational program in place, next generations of internet users will be ready to make rational and informed decisions about electronic theft. | ||
* Programs in place for kids in secondary schools | * Programs in place for kids in secondary schools | ||
| Line 198: | Line 430: | ||
* Programs in place for college students | * Programs in place for college students | ||
** [http://www.campusdownloading.com/ Campus Downloading] | ** [http://www.campusdownloading.com/ Campus Downloading] | ||
* | * Other information sources | ||
** [http://www.microsoft.com/protect/family/activities/pirating.mspx Microsoft] | ** [http://www.microsoft.com/protect/family/activities/pirating.mspx Microsoft] | ||
** [http://www.wiredsafety.org/resources/pdf/musicdownloads_parryguide.pdf WiredSafety.org, from Parent's Guide to Protecting Your Children in Cyberspace] | |||
* Opposing viewpoints | * Opposing viewpoints | ||
** [http://www.projectopus.com/node/5730 RIAA partnership with iSafe, a dangerous step] | ** [http://www.projectopus.com/node/5730 RIAA partnership with iSafe, a dangerous step] | ||
| Line 210: | Line 443: | ||
* Adapting to the new digital environment | * Adapting to the new digital environment | ||
** Embrace the inevitable online music movement | ** Embrace the inevitable online music movement | ||
** Develop better technologies to aid sales | ** Develop better technologies to aid sales | ||
| Line 219: | Line 451: | ||
The main incentive to obtain pirated files instead of purchasing them from a legitimate seller is because of the undesirable high prices of genuine media. In a study conducted by the RIAA, the consumer prices of producing a CD nearly rose 60% between the years of 1983 and 1996. Fortunately, the price of blank CDs fell 40% during this period, otherwise âaverage retail price of a CD in 1996 would have been $33.86 instead of $12.75â [http://www.riaa.com/news/marketingdata/cost.asp]. The RIAA notes because âthe amount of music provided on a typical CD has increased substantially, along with higher quality in terms of fidelity, durability, ease of use, and range of choices,â not to mention todayâs insanely over the top marketing strategies, the prices of production has been consistently on the rise. | The main incentive to obtain pirated files instead of purchasing them from a legitimate seller is because of the undesirable high prices of genuine media. In a study conducted by the RIAA, the consumer prices of producing a CD nearly rose 60% between the years of 1983 and 1996. Fortunately, the price of blank CDs fell 40% during this period, otherwise âaverage retail price of a CD in 1996 would have been $33.86 instead of $12.75â [http://www.riaa.com/news/marketingdata/cost.asp]. The RIAA notes because âthe amount of music provided on a typical CD has increased substantially, along with higher quality in terms of fidelity, durability, ease of use, and range of choices,â not to mention todayâs insanely over the top marketing strategies, the prices of production has been consistently on the rise. | ||
This price trend also is occurring in the DVD sales industry. With the DVD player penetration rate in American households up from 23.6% in 2001 to 76.2% in 2005, DVDs are definitely on demand [http://mpaa.org/researchStatistics.asp]. The average price of a DVD title, however, rose from $20.52 to $21.35 from 2001 to 2005 while the price of blank DVDs were falling lower and lower [http://mpaa.org/researchStatistics.asp]. | This price trend also is occurring in the DVD sales industry. With the DVD player penetration rate in American households up from 23.6% in 2001 to 76.2% in 2005, DVDs are definitely on demand [http://mpaa.org/researchStatistics.asp]. The average price of a DVD title, however, rose from $20.52 to $21.35 from 2001 to 2005 while the price of blank DVDs were falling lower and lower [http://mpaa.org/researchStatistics.asp]. Consumers who are always hunting for deals turn to free P2P services or cheaper pirated versions of media because the real stuff is simply too expensive. | ||
* Good examples | |||
** Apple iTunes Music Store | |||
** The New Naspter | |||
** ''BitTorrent and MPAA Join Forces'' [http://www.slyck.com/story1006.html] | |||
== Adjust Enforcement Techniques == | |||
''Parts of this section were adapted from [[User:Cfang|Chen Fang]]'s freshmen seminar paper.'' | |||
The RIAA announced in July 2003 its intent to start gathering evidence in order to sue end users for illegally downloading copyrighted content via file sharing networks. Several months later, the big day finally came. On September 8th, 2003, the RIAA issued the first 261 lawsuits in what was to become an onslaught of charges. By May of 2006, newspapers have reported "the RIAA had sued more than 182,000 individuals for illegal downloading of music." [http://www.poughkeepsiejournal.com/apps/pbcs.dll/article?AID=/20060905/LIFE/60905008] Although there were several cases that were fought extensively by the defendants, on average, each suit was settled for around $3000. The Motion Pictures Association of America, an organization that serves "as the voice and advocate of the American motion picture, home video and television industries," was not far behind in its user litigation endeavor. [http://mpaa.org/AboutUs.asp] Around one year after the RIAA's announcement, the newly appointed CEO of MPAA, Dan Glickman, declared at a UCLA press conference that "the studios will begin suing online movie swappers in the next few weeks." [http://www.usatoday.com/money/media/2004-11-05-glickman_x.htm] Commenting on the recording industry's pursuit of piracy, Glickman told USA Today - "we wanted to watch their progress first and have some time to evaluate options. In the short term, it caused them some problems, but long term they were helped greatly by the campaign." | |||
Problems? Since the day the RIAA initiated its first wave of copyright infringement suits, there have been many complaints voiced by analysts over the practice of suing loyal consumers. Wharton legal studies professor Richard Shell proclaimed that the RIAA "has gone one step too far with its latest legal move. Industries have a completely different strategic relationship with customers than they do with rivals. And this sort of strategy does not play well in the court of public opinion." The questionable effectiveness of this controversial business strategy was hyped to an even higher level when some targets of the RIAA became simply ridiculous. Curious media networks, always hungry for another eye catching story, had a field day when people like Sarah Ward received her lawsuit in the mail. For some odd reason, Ward, a grandmother residing in Massachusetts was charged for downloading "hard-core rap music." [http://www.eff.org/IP/P2P/RIAAatTWO_FINAL.pdf] It turns out this wasn't the only obscure case, given that little girls and old grandpas were also part of the pool of 261 unlucky individuals hit by RIAA's first round of lawsuits. "Brianna Lahara, a twelve-year-old girl living with her single mother in public housing in New York City" and "Durwood Pickle, a 71-year-old grandfather in Texas" were both charged for downloading copyrighted content through illegal file sharing networks. [http://www.eff.org/IP/P2P/RIAAatTWO_FINAL.pdf] The profiling of stereotypically awkward individuals did not stop here. In the years following the first lawsuits, the RIAA had inspired many sardonic headlines - "RIAA drops case against mom; sues her kids", "RIAA Sues Deceased Grandmother," and "RIAA Sues Yet Another Person Without A Computer" just to list several examples. Though some of these cases did turn out to be mistakes, the majority of them actually were legitimate accusations. Nevertheless, the large majority of the populace on popular forums, blog sites, and the news media concur with Professor Shell's belief. In their opinion, chastising, ridiculing, and sometimes flat out mocking the RIAA's foolish actions made sense. | |||
* Setting the examples (for the prosecution) | * Setting the examples (for the prosecution) | ||
** Sue illiterate sympathizers and root release groups | ** Sue illiterate sympathizers and root release groups | ||
| Line 230: | Line 472: | ||
** Keep an open mind & avoid being greedy | ** Keep an open mind & avoid being greedy | ||
*** ''Piracy stats don't add up'' [http://australianit.news.com.au/story/0,24897,20713160-15306,00.html] | *** ''Piracy stats don't add up'' [http://australianit.news.com.au/story/0,24897,20713160-15306,00.html] | ||
=== Setting Examples === | |||
A moderate level of user litigation theoretically is beneficial to the recording industry. However, the question of who should be sued is still left to be determined. Is it right to sue grandpas, grandmas, and little kids? Is it fair for the recording industry to issue the same settlement amount to a computer amateur who shared several media files and a computer guru who finally got caught? Contrary to popular belief, litigation of "innocent" little kids is in fact the right thing to do. Logically, this might not make sense, but if observed from a grander economic perspective, prosecuting downloaders who are sympathetic to the recording industries is the right way to go. | |||
Currently, the RIAA has been known to mainly target uploaders or "individuals who were allowing others to copy music files from their shared folders." [http://www.eff.org/IP/P2P/RIAAatTWO_FINAL.pdf] The piracy awareness materials published by the MPAA have also suggested the movie industry is following somewhat the same policy. In a short video clip documenting what MPAA calls "the Piracy Avalanche," the narrator concludes with the following sentence: "By eliminating topsites, the Motion Picture Association is targeting Internet piracy at its source and putting a lock on the trigger of illegal downloading and distribution of copyrighted material worldwide." [http://mpaa.org/researchStatistics] "Topsites" according to the MPAA are centralized distribution centers where the chain of piracy starts. In their opinion, if these initial outlets of pirated material are taken down, then online movie piracy would be reduced a great extent. Although this hypothesis may be true, the execution of the plan is too far-fetched. The effort needed by the MPAA to terminate a topsite is far greater than the effort needed by a single computer-adept person to launch services in another location. Only with the full cooperation of governments around the world, will this proposal be successful. | |||
In addition to the implausibility of targeting piracy at its deepest roots, the idea of suing domestic high uploaders also does not make sense. The RIAA claims that piracy "costs the music industry more than 300 million dollars a year domestically." [http://www.riaa.com] Although no one knows how this number is estimated, one fact needs to be clarified. From an economics point of view, the recording industry is only losing money when a user who originally intended to buy legal media forgoes this process to download illegally. A computer guru who never spent a single dime on the recording industry in his or her life technically does not count in this losses figure. Therefore, it is unwise for the MPAA and the RIAA to simply concentrate on people who upload a lot. To these individuals, getting a cease and desist notice from their ISP will not affect ideologies already imbued in their heads. On the other hand, if a computer novice who used to buy CDs and DVDs legitimately got the same warning, this wakeup call would much more likely turn them back into buying media the old fashioned way. | |||
[[Image:Proposed Plan for Media Industries.jpg|thumb|center|583px|Proposed Plan for Media Industries]] | |||
Line A shows a generalization of MPAA and RIAAâs current business practices. Assuming that computer gurus upload a lot more than a computer notice who is trying Kazaa for the first time, the number of lawsuits filed increases as computer experience increases. Instead of only concentrating on bringing down the uploaders, the recording industry should increase the number of lawsuits aimed at the first time user. If there was a way to use bots scanning P2P networks to keep track of the reoccurrence of IP addresses, at the optimum situation (line D), the number of lawsuits should be directed to both computer illiterate sympathizers who are using the P2P network for the first time and old school uploaders who are fueling the illegal material. With this two prong attack, the recording industry will not only curtail the spread of piracy but also instill fear using illegal mediums to acquire media in the community of customers. "How well law regulates, or how efficiently, is a different question. But whether better or not, law continues to threaten a certain consequence if it is defined." [http://www.socialtext.net/codev2/index.cgi?what_things_regulate] The RIAA and MPAA should continue to use the powers of law to deter piracy. | |||
=== Employing New Technologies === | |||
* Using technologies to their advantage | |||
** ''Preventing Movie Piracy (Camcording)'' [http://www.techreview.com/read_article.aspx?id=17105&ch=biztech&a=f] | |||
** DRM | |||
=== Using the Masses === | |||
'''Covenant i-Fan Model''' | |||
Although the architecture of the internet allows for programmers to construct P2P infrastructures, the same architecture can also be used to control or at least disrupt these networks. The most common countermeasure the RIAA and the MPAA have used is hiring third party security companies such as Covenant Corporation to upload false media files to discourage users from downloading. Covenant Corporation uses its own servers to mimic users on P2P networks, uploading unusable copyrighted files to unsuspecting downloaders. Through this i-Fan system, Covenant Corporation also encourages users to distribute these files through their personal computers. | |||
Covenant took a step in the right direction but failed to produce the necessary results because of the poor user base. i-Fan offers its users "free money" to help intentionally disseminate these spoof files, however, does not guarantee everyone assisting this project rewards. Over the course of the past three years, only six winners have been announced. [http://www.protectedbycovenant.com/prizewinners.] So where can the MPAA and RIAA harness a big enough user base to start the anti-piracy movement? iTunes. As of 2006, Wired magazine reported that iTunes has over 200 million active customers. [http://www.wired.com/news/mac/0,2125,69193,00.html] If the MPAA and RIAA can convince Apple to tack on something like i-Fan into its iTunes program, the recording industry will have a lawful and practical method of bringing down P2P networks. | |||
[[Image:ITunes Advantage.jpg|center|thumb|601px|iTunes Advantage (coined by Chen Fang)]] | |||
The figure above provides a visual representation of what "iTunes Advantage" adds on to the existing infrastructure. The larger circle on the bottom right hand corner is the existing P2P network. Today, the only spoof computers that upload senseless material into the P2P network are the ones hired by the MPAA and RIAA. With iTunes Advantage, every user currently in the iTunes community has the option of helping to stop piracy. If this plug-in is turned on, iTunes will use built in P2P protocol to upload corrupted content to select P2P networks. To make the deal even more attractive, the recording industries might provide certain amount of iTunes store credit for every megabyte uploaded. With cooperation from Apple, the recording industry can modify the architecture of the internet to stop piracy. | |||
'''Hong Kong Youth Ambassador Model''' | |||
If you can't beat them, recruit them. Instead of hiring professional corporations to implement sophisticated anti-piracy mechanisms and paying an army of lawyers to prosecute the few who are caught, the Hong Kong government launched a revolutionary new anti-piracy program consisting of today's most talented, internet-adept populace -- our kids. Starting on July 18th, 2007, "the Hong Kong government plans to have 200,000 youths search discussion sites for illegal copies of copyrighted songs and movies and report them to the authorities. The campaign has delighted the entertainment industry but prompted misgivings among some civil liberties advocates." [http://www.iht.com/articles/2006/07/18/business/piracy.php] The Youth Ambassadors program consist individuals as young as 9 to scour the internet for links to illegally uploaded copyrighted content. Governmental officials announced, "all members of the Boy Scouts, Girl Guides and nine other uniformed youth groups here, will be expected to participate." "We are not trying to manipulate youths and get them into the spy profession," Tam said. "What we are just trying to do is arouse a civic conscience to report crimes to the authorities." [http://www.iht.com/articles/2006/07/18/business/piracy.php] | |||
Youth Ambassador program has three main goals. One, the program is aimed to promote the importance of intellectual property rights. "Educating youths to respect copyrights is a central goal of the program, officials said. "A lot of Internet piracy is done by young people, particularly in their teens, and the difficulty is it's almost becoming a fashion to download music, download video," said Joseph Wong, the Hong Kong secretary of commerce, industry and technology." Two, by hiring today's youth, government officials hope to expand its abilities to monitor illegal internet activity. And three, if enough reports come in, the government hopes to reduce the amount of illegal BitTorrent seeds available online. [http://sc.info.gov.hk/gb/www.info.gov.hk/gia/general/200607/19/P200607190115.htm] This project "was one of the main campaigns in a series of publicity and educational programs for IPRs protection launched by Commerce, Industry and Technology Bureau on May 29" of this year. In this original pilot run, 60% of all postings to illegal content on forums have been removed. [http://sc.info.gov.hk/gb/www.info.gov.hk/gia/general/200607/19/P200607190115.htm] Hong Kong is setting an anti-piracy methodology for the rest of the world to follow. | |||
== Embrace Policy Amendments == | |||
One of the main motivations behind piracy resides in the desire to bypass barriers to obtain rare or restricted commodities. Whether for professional, creative, or leisure use, people are in constant search for new pictures, music, movies, games and other digital fads. Recently in the United States, thanks to stronger copyright laws, it has become harder and harder to legally acquire these works without going through the hassle of obtaining the correct licenses. Although the ideas patented by private industries were never available for free, public consumption, the Copyright Law revision of 1976 changed the default copyright standards for creative works. Before this fateful year, when an author created a new work of art, it was not automatically protected by copyright unless the author officially applied through the proper government channels. After these legislative changes, "creative works are now automatically copyrighted." [http://wiki.creativecommons.org/Legal_Concepts] Now copyright was applied by default, for "once someone has an idea and produces it in tangible form, the creator is the copyright holder and has the authority to enforce his exclusivity to it." [http://www.articlecity.com/articles/legal/article_987.shtml] These alterations to the law restrict the number of works available in the public domain, increasing the incentives to commit piracy. | |||
=== Free & Copyleft-Like Licensing === | |||
Long before the popularization of personal computers, the internet and the onset of digital piracy, programmers and users alike have supported alternatives to copyright. Although forcing all goods and services in a society be offered for gratis is an extreme solution to the piracy, the action will not only stifle innovation but also crumble a society's economy, thus its infrastructure to exist. Instead, the present copyright laws can be adjusted to better accommodate the creative needs of future generations. Copyleft is a copyright license spin off that allows for the modification of would be copyrighted content. Copyleft "removes restrictions on distributing copies and modified versions of a work for others and requiring that the same freedoms be preserved in modified versions." [http://en.wikipedia.org/wiki/Copyleft] Currently there are several notable movements that have been offering such substitute licensing options: Free Software Foundation's GNU GPL, Open Source Initiative's Academic Free License, Creative Commons License, and quite a few less popular licenses like MIT, BSD, Uol/NCSA, and Apache. | |||
'''Free Software Foundation & GNU GPL''' | |||
[[Image:Free software foundation logo.jpg|thumb|369px|left|Free Software Foundation Logo]] | |||
In 1985, Richard Stallman founded a non-profit organization called The Free Software Foundation. It is "dedicated to promoting computer users' rights to use, study, copy, modify, and redistribute computer programs." [http://www.fsf.org/] Since its establishment, the FSF widely known for its free software advocacy. Besides publishing a very popular GNU GPL (GNU Lesser General Public License), FSF also released one of the first open source operating systems called GNU (GNU's Not Unix). Today, GPL is used by numerous software programmers and corporations as the official license for their software. Popular Wikimedia foundation's wiki projects are all released under the GNU Free Documentation License. | |||
'''Open Source Initiative's & APL''' | |||
[[Image:Open source logo.jpg|thumb|154px|right|Open Source Logo]] | |||
After a decade free software policy promotion, the FSF's goals became distorted by the large amounts of actual "zero cost" software running under its GNU license. This made FSF look like an anti-commercial, anti-market organization rather than a outlet of free expression and free speech. Around 1998, a sect of the free culture movement followers gathered together to push for a less ambigous goal. These people "advocated that the term free software be replaced by open source software (OSS) as an expression which is more comfortable for the corporate world." [http://en.wikipedia.org/wiki/Open-source_software] Founded by Eric Raymond and Bruce Perens in February 1988, the OSI (Open Source Initiative) "sought to bring a higher profile to the practical benefits of freely available source code, and they wanted to bring major software businesses and other high-tech industries into open source." [http://en.wikipedia.org/wiki/Open-source_software] Raymond suggested the development of open source software should following his "Bazaar" model, which included the following traits: users treated as co-developers, early releases, frequent integration, several versions, high modularization, and dynamic decision making structure. Popular projects like Apache, Linux, Netscape, and Perl follow this model. Right now the Open Source Initiative serves as a "community-recognized body for reviewing and approving licenses as OSD (open source development) conformant." [http://www.opensource.org/about] | |||
'''Creative Commons & CC License ''' | |||
[[Image:Creative commons logo.jpg|thumb|200px|left|Creative Commons Logo]] | |||
Creative Commons is a non-profit organization that allows for âauthors, scientists, artists, and educators easily mark their creative work with the freedoms they want it to carry.â [http://www.creativecommons.org/] Founded by Lawrence Lessig in 2001, Creative Commons offers free licensing to the whole spectrum of individuals from every corner of the media background. These Creative Commons licenses come in several different flavors, offering selective protections such as forbidden commercial use or mandatory sharealike distribution. They enable âcopyright holders to grant some or all of their rights to the public while retaining others through a variety of licensing and contract schemes including dedication to the public domain or open content licensing terms. The intention is to avoid the problems current copyright laws create for the sharing of information.â [http://en.wikipedia.org/wiki/Creative_Commons] By using CC Licenses, producers of what would be considered protected intellectual property can release their works to the public in confidence, for consumers will know exactly what they can and cannot do with the licensed work. | |||
Unlike the GNUâs GPL, which is mainly used by programmers to license software creations, Creative Commons licenses can be applied to all kinds of media. CreativesCommons.org provides custom-made online tools and straightforward directions to help users license their work. Once a proper license is chosen, the online community has access to three editions â one laymenâs terms for regular users, one in legal writing for lawyers, and one in code for computers. Comprehensive translations are also available for international users. | |||
= Reflections = | = Reflections = | ||
| Line 240: | Line 550: | ||
** Family influences | ** Family influences | ||
** Group mentality phenomenon | ** Group mentality phenomenon | ||
[http://ezp1.harvard.edu/login?url=http://search.ebscohost.com/login.aspx?direct=true&db=aph&AN=14072647&site=ehost-live&scope=site Kids: Stealing Digital Data OK, 2004] | |||
* Newspaper article reports the 2004 BSA findings (same study was redone in 2006 and once more in 2007) | |||
"Youth admits it's illegal, but download music, movies, games anyway" | |||
"Of the 1,100 eight to 18-year-olds polled, more than 80 percent know that music, movies, games, and software arc protected by law, and more than 60 percent know the same applies to Web sites. Yet 53 percent of kids still download music and more than a third download games. Only 22 percent of kids, however, steal larger files such as software and 17 percent copy movies. A measly 29 percent think illegal copying is wrong. No wonder. Eight percent say their parents approve of the activity." | |||
"Kids cite a number of reasons for illegal downloading, from not having the money to pay for software (51 percent) to the rationale that "lots of people do it" (33 percent). Twenty-six percent also view file stealing as a victimless crime, saying it "doesn't hurt anybody." | |||
"Interestingly, 59 percent of kids say their knowledge of intellectual property comes from television. Other sources include parents and the Internet (44 percent), and friends (30 percent). Teachers ranked dead last at 18 percent." | |||
[http://www.broadcastingcable.com/article/CA6432259.html Study: Students Don't Understand Copyright Rules] | |||
* Small study conducted by 2 college professors find students don't understand copyright laws | |||
"AU School of Communications Professor Patricia Aufderheide and Washington College of Law's Peter Jaszi polled 51 graduate and undergraduate students who upload videos and held more extensive interviews with 15 of them." | |||
"The majority of students (87%) who upload copyrighted material to user-generated video sites likeYouTube, Facebook or MySpace don't get permission from copyright owners, even though most (74%) believe it is fair to pay people for their use." | |||
"The study concluded that students were, "universally underinformed and misinformed about the law." While 76% of the students said that the Fair Use doctrine allowed them to use copyrighted material, none could accurately define the doctrine." | |||
"While they were generally concerned with staying on the "good side" of the law, they were "making up rules themselves" about what and how to use intellectual property. They also did not understand their own rights as creators of content." | |||
Students' justifications of why they copyright content: | |||
* Sharing a file is like talking with colleagues near a virtual water cooler environment | |||
* Putting "all rights reserved" on a copyrighted clip protects him from the owner | |||
* Gives the owner of the copyright free publicity/advertisement | |||
[http://www.bsa.org/usa/press/newsreleases/may-2007-youth-ed.cfm Illegal Downloading Among Youth Drops, Reports New Study] | |||
* BSA's 2007 study on youth piracy, shows piracy down from 2004 | |||
[[Image:Illegal downloading among kids.jpg|thumb|479px|Business Software Alliance May 2007 Report]] | |||
[[Image:Parental guidance.jpg|thumb|479px|Business Software Alliance May 2007 Report]] | |||
"The results of a recent nationwide survey released by the Business Software Alliance (BSA) show that illegal downloading of digital copyrighted works by youth (ages 8 to 18) has dropped by 24 percent in the last three years." | |||
"The survey, first conducted in 2004, indicated that 60 percent of survey participants reported downloading software, music, movies, or games without paying for it; in 2006 the percentage of those who downloaded without paying dropped to 43 percent; and in 2007 the percentage decreased to 36 percent. Youth report that parental oversight is a significant motivator and key influencing factor in their online behavior." | |||
Top factors that kids worry about when downloading digital copyrighted works: | |||
* Fear of accidentally downloading a computer virus (62 percent) | |||
* Getting into legal trouble (52 percent) | |||
* Accidentally downloading spyware (51 percent) | |||
* Fear of getting in trouble with parents (48 percent, increasing from 40 percent in 2006) | |||
âThis study indicates that parents represent a growing and effective influence on the online practices of youth,â said Diane Smiroldo, vice president of public affairs for BSA. âBut, while decreases in downloading are encouraging over recent years, youth are still taking too many risks online. We hope that parents continue to take seriously their role in helping their children make the right choices online. Fortunately, the survey found that more than half of the students have been warned by their parents about dangerous, illegal online behaviors. Imposing rules and ensuring your children abide by them may be an old-fashioned concept for cyberspace, but it works.â | |||
Illegal downloading among kids have dropped in recent years: | |||
* 22% of kids illegally downloaded software in 2004, 14% in 2006, 11% in 2007 | |||
* 53% of kids illegally downloaded music in 2004, 32% in 2006, 30% in 2007 | |||
* 17% of kids illegally downloaded movies in 2004, 10% in 2006, 8% in 2007 | |||
Parental guidance plays a big role in kids' lives: | |||
* 87% surf the web without parental rules, 63% with rules | |||
* 55% buy something without parental rules, 19% with rules | |||
* 52% download software without parental rules, 19% with rules | |||
* 47% illegally download music without parental rules, 16% with rules | |||
== Other Side of the Debate == | == Other Side of the Debate == | ||
Is piracy really causing problems for the programming/entertainment industries? | |||
* ''Russian teacher fined for MS piracy'' [http://www.theregister.co.uk/2007/05/08/russian_teacher_ms_piracy_case/] | * ''Russian teacher fined for MS piracy'' [http://www.theregister.co.uk/2007/05/08/russian_teacher_ms_piracy_case/] | ||
* ''When Piracy Becomes Promotion'' [http://www.technologyreview.com/Biotech/13722/] | |||
"The underground subtitling and circulation of Japanese anime helped to open the American market to Asian cultural imports." | |||
"The global sales of Japanese animation and character goods, an astonishing 9 trillion yen ($80 billion) has grown to 10 times what it was a decade ago." | |||
"The Cartoon Network features a wide array of anime series as part of its late night Adult Swim programming. ADV Films, a major importer of anime series for the American market, has launched a 24 hours Anime Network. TOKYOPOP, a Los Angeles-based company, will publish 400 volumes of translated manga (Japanese comics) for U.S. consumption this year. One can find whole shelves of manga in many Barnes and Noble or Borders bookstores, where they frequently outsell American-produced graphic novels." | |||
"The clubs, such as the MIT Anime Club, functioned as lending libraries and dubbing centers as well as holding marathon screenings to attract new members." | |||
"Japanese distributors winked at these screenings. They didnt have permission from their mother companies to charge these fans or provide the material but they were interested to see how much interest the shows attracted." | |||
"Many U.S. media companies might have regarded all of this underground circulation as piracy and shut it down before it reached critical mass. The Japanese media companys tolerance of these fan efforts is consistent with their similar treatment of fan communities in their local market. As Temple University law professor Salil K. Mehra notes, the underground sale of fan-made manga, often highly derivative of the commercial product, occurs on a massive scale in Japan, with some comics markets attracting 150,000 visitors per day; such markets are held almost every week in some parts of the country. Rarely taking legal action, the commercial producers sponsor such events, using them to publicize their releases, to recruit potential new talent, and to monitor shifts in audience tastes. In any case, they fear the wrath of their consumers if they took action against such a well-entrenched cultural practice and the Japanese legal structure would provide for fairly small legal penalties if they did pursue infringers." | |||
"More generally, as Yuichi Washida, a research director at Hakuhodo, Japans second largest advertising and marketing firm, has argued, Japanese corporations have sought to collaborate with fan clubs, subcultures, and other consumption communities, seeing them as important allies in developing compelling new content or broadening markets. In courting such fans, the companies helped to construct a moral economy that aligned their interests in reaching a market with the American fans desires to access more content." | |||
* Piracy in developing countries | |||
Piracy is no doubt a huge problem overseas. Although most countries have anti-piracy legislation in place, the enforcement of these laws are not up to par with global standards. Especially in developing countries where local governments have no incentives of protecting foreign intellectual property, whole industries have been built around the concept of illegally duplicating and distributing media for individual gains. The Motion Pictures industry in 2005 claimed that there were "more than 34,000 cases of piracy and assisted law enforcement officials in conducting more than 10,500 raids. These activities resulted in the seizure of more than 34 million illegal optical discs, 55 factory optical disc production lines and 3,362 optical disc burners, as well as the initiation of more than 8,000 legal actions." [http://www.mpaa.org/AsiaPacificPiracyFactSheet.pdf] Despite these proactive measures, MPA still projected a sum total of more than one billion dollars in lost potential revenue for 2005 in the Asia-Pacific region alone. | |||
" | While the entertainment industry frantically tries to control piracy overseas, software businesses have a lighter view on this issue. Although software piracy is no better compared to media piracy abroad, there is less concern from the corporate side. In these developing countries, the biggest competitors for legitimate software companies are open source organizations. Since, software engineers are vying to attract a larger portion of the new population to use their product, strategists have have concluded piracy may actually help companies defeat the open source movement. Take the software giant Microsoft for example. It "acknowledges that piracy sometimes helps the company establish itself in emerging markets and fend off threats from free open-source programs." [http://www.hunterstrat.com/news/2006/04/09/third-world-piracy-actually-good-for-microsoft/] In countries like China and India, even though a huge portion of the population operates on counterfeit versions of Windows and unactivated versions of Office, at the end of the day they are still using Microsoft made products. If the strategy to empower both the legitimate and illegitimate user base works out as planned, when a country's economy matures in the long run, the majority of the population will be more willing to buy Microsoft's genuine software. Just look at Vietnam, "which at more than 90% has the highest piracy rate in the world, has improved from 100% in 1994. The No. 1 software firm in Vietnam: Microsoft." [http://www.hunterstrat.com/news/2006/04/09/third-world-piracy-actually-good-for-microsoft/] | ||
The | The debate about whether or not severe anti-piracy measures are necessary in developing countries is an hot issue, for there are good supporting arguments for both parties. The value of a piece of software varies directly with the size of its user base. Without a substantial base of users, software products cannot survive. In these developing countries where the majority of the population cannot afford many of life's luxuries, asking them to dump several hundred dollars for a copy of Windows Vista is ridiculous. But, for every pirated of Vista bought Microsoft is loosing potential revenue. So, the final question to be asked is -- constituents a potential sale? | ||
* Romanian President to Gates: Windows Piracy Built This Country [http://www.engadget.com/2007/02/02/romanian-prez-to-gates-windows-piracy-built-this-country/] | |||
= Relevant Research = | = Relevant Research = | ||
| Line 272: | Line 655: | ||
[http://www.benedict.com/digital/digital.aspx Digital copyright court cases] | [http://www.benedict.com/digital/digital.aspx Digital copyright court cases] | ||
[http://arstechnica.com/news.ars/post/20070619-the-youtube-effect-http-traffic-now-eclipses-p2p.html The YouTube effect: HTTP traffic now eclipses P2P] | |||
[http://www.law.uchicago.edu/Lawecon/WkngPprs_151-175/162.ls.file-swapping.pdf Charismatic Code, Social Norms, and the Emergence of Cooperation on the File-Swapping Networks] | |||
[http://crunchgear.com/2007/05/14/help-key-the-essential-guide-to-piracy/ The Essential Guide to Piracy] | |||
== Youth & Piracy == | == Youth & Piracy == | ||
[http://www.bsa.org/usa/press/newsreleases/Majority-of-Youth-Understand-Copyright.cfm Majority of Youth Understand âCopyright,â But Many Continue To Download Illegally | [http://www.bsa.org/usa/press/newsreleases/Majority-of-Youth-Understand-Copyright.cfm Majority of Youth Understand âCopyright,â But Many Continue To Download Illegally] | ||
[http://www.vnunet.com/vnunet/news/2124580/parents-pick-piracy-kids Parents pick up piracy from kids] | [http://www.vnunet.com/vnunet/news/2124580/parents-pick-piracy-kids Parents pick up piracy from kids] | ||
[http://www.foxnews.com/story/0,2933,94960,00.html Online Piracy: The Ultimate Generation Gap] | |||
[http://www.acm.org/crossroads/xrds10-3/piracy.html The Effects of Piracy in a University Setting] | |||
[http://www.broadcastingcable.com/article/CA6432259.html Study: Students Don't Understand Copyright Rules] | |||
[http://www.bsa.org/usa/press/newsreleases/may-2007-youth-ed.cfm Illegal Downloading Among Youth Drops, Reports New Study] | |||
== Youth & Technology == | == Youth & Technology == | ||
[http://news.bbc.co.uk/1/hi/technology/4403574.stm US youths use internet to create | [http://news.bbc.co.uk/1/hi/technology/4403574.stm US youths use internet to create] | ||
PDF: Teen Content Creators and Consumers | PDF: Teen Content Creators and Consumers [http://www.pewinternet.org/pdfs/PIP_Teens_Content_Creation.pdf] | ||
[http://www.itnews.com.au/newsstory.aspx?CIaNID=17377&eid=1&edate=20041223 Youth value technology: poll ] | [http://www.itnews.com.au/newsstory.aspx?CIaNID=17377&eid=1&edate=20041223 Youth value technology: poll ] | ||
== Anti-Piracy == | == Anti-Piracy == | ||
[http://torrentfreak.com/anti-piracy-gang-launches-their-own-video-download-site-to-trap-people/ Anti-Piracy Gang Launches their own Video Download Site to Trap People] | |||
[http://gizmodo.com/gadgets/sorry-pirates/drm+free-itunes-songs-have-embedded-user-info-264574.php DRM-free iTunes Songs Have Embedded User Info, 2007] | |||
[http://www.spiegel.de/spiegelspecial/0,1518,490777,00.html Darnstädt, T.: Die Gratis Kultur, in: Spiegel Online, 2007.] | |||
=== Organizations === | |||
[http://www.siia.net/piracy/default.asp (Software & Other Content) SIIA & the SPA: Anti-Piracy] ([http://www.siia.net/membership/memberlist.asp SIIA Member List]) | |||
"SIIA and its predecessor organization, the Software Publishers Association (SPA), have the longest-running software anti-piracy program in existence. Started in the mid-1980s, SIIA's Corporate Anti-Piracy program identifies, investigates, and resolves software piracy cases on behalf of our members. As Internet-based piracy has emerged, SIIA again broke new ground and now has an extensive program for tackling software pirates operating over the Internet, ensuring that SIIA members receive the maximum protection possible." | |||
[http://bsa.org/Piracy%20Portal.aspx (Commercial Software) BSA: Anti-Piracy] | |||
([http://bsa.org/country/BSA%20and%20Members/Our%20Members.aspx BSA Member List]) | |||
"The Business Software Alliance is the voice of the worldâs commercial software industry and its hardware partners before governments and in the international marketplace. BSA programs foster technology innovation through education and policy initiatives that promote copyright protection, cyber security, trade, and e-commerce." | |||
[http://www.theesa.com/ip/index.php (Gaming Industry) ESA: Intellectual Property] | [http://www.theesa.com/ip/index.php (Gaming Industry) ESA: Intellectual Property] | ||
"The Entertainment Software Association (ESA) is the U.S. association exclusively dedicated to serving the business and public affairs needs of companies that publish video and computer games for video game consoles, personal computers, and the Internet. The ESA offers a range of services to interactive entertainment software publishers including a global anti-piracy program, business and consumer research, government relations and intellectual property protection efforts. ESA also owns and operates the E3 Media & Business Summit." | |||
[http://mpaa.org/piracy.asp (Movie Industry) MPAA: Anti-Piracy] | [http://mpaa.org/piracy.asp (Movie Industry) MPAA: Anti-Piracy] | ||
"The Motion Picture Association of America (MPAA) and its international counterpart, the Motion Picture Association (MPA) serve as the voice and advocate of the American motion picture, home video and television industries, domestically through the MPAA and internationally through the MPA. Today the association continues to advocate for strong protection of the creative works produced and distributed by the industry, fights copyright theft around the world, and provides leadership in meeting new and emerging industry challenges." | |||
[http://www.siia.net/piracy/ | [http://www.riaa.com/physicalpiracy.php (Music Industry) RIAA: Anti-Piracy] | ||
"The Recording Industry Association of America (RIAA) is the trade group that represents the U.S. recording industry. Its mission is to foster a business and legal climate that supports and promotes our members' creative and financial vitality. Its members are the record companies that comprise the most vibrant national music industry in the world. In support of this mission, the RIAA works to protect intellectual property rights worldwide and the First Amendment rights of artists; conducts consumer, industry and technical research; and monitors and reviews state and federal laws, regulations and policies." | |||
=== Stats & Studies === | |||
[http://www.siia.net/piracy/yir_2006.pdf SIIA: 2006 Anti-Piracy Year in Review] | |||
[http://w3.bsa.org/globalstudy//upload/2007-Losses-EMEA.pdf BSA: 2006 Global Software Piracy Study: European Union] | |||
[http://w3.bsa.org/globalstudy//upload/2007-Piracy-Study-Findings.pdf BSA: Fourth Annual Global Software Piracy Study] | |||
[http://www.theesa.com/facts/top_10_facts.php ESA: Top 10 Industry Facts] | |||
[http://mpaa.org/2006-US-Theatrical-Market-Statistics-Report.pdf MPAA: 2006 US Theatrical Market Statistics Report] | |||
[http://mpaa.org/International%20Theatrical%20Snapshot.pdf MPAA: International Theatrical Snapshot] | |||
[http://mpaa.org/MovieAttendanceStudy.pdf MPAA: Movie Attendance Study] | |||
[http://mpaa.org/USEntertainmentIndustryMarketStats.pdf MPAA: US Entertainment Industry Market Statistics] | |||
[http://www.mpaa.org/2006_05_03leksumm.pdf LEK: The Cost of Movie Piracy] | |||
[http://76.74.24.142/6BC7251F-5E09-5359-8EBD-948C37FB6AE8.pdf RIAA: 2006 Year-End Shipment Statistics] | |||
== Pro-Piracy == | == Pro-Piracy == | ||
[http://www.theregister.co.uk/2007/05/08/russian_teacher_ms_piracy_case/ Russian teacher fined for MS piracy | [http://www.theregister.co.uk/2007/05/08/russian_teacher_ms_piracy_case/ Russian teacher fined for MS piracy] | ||
[http://dir.salon.com/story/tech/feature/2002/09/26/piracy_unlimited/index.html Profits from Piracy: Microsoft in China] | [http://dir.salon.com/story/tech/feature/2002/09/26/piracy_unlimited/index.html Profits from Piracy: Microsoft in China] | ||
[http://www.technologyreview.com/Biotech/13722/ When Piracy Becomes Promotion] | |||
[http://www.engadget.com/2007/02/02/romanian-prez-to-gates-windows-piracy-built-this-country/ Romanian President to Gates: Windows Piracy Built This Country] | |||
[http://online.wsj.com/article/SB118420443945664247.html?mod=hpp_us_editors_picks Pirated Music Helps Radio Develop Playlists] | |||
== Possible Solutions == | == Possible Solutions == | ||
[http://knowledge.wharton.upenn.edu/article.cfm?articleid=863 Suing Your Customers: A Winning Business Strategy? | [http://knowledge.wharton.upenn.edu/article.cfm?articleid=863 Suing Your Customers: A Winning Business Strategy?] | ||
[http://www.iht.com/articles/2006/07/18/business/piracy.php Hong Kong enlists youth to fight piracy] | [http://www.iht.com/articles/2006/07/18/business/piracy.php Hong Kong enlists youth to fight piracy] | ||
== | == Piracy in the News == | ||
[http://www.jasonkolb.com/weblog/2007/02/viacom_the_late.html Viacom the Latest Company to Misunderstand the Internet, Jason Kolb, 2007] | [http://www.jasonkolb.com/weblog/2007/02/viacom_the_late.html Viacom the Latest Company to Misunderstand the Internet, Jason Kolb, 2007] | ||
| Line 317: | Line 763: | ||
[http://www.boingboing.net/2007/02/03/viacom_terrorizes_yo.html Viacom Terrorizes YouTube, Cory Doctorow at Boing Boing, 2007] | [http://www.boingboing.net/2007/02/03/viacom_terrorizes_yo.html Viacom Terrorizes YouTube, Cory Doctorow at Boing Boing, 2007] | ||
[http://www.latimes.com/entertainment/news/la-fi-pollmusic9aug09,0,4581014.story LA Times: Is Copying a Crime? | [http://www.latimes.com/entertainment/news/la-fi-pollmusic9aug09,0,4581014.story LA Times: Is Copying a Crime? Well ..., 2006] | ||
[http://www.nytimes.com/2007/02/26/technology/26cspan.html?_r=2 Which Videos Are Protected? Lawmakers Get a Lesson, 2007] | [http://www.nytimes.com/2007/02/26/technology/26cspan.html?_r=2 Which Videos Are Protected? Lawmakers Get a Lesson, 2007] | ||
| Line 327: | Line 773: | ||
[http://australianit.news.com.au/story/0,24897,20713160-15306,00.html Piracy stats don't add up, 2006] | [http://australianit.news.com.au/story/0,24897,20713160-15306,00.html Piracy stats don't add up, 2006] | ||
[http://www.theregister.co.uk/2007/03/29/ebay_software_counterfeiter_jailed/ Indiana man jailed for selling counterfeit software on eBay] | [http://www.theregister.co.uk/2007/03/29/ebay_software_counterfeiter_jailed/ Indiana man jailed for selling counterfeit software on eBay, 2007] | ||
[http://www.usatoday.com/money/media/2004-11-05-glickman_x.htm, Movie Swappers Put on Notice, 2004] | [http://www.usatoday.com/money/media/2004-11-05-glickman_x.htm, Movie Swappers Put on Notice, 2004] | ||
| Line 333: | Line 779: | ||
[http://www.poughkeepsiejournal.com/apps/pbcs.dll/article?AID=/20060905/LIFE/60905008 Poughkeepsie Online: Music Swappers Sued, 2003] | [http://www.poughkeepsiejournal.com/apps/pbcs.dll/article?AID=/20060905/LIFE/60905008 Poughkeepsie Online: Music Swappers Sued, 2003] | ||
[http:// | [http://cyber.law.harvard.edu/is99/RioSpaceShifter.htm In Court's View, MP3 Player is Just a 'Space Shifter', 1999] | ||
[http://boingboing.net/2006/06/09/antiitunes_drm_demon.html Anti-iTunes DRM demonstrations across the USA tomorrow, 2006] | |||
[http:// | [http://www.businessweek.com/globalbiz/content/apr2007/gb20070402_391654.htm?chan=globalbiz_europe_more+of+today's+top+stories Apple, EMI Ink DRM-Free Music Plan, 2007] | ||
[http://news.com.com/Bush+signs+law+targeting+P2P+pirates/2100-1028_3-5687495.html New law cracks down on P2P pirates, 2005] | |||
[http://www.nlpc.org/view.asp?action=viewArticle&aid=2082 Is Google Promoting Video Piracy?, 2007] | |||
[http://www.techcrunch.com/2007/07/11/top-50-videos-google-is-pirating/ Top 50 Copyrighted Videos Google is Pirating, 2007] | |||
[http://news.digitaltrends.com/news/story/13616/isp_protects_file-swappers_identities ISP Protects File-Swappers' Identities, 2007] | |||
[http://web20.telecomtv.com/pages/?newsid=41371&id=e9381817-0593-417a-8639-c4c53e2a2a10&view=news AT&T moves to prevent Internet piracy on its network, 2007] | |||
[http://www.businessweek.com/innovate/content/mar2007/id20070313_676246.htm?chan=top+news_top+news+index_innovation+%2Bamp%3B+design Piracy is Big Business, 2007] | |||
[http://news.xinhuanet.com/english/2007-07/18/content_6395537.htm Baidu faces new lawsuit over music piracy, 2007] | |||
[http://www.nintendic.com/news/745 NES piracy surfaces on Facebook, 2007] | |||
[http://www.pcworld.com/article/id,134995-c,cybercrime/article.html China, FBI Bust Piracy Syndicate, 2007] | |||
[http://www.tgdaily.com/content/view/33022/120/ RIAA says lawsuits cannot be the complete answer to music piracy, 2007] | |||
[http://arstechnica.com/news.ars/post/20070723-bill-would-force-top-25-piracy-schools-to-adopt-anti-p2p-technology.html Bill would force "top 25 piracy schools" to adopt anti-P2P technology, 2007] | |||
[http://news.bbc.co.uk/go/pr/fr/-/2/hi/entertainment/6993752.stm BBC News - Pop Star Prince gets togh on Web Pirates, 09.13.07] | |||
== RIAA Pre-Litigation Letters == | |||
[http://riaa.com/newsitem.php?id=780E8751-0E03-4258-D651-F991B66E1708 July 18, 2007: Sixth Wave] | |||
Targeted: 23 Colleges | |||
State University of New York at Morrisville (34 pre-litigation settlement letters), Georgia Institute of Technology (31), Pennsylvania State University (31), University of Central Arkansas (27), University of Delaware (23), Northern Michigan University (20), Rensselaer Polytechnic Institute (20), George Washington University (19), Ohio State University (19), New Mexico State University (17), Eckerd College (16), University of Minnesota (16), California State University - Monterey Bay (14), University of Kansas (14), University of Missouri - Rolla (14), University of San Francisco (13), Case Western Reserve University (12), Northern Arizona University (12), San Francisco State University (12), University of Tulsa (12), Franklin and Marshall College (11), Western Kentucky University (11), and Santa Clara University (10) | |||
[http://riaa.com/newsitem.php?news_year_filter=&resultpage=2&id=7710D405-A886-F768-B8AD-EBC0E4831DD1 June 8, 2007: Fifth Wave] | |||
Targeted: 19 Colleges | |||
Dartmouth College (13 pre-litigation settlement letters), DePaul University (19), Drexel University (26), Northeastern University (10), Northwestern University (16), North Carolina State University (43), Rochester Institute of Technology (19), Stanford University (19), Texas Christian University (7), University of California - Davis (34), University of California - Irvine (23), University of California - Los Angeles (37), University of California - San Diego (9), University of California - Santa Cruz (15) , University of Chicago (18), University of Nebraska - Lincoln (33), University of Oregon (17), Western Washington University (15), and Wichita State University (22) | |||
[http://riaa.com/newsitem.php?news_year_filter=&resultpage=3&id=C2476AFF-A70F-0567-76C2-FC3ECEE93D8E May 2, 2007: Fourth Wave] | |||
Targeted: 13 Colleges | |||
Brandeis University (15 pre-litigation settlement letters), Duke University (35), Iowa State University (15), Massachusetts Institute of Technology â MIT (23), Northern Illinois University (50), Syracuse University (20), Tufts University (15), University of Georgia (19), University of Iowa (25), University of Southern California (50), University of South Florida (50), University of Tennessee (50), and the University of Texas - Austin (35) | |||
[http://riaa.com/newsitem.php?news_year_filter=&resultpage=4&id=7408966D-245D-A17D-4869-C0DB1E7ADA97 April 11, 2007: Third Wave] | |||
Targeted: 22 Colleges | |||
Bates College (7 pre-litigation settlement letters), Brown University (12), Central Michigan University (24), Colby College (5), College of William & Mary (12), Cornell University (19), Fairfield University (15), Florida International University (16), Indiana University (28), Keene State University (19), Kent State University (19), Morehead State University (10), Ohio University (50), Oklahoma State University (16), University of Massachusetts â Amherst (32), University of Maryland System (25),University of Michigan â Ann Arbor (23), University of New Hampshire (17), University of New Mexico (16), University of Pennsylvania (17), University of Rochester (22), and Williams College (9) | |||
[http://riaa.com/newsitem.php?news_year_filter=&resultpage=5&id=B3196098-01D3-FCD7-E97E-E8F8384E4986 March 21, 2007: Second Wave] | |||
Targeted: 23 Colleges | |||
Boston University (50 pre-litigation settlement letters), Columbia University (20), Dartmouth College (11), DePaul University (18), Drexel University (20), Ferris State University (17), Ithaca College (20), Purdue University (38), University of California - Berkeley (19), University of California - Los Angeles (21), University of California - Santa Cruz (17), University of Maine system (27), University of Nebraska - Lincoln (25), University of Wisconsin system (66, including the following individual campuses: Eau Claire, Madison, Milwaukee, Parkside, Platteville, Stevens Point, Stout, and Whitewater), Vanderbilt University (20), and Virginia Polytechnic Institute & State University (16) | |||
[http://riaa.com/newsitem.php?news_year_filter=&resultpage=5&id=0BB7A35D-544B-2DD2-F374-4F680D6BAE9B February 28, 2007: First Wave] | |||
Targeted: 13 Colleges | |||
Arizona State University (23 pre-settlement litigation letters), Marshall University (20), North Carolina State University (37), North Dakota State University (20), Northern Illinois University (28), Ohio University (50), Syracuse University (37), University of Massachusetts â Amherst (37), University of Nebraska â Lincoln (36), University of South Florida (31), University of Southern California (20), University of Tennessee â Knoxville (28), and University of Texas â Austin (33) | |||
== Legal Notes == | == Legal Notes & Guides == | ||
[http://www.law.cornell.edu/uscode/html/uscode17/usc_sup_01_17.html Cornell Law School Legal Information Institute - US Code: Title 17, Copyrights] | [http://www.law.cornell.edu/uscode/html/uscode17/usc_sup_01_17.html Cornell Law School Legal Information Institute - US Code: Title 17, Copyrights] | ||
| Line 346: | Line 856: | ||
[http://www.gseis.ucla.edu/iclp/dmca1.htm DMCA: The Digital Millennium Copyright Act] | [http://www.gseis.ucla.edu/iclp/dmca1.htm DMCA: The Digital Millennium Copyright Act] | ||
[http://www.copyright.gov/legislation/pl109-9.html Family Entertainment and Copyright Act] | |||
[http://www.law.cornell.edu/uscode/html/uscode17/usc_sec_17_00000107----000-.html Cornell Law School Legal Information Institute - US Code: Title 17, Chapter 1, Section 107, Fair Use] | |||
[http://www.chillingeffects.org/fairuse/faq.cgi Frequently Asked Questions (and Answers) about Copyright and Fair Use] | |||
== Resources from Gutman Library == | |||
''The following resources are pulled from Harvard's library system. You need a Harvard University ID and PIN to access them.'' | |||
[http://web.lexis-nexis.com.ezp2.harvard.edu/universe/document?_m=91b41511d8701cd3f605debb5699f4c6&_docnum=16&wchp=dGLbVzz-zSkVb&_md5=b11b8af6dbd464619a5e69d290d431f5 Privacy V. Piracy, 2005] | |||
[http://web.lexis-nexis.com.ezp2.harvard.edu/universe/document?_m=69b4a70780fe80770a6459b10d5613be&_docnum=37&wchp=dGLbVzz-zSkVb&_md5=344bf4d0f80a0e13e4e3b9b395b07b88 Don't Shoot The Messenger: Copyright Infringement In The Digital Age, 2003] | |||
[http://web.lexis-nexis.com.ezp2.harvard.edu/universe/document?_m=c5064934a128565e2825964626d6f8d8&_docnum=6&wchp=dGLbVzz-zSkVb&_md5=2e87f344fd1d7e704ff7b11d1cf44627 U.S. to step up piracy battle, 2007] | |||
[http://web.lexis-nexis.com.ezp2.harvard.edu/universe/document?_m=7e1c95ad823494928f4c2ee24d13ed2f&_docnum=26&wchp=dGLbVzz-zSkVb&_md5=529641701043fb669843be9fa3609354 France Debates Downloads, With Teenager As Top Expert, 2006] | |||
[http://web.lexis-nexis.com.ezp2.harvard.edu/universe/document?_m=6fc3ff61659e35907b99ed637963ada7&_docnum=58&wchp=dGLbVzz-zSkVb&_md5=0fd0148d85eaae53ba614abdf603ac41 Record industry sues fans for illegally downloading music from the internet, 2004] | |||
[http://ezp1.harvard.edu/login?url=http://search.ebscohost.com/login.aspx?direct=true&db=aph&AN=3465712&site=ehost-live&scope=site The Heavenly Jukebox, 2000] | |||
[http://ezp1.harvard.edu/login?url=http://search.ebscohost.com/login.aspx?direct=true&db=aph&AN=11008385&site=ehost-live&scope=site Discussing Cyber Ethics with Students Is Critical, 2003] | |||
[http://ezp1.harvard.edu/login?url=http://search.ebscohost.com/login.aspx?direct=true&db=aph&AN=14072647&site=ehost-live&scope=site Kids: Stealing Digital Data OK, 2004] | |||
[http://web.lexis-nexis.com.ezp2.harvard.edu/universe/document?_m=d520576e58ef5bf18134cf4f3ffe3834&_docnum=1&wchp=dGLbVlb-zSkVA&_md5=643a0a82adff308c7207a0ab3b00cb00 We're a pirate nation, 2007] | |||
[http://www.newstatesman.com/pdf/CounterfeitingCulture2006.pdf Counterfeiting Culture, 2006] | |||
[[Category:Core Articles]] | |||
Latest revision as of 20:29, 24 November 2007
Narratives
- Trevor is doing a project for school. Since he is very adept at video mashups, he decides to use clips from different TV shows and movies to assist him with the project. After completing the masterpiece, Trevor is very excited about his work and wants not only his class but also the whole world to see his creation. Due to the fact that long segments of copyrighted material were used in the making of this clip, he decides to post the video onto YouTube with an obscure name to avoid detection and uploads it onto five other video sharing services DailyMotion, Revver, GoFish, MySpace Video, and Facebook Video to act as mirrors. He then embeds the clip onto his blog and uses IM, email, text messaging, and Twitter to spread the word about this update.
Involves the use of the following applications: Adobe Premiere, Audacity, Trillian, Thunderbird
And services: YouTube, Daily Motion, Revver, GoFish, MySpace, Facebook, Textem, and Twitter.
- Questions raised from this scenario:
- What constitutes fair use?
- Do copyright laws impede creativity?
- Trevor and friends are hanging out in his basement on a lazy Sunday afternoon. They just watched a trailer of an upcoming blockbuster film and the whole group is very excited -- they canât wait to get in line to see the first midnight showing. Unfortunately, the filmâs release date is one week away. With nothing else to do, Trevor proposes that he could obtain a copy of the film via a private torrent network whose administrator is a member of an infamous release group. A few of his friends brings up the concern about piracy, but since the group is at Trevorâs house, using Trevor's internet connection, nobody objects -- in fact, a few never realized this was possible. After a quick debate about what to do, soon the majority of the group wants the movie downloaded and burned to discs for everyone to have.
Involves the use of the following applications: Quicktime, uTorrent, PeerGuardian 2, DivX Player, XviD Video Codec, AC3 Audio Codec
And services: <Torrent Website>, <Release Group>
- Questions raised from this scenario:
- Who should be more responsible for the piracy? The release group or the end user?
- How does group mentality play affect piracy?
- After seeing Trevor successfully obtain the movie, one of Trevorâs friends decide to get more movies from a P2P program he installed a while back. After firing the application up, his computer freezes. Not knowing what happened, Trevorâs friend does a simple force reboot and after the restart, everything seems fine. In the background processes, however, the P2P program automatically shared his whole media folder to the rest of the P2P community without telling the user.
Involves the use of the following applications: <P2P Application>
- Questions raised from this scenario:
- If a P2P program automatically shares all the media on a user's computer and the user is accused of copyright infringement, who should take the blame? The P2P company or the end user?
- The tech companies hired by the media industries to track down internet pirates is known for only targeting uploaders, rarely downloaders. Is this technique working?
- Trevor's family live in a fairly large condominium complex. Although all the computers in Trevor's house are connected via an encrypted wireless local area connection, Trevor's laptop has the ability to detect and connect to several other neighbor's wireless routers from the comforts of his bedroom. Since his laptop's wireless card is set connect to the closest router, Trevor often surfs the net & downloads copyrighted media using his neighbor's connection.
Involves the use of the following applications: <Wireless Configuration Utility>
- Questions raised from this scenario:
- A large majority of home wireless routers do not ship with WEP and WPA security turned on, causing many personal networks to be exposed to outside threats. If an outsider uses your wireless connection to facilitate illegal file sharing, what rights do you have as the innocently accused?
Introduction to Piracy

In the simplest terms, piracy is obtaining materials without the proper rights of legal ownership. In a broader sense, piracy can represent a whole range of intellectual and physical robbery. Like what the traditional usage of this term suggests, the theft committed by ruthless sea barbarians in the early 1700s is analogous to the present day methods to wrongfully acquire or distribute copyrighted material. Yes, the recent surge in pirated Pirates of the Caribbean films is, least to say, ironic.
The main driving force behind the argument against piracy centers on the degree of copyright infringement. The creator of a new piece of work has exclusive rights or ownership over all individual products of labor. Exclusive rights include, but are not limited to, distribution, reproduction, the ability to perform and make derivatives of the original. Under United States and most foreign law, copyright infringement is the unauthorized use of any works or materials secured by copyright. Piracy impinges on the copyright ownerâs exclusive rights without a license to do so and thus is considered a form of copyright infringement.
Why are copyrights necessary? Copyrights and the consequences of copyright infringement not only help protect intellectual property and ownership but also benefit society as a whole. By prohibiting duplication of new products and ideas for a designated period of time after creation, these laws prevent third party profiteers from stealing intellectual property and making a living from the hard work of others. Copyrights provide sufficient incentives for individuals to embark on revolutionary research, make their discoveries, and present their own creations without having to worry about ownership issues. These laws promote society's scientific and intellectual progress while piracy works as the counterforce.
Currently, the piracy problem spans many corporate sectors. The MPAA, RIAA, ESA, and SIAA, representing the movie, music, gaming, and software industries respectively, have all taken drastic measures to cope with the repercussions from illegal sharing of their clientsâ copyrighted works. Besides publishing annual damage reports that rave about the millions upon billions of lost profit and issuing pre-litigation notices to known violators, industries have begun collaborating with educational companies to bring piracy awareness into schools.
Although some critics of these so-called âprofit seekingâ businesses frown upon the use of educational programs designed by paid business partners, the piracy-ridden industries are targeting the right demographics. [1] [2] As studies conducted by third party researchers show, up and coming generations of digital natives are more prone than any other age group to experiment with and actually commit piracy. In a 2006 study, L.E.K. consulting group found the typical internet pirate is a male between the ages of 16 and 24. They reported, â44 percent of MPA company losses in the U.S. are attributable to college students.â [3] Growing up in an environment immersed with different technological facets, digital natives confront the copyright issue much earlier in childhood. More and more of our youth are desensitized about piracy and intellectual property rights at younger ages. In a recent PEW study, researchers found that around half of the young students interviewed were not concerned with downloading and sharing of copyrighted content for gratis. Teens who download music online agree, âitâs unrealistic to expect people to self-regulate and avoid free downloading and file-sharing altogether.â [4]
Overview
Technological advancements in years saddling the new millennium brought sweeping changes to the way data is transferred across the world. The rapid increase in the availability and acceptance of broadband internet connections has allowed people from the far reaches of the globe to download large multimedia files at much faster speeds than ever before. Sharing files between computers became easier for the general population to understand. The once dominant UseNets and IRC channels slowly gave way to user-friendly graphical user interface (GUI) peer-to-peer (P2P) programs where anyone can make a simple search to produce desirable results. Emerging technologies such as Wikis and BitTorrent coupled with old tools like email and instant messaging provided additional techniques where information can be transferred from one client to the next. Finally, the adoption of standardized media formats improved the sharing experience as a whole. All of these changes, old and new, provided the foundations for the present day's pervasive illegal distribution of copyrighted material.
Classifications
Since the piracy problem is pertinent across many fields, the definition of this term and possible classifications have been extremely controversial over the years. While members of the justice system used piracy and theft almost interchangeably, people on the other side of the aisle view this practice as a grand exaggeration of reality. To them, it is unfair to compare downloading a song with real life thievery, or in this case, the carnage of 17th century sea "pirates." Even the organizations representing the large media and software industries do not have standard, unified definition for what they are fighting. MPAA defines piracy as "a serious federal offense." As for the different kinds of piracy, MPAA only mentions "internet piracy of movies, DVD copying, illegal sales and theatrical camcording." To the ISAA, "making additional copies, or loading the software onto more than one machine, may violate copyright law and be considered piracy." RIAA defines piracy as "the illegal duplication and distribution of sound recordings." Each organization is representing its respective industry, only showing pertinent consumers mere pieces of the puzzle. A definitive, yet agreeable definition for piracy and an universal way to classify the many faces of this issue are needed.
Piracy can be classified into two categories - digital and physical. Digital piracy is the illegal duplication and distribution of copyrighted content via electronic means. While the usage of online (peer-to-peer) P2P networks is the most pervasive outlet of digital piracy, hosting copyrighted files such as MP3s, movies, and software on web servers, uploading copyrighted media on video sharing sites, and even simpler ways of distribution such as via email or instant messaging are also considered illegal digital piracy. Similar to digital piracy, physical piracy involves the illegal duplication and distribution of works, but in physical form. Digital media can be illegally burned onto mediums such as CDs, DVDs and sold for a fraction of the retail price. Books, newspapers, magazines, course packs, journals, research and reports can also be duplicated in physical form and distributed. In fact, the MPAA reports, for 2005 "62 percent of the $6.1 billion loss result from piracy of hard goods such as DVDs, 38 percent from internet piracy." [5] Physical piracy of media and other forms of content are much more pervasive on a global scale. This method of copyright infringement can be further classified into individual license, corporate to end-user, reseller and distributor violations.
Categorizing piracy by methodology only answers the "how" question. "Why" people pirate can be grouped by a measurement of intentionality. Kids and adults alike have different reasons for why they choose to download from P2P networks or buy counterfeit media. Some, however, are quite unaware of their actions while others are completely oblivious between what is right and wrong. In a recent ZDNet report on UK businesses running Windows, "Microsoft would not put a figure on how much it loses from unintentional piracy, but said that while 85 percent of UK small businesses run Microsoft software, only 15 percent pay for it." [6] All of this, of course, hinges on intentionality. Individuals who are completely aware of their actions are considered director facilitators of digital or physical piracy. From the acquirers of prerelease content, to the online intermediaries, from the distributors to the customers, this group includes people anywhere on the piracy chain. Intentional piracy usually involves some sort of monetary gain at the loss of the copyright holder. Individuals somewhat aware of piracy are usually consumers of counterfeit content. They understand to an extent what they are doing is wrong but choose to go ahead with it for various reasons such as personal enjoyment or curiosity. Educating these indirect facilitators the wrongs of piracy is the recording industries' best chance at curbing this problem. Finally, consumers completely unaware of piracy are usually those who are victims of counterfeit scammers or those whose computer or personal network has been hijacked to illegally contribute copyrighted material.
Origins
In the last millennium, there were only a few landmark innovations affecting the dissemination of media content. Gutenbergâs invention of the printing press in 1450 allowed for easy and inexpensive duplication of paper works. With the assistance of moveable type, productivity of scribes (now hired machine workers) increased exponentially. As profit margins shot through the roof, the publishing industry was born. In the late 1970s, early 1980s, the introduction of the Sony Walkman gave humans the capability to record audio while the videocassette system did the same for video. In the 1990s, the popularization of CD/DVD optical disk technology gave birth to the new era of digital recording. The 21st century ushered in the acceptance of new digital mediums. Combined with the enormous success of the internet, computers and newly developed network protocols took information sharing to a new level. Each one of these new "machines" included a "mechanism" for which a certain "media" was affected. Each innovation established or revolutionized an industry. Each provided a faster, even better way to spread information. Each, however, brought with it intellectual property issues, for each forced or is forcing policy makers to amend copyright standards.
| Media | Mechanism | Machine |
|---|---|---|
| Paper | Movable Type Publishing | Printing Press |
| Cassette/VHS Tape | Magnetic Recording | Walkman/VHS Machine |
| CD/DVD | Optical Disk Recording | CD/DVD Recorder |
| Standardized Computer Files | P2P/Torrent Networks | Personal Computer |

On June 1st, 1999, Shawn Fanning, a student from Northeastern University, released what would be called "the godfather of peer to peer programs" â Napster. At that time, although there were other technologies facilitating the sharing of media, "Napster specialized exclusively in music ... and presented a user-friendly interface." [7] Soon after being launched, this easy to use, cost-free program became wildly popular because everyday computer users had enough basic technical knowledge to contribute to the file sharing movement. Napster's sensation, however, was short lived. Its "facilitation of transferring copyrighted material raised the ire of the Recording Industry Association of America (RIAA), which almost immediately â in December 1999 â filed a lawsuit against the popular service." [8] Because Fanning earned profits through advertisements and operated the project via a client-server protocol with a centralized file list, the RIAA push for intentional copyright infringement ultimately succeeded.
Napster's immense success planted the seed for today's P2P debacle. On one hand, this innovation sparked the countermovement by the RIAA and other recording companies to curtail infringement. On the other hand, Fanning's concept of dedicated media distribution GUI programs inspired next generations of P2P coders to create iterations of the Napster design even more insusceptible to the current copyright laws. The 1986 "Betamax case" allowed Sony to manufacture VCRs "because the devices were sold for legitimate purposes and had substantial non-infringing uses" (Betamax). In the cases brought up against these new P2P projects, even though the prosecution was successful in proving the Betamax argument invalid, the victory in the courtroom only fueled the rapid spawning of new P2P projects.
In March 2001, the FastTrack protocol allowed for a more distributed network without a centralized sever. Faster computers in the network now has the ability to become supernodes, or machines with server-like capabilities to help out slower clients. Newer P2P programs like KaZaa, Grokster, and iMesh successfully implemented this protocol and gained millions of users. Two years later, "FastTrack was the most popular file sharing network, being mainly used for the exchange of music mp3 files. Popular features of FastTrack are the ability to resume interrupted downloads and to simultaneously download segments of one file from multiple peers." [9] During the same decade, true distributed network protocols such as the open source Gnutella and eDonkey 2000 also caught on with mainstream P2P file sharers. Likewise spawning other P2P clients, Limewire, Morpheus, and eDonkey. Compared to Napster, these newer networks were able to attain higher maximum speeds because every client also had the capability to share files. Also, since the copyrighted material were stored on individual computers, with the proper disclaimers, the P2P client companies were able to brush off the majority of legal accusations.
The acceptance of the mp3 format in the mid 1990s allowed users to compress songs into several megabyte files, all of which were easily distributable throughout the digital world. In the early 2000s, DivX, a newly developed video compression codec did the same for video. As more households switched over to broadband internet, the ability to transfer large files finally became plausible. However, even with DivXâs help, typical compressed DVD rips still hovered above 600 MB. Since traditional P2P protocols could not handle the new bandwidth demand efficiently, a newer distributive protocol called BitTorrent was quickly adopted.

BitTorrent was developed by Bram Cohen in 2001. By splitting large files into sizable pieces, data can be widely distributed and shared "without the original distributor incurring the entire costs of hardware, hosting and bandwidth resources." [10] For a client to download additional data, one must supply requested chunks of the larger file to newer recipients. Cohen's implementation not only proved to be incredibly efficient, but also managed to exploit a legal loophole. While the initial releases of the BitTorrent system depended on trackers to operate, these servers answered the requests clients only by giving them the location of other computers who are concurrently sharing the same sought after file. Since tracker servers did not host any of the copyrighted content, the prosecution had a harder time shutting down these organizations. BitTorrent soon grew to become the sharing mechanism of choice.
Digital piracy only constitutes a portion of the whole picture. True, today's extensive counterfeit CD/DVD markets are largely fueled by the established presence of piracy in the digital realm. Resellers and distributors usually get the content to copy from online sources. But, the history of physical piracy can be traced back to the days of floppy disks and cassette tapes. In 1964, the Philips company brought compact audio cassette technology to the United States. Although there were other magnetic cartridge technologies available, Philip's decision to license the format for free made compact cassettes the most accepted recording medium during this time. [11] In the 1970s and 1980s, cheaper multi-track recording mechanisms for artists and the consumer compact cassette boom prolonged the popularity of this new medium. The trading of these recordable cassettes among music fans across the U.S. and U.K. via the mail was dubbed "cassette culture." [12] Acceptance of floppy disk technology starting from the early 1980s provided users an easy way to copy computer related files. Copyrighted computer software and games especially could be easily duplicated using these disks. Of course, anti-piracy campaigns also started as a reaction to these new fads. The British Phonographic Industry, a music trade group in the 1980s, launched an anti-piracy campaign with the slogan "Home Taping Is Killing Music." Similar to the RIAA's concerns today, the BPI was afraid that the rise of a new recording medium (in their case, the cassette tapes) would hurt legitimate record sales. In 1992, the Software Publishers Association produced an anti-piracy campaign centered around a video commercial called "Don't Copy That Floppy." [13]
Current Methodologies
Advent of the internet and the rapid increase of personal computers means more people than ever before have the capability to share information online. Though these advancements give users unprecedented access to the world's data, enforcing proper copyright restrictions while allowing justifiable sharing freedoms have not been attained. Thus, many have pointed to these new technologies as the facilitators of so-called "digital piracy." Today, users employ many different applications and services to illegally transfer copyrighted material. Factoring intentionality out of the equation, this section aims to introduce these online trade tools.
Local sources
Highlights: Live Messenger, E-mail, YouSendIt, MyTunes
The easiest and often times fastest way a person obtains copyrighted materials is from local, direct sources. Friends, family members, classmates -- an individual's immediate relations are commonly the people one asks when in need of a song, copy of a TV show, or a recent movie. Popular chat software like Microsoft's Live Messenger, AOL's IM, even Yahoo Messenger all support some form of a file transferring mechanism allowing these exchanges to happen. A few clicks and a potentially copyrighted file is on its way. Thanks to the recent milestones in the email industry, ever increasing account quotas and attachment size restrictions removed the barriers for sending decent sized files via traditional email. As of June 2007, popular services like Google's GMail and Windows Live Hotmail offer 2 GB of free space. Yahoo Mail even went as far as offering unlimited storage. [14] For larger files such as bundled music albums and films that exceed the maximum attachment caps, users turn to dedicated file uploading services like YouSendIt. After the file is uploaded, a notification is sent to the intended recipient with a retrieval URL. Recently, programs like MyTunes managed exploit sharing capabilities of the widely used music player iTunes, allowing users on the same local network to share their music libraries. All in all, in these proposed cases, the user is obtaining material from known, local sources on an personal basis via the internet.
P2P networks
Highlights: Kazaa, eMule, LimeWire, the original Napster
Peer-to-peer (P2P) networks comprise of computers across the internet linked together with special file sharing protocols implemented by different P2P programs. Popular protocols vary by two qualities: centralization and structure. Centralized P2P network protocols, like one used by the first version of Napster, rely on dedicated severs to record client information and store pieces of the shared data. Newer, decentralized P2P networks like FastTrack (used by popular P2P programs like KaZaa and Grokster) depend on individual clients to relay information; each computer on the network can act both as the sender and receiver of traffic. The way in which computers are connected inside of a P2P network determines its structure. When a client joins unstructured network, the computer only has access to files shared by known sources, barring access from the rest of the computers. Trying to locate a rare file is a lot harder because of the connection limitations. Structured P2P networks have streamlined methodologies for unique searches. Using technologies like distributed hash tables (DHT), it is incredibly efficient to find a file on the other side of the web. The beauty of P2P protocols and client/server networks relies on its user base. The combined processing power and bandwidth capabilities of these networked computers provide unprecedented levels of digital resources. With enough contributers, people can easily find and quickly download every piece of digitized work ever made.
The original Napster was the first P2P program to achieve mainstream status. In 2001, the final ruling of the case A&M Records, Inc. v. Napster, Inc. found this file sharing giant liable for illegal "contributory infringement of plaintiff record company's copyrights." [15] Even though Napster was consider a P2P program, it worked in a far more centralized way. The A&M Records' lawyers had incontestable evidence showing the defendant's role in facilitating copyright infringement, for clients depended on servers to talked to other clients. After Napster's demise, other P2P applications using newer, more efficient P2P protocols found their place in this industry. Popular programs like KaZaa (FastTrack protocol), eMule (eMule 2000 protocol), Limewire (Gnutella protocol) employed more decentralized and more structured ways of data exchange. These iterations of the original design, thus in a sense, are considered true peer-to-peer technologies.
Torrent networks: Torrent indexers, trackers & clients
Highlights: ThePirateBay, MiniNova, µTorrent, Azureus
The Torrent network is another file sharing alternative. BitTorrent was developed by programmer Bram Cohen during the summer of 2001. [16] The main quality that sets BitTorrent apart from other P2P technologies is its ability to efficiently transfer large amounts of data quickly and efficiently. When a user downloads something via traditional P2P means, most of the data usually comes from a couple of individuals who are sharing the same completed file. Unlike KaZaa, eMule, and LimeWire, all data on the torrent network are broken up into small pieces and simultaneously shared by huge pools of users. Each individual's Torrent client has the ability to connect to hundreds of other clients who are sharing pieces of the same sought after file. The relationship between clients are symbiotic. In order for computers to download pieces of a file, they too have to share similar pieces with other computers. This forced reciprocity and piece-wise sharing technique provides noticeable boosts productivity and speed. A 2004 report from CacheLogic claimed "Online movie trading is skyrocketing, but onetime leader Kazaa is tumbling in use" Andrew Parker, CacheLogic's founder and chief technology officer said, "The overall level of file sharing has increased. Users have migrated from Kazaa onto BitTorrent." [17] Because computer users are increasingly downloading larger files like movies and software, in the first few years of this decade, P2P traffic on the internet surpassed all other types of data. [18]
There are three integral components of the Torrent system; each provides a specific function that is uniquely independent of the others. Torrent indexers like ThePirateBay and Mininova stores databases full of ".torrent" files which contain the locations of both public and private torrent trackers. These tracker servers help client computers loaded with compatible torrent programs like µTorrent and Azureus connect with other candidates from all across the web. While anyone can download from public trackers, there are exclusive invite-only private trackers that provide even faster connections. Clients act as individual nodes on the network; their main job is to communicate with other clients to trade copied pieces of the requested file until all the pieces are downloaded. An user commences a download by loading a small ".torrent" file retrieved from a torrent index site into the torrent client. The client then communicates to the given server(s) and retrieves a list of IP addresses where pieces of the same file are being hosted. In case a server is down or not responding, clients also have the ability to use DHT (Distributed Hash Table) and PE (Peer Exchange) technology to find the locations of other clients without the assistance of trackers.
Warez networks
Highlights: Astalavista.box.sk, Cracks.ms
Warez is technical slang that stands for a broad spectrum of online counterfeit content. Ripped computer programs, music, movies, books and any copyrighted content published in a organized but illegal fashion can be considered Warez. Underground organizations called "release groups" operate on a minute by minute basis in constant search for new, unreleased music albums and features film to push on the web. In a 2005 Wired Magazine article, Erik Malinowski describes the five step "trickle-down file-sharing" system. [19] He divides up the piracy chain into the insider, the packager, the distributor, the couriers, and the public. According to Malinowski, majority of the high quality content that reaches the internet prematurely originate from insiders. Appointed screeners, workers at optical disk manufacturing plants, and moles within the production industry feed unreleased copies of albums, films, or computer programs to these release groups. In return, these people are usually provided with monetary contributions and access to terabytes of high quality media stored on the release groups' servers. Once a copy of unreleased media content gets into a release group, packagers working non-stop to encode and compress the content into smaller sized, easily transferable files. The content is then stamped with the release group's name or logo, zipped with a NFO file or (information file) giving credit to a release group, and passed on to the distributor. On the digital end, most release groups have relationships with "topsites" or "highly secretive sites on the top of the online distribution pyramid." [20] When a topsite operator publicizes the file on its networks, couriers immediately begin pushing the package to more accessible P2P and Torrent networks for the public to access. On the physical end, release groups can simultaneously sell copies of unreleased content to disc piracy manufacturers all around the globe. Immediately, people in the counterfeit disc business will begin mass producing copied CDs/DVDs to sell to audiences on the streets.
Even though most insiders and people associated with release groups do not know their acquaintances in person, members of these select organizations develop strong bonds with each other, for getting a new piece of media into the public takes teamwork and precision. The race to be first at offering the latest copyrighted content stirs up immense amounts of competition among release groups. Once a copy of an publicly unavailable content reaches the web, the value of such file or files drops close to zero. Over the years these underground networks of moes, hackers, crackers, and rippers were dubbed "The Scene." [21]
Besides producing ripped films and other media, release groups also have been known for cracking licensed software. Instead of insiders, the these groups depend on software crackers to supply the goods. Reverse engineering programmers spend their days trying to figure out how to defeat embedded license protection mechanisms. Crack/CD-key aggregators like Astalavista and Cracks.ms store hundreds upon thousands of key generators, patches, and other forms of cracks for a wide range of software. Users who can't find a prepackaged release from BitTorrent often resort to this manual search method. Though, one must wade through a lot of pornographic content, spyware exploits, and virus ridden files before finding anything useful. For amateur computer users, the risk of endangering their computers' integrity by exposing them to these malicious sites is too great; thus, they turn to traditional legal means.
Web mediums: Media sharing & aggregation
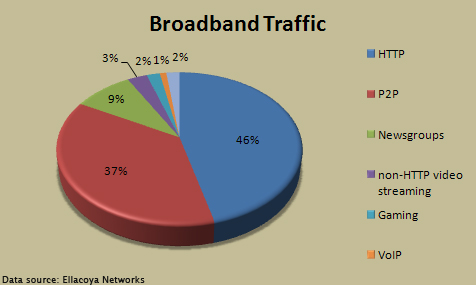
Highlights: Tv-Links.co.uk, PeekVid, YouTube, Veoh
With help from YouTube, online video sharing and streaming websites have caught on as top accessed online services among mainstream internet users. The analysis of internet traffic has always been a great way to measure the popularity of different protocols. For example, typical web browsing will amount to HTTP traffic. (When browsing the internet, notice websites usually have the letters âHTTPâ in front of the URLs.) Likewise, accessing FTP servers will generate FTP traffic, using P2P networks such as KaZaa or BitTorrent will generate P2P traffic, and so forth. For the first few years of the twentieth century, P2P data has dwarfed other forms of transferred traffic largely due to the immense popularity of music and video sharing. In a 2007 study, however, Ellacoya found âfor the first time in four years, P2P traffic finally fell behind HTTP. Chalk it up to YouTube and other Internet video sharing sites. The surge in HTTP traffic is largely a surge in the use of streaming media, mostly video.â Specializing in IP service control, Elacoya said, âBreaking down the HTTP traffic, only 45 percent is used to pull down traditional web pages with text and images. The rest is mostly made up of streaming video (36 percent) and streaming audio (five percent). YouTube alone has grown so big that it now accounts for 20 percent of all HTTP traffic, or more than half of all HTTP streaming video." [22]
YouTubeâs popularity comes with a cost. "New web sites are making it even easier for anyone who can click a mouse to access copyrighted content across the net. You no longer need to know your way around IRC or understand what a .torrent file is. Instead you can just stream them over any number of social video sites." [23] Since there are little to no physical restrictions that prevent users from uploading copyrighted content, individuals often times believe sharing an episode of Family Guy or Friends on YouTube is just. While some companies like CBS allow segments of their popular shows to be streamed online as means of free advertising, other TV stations and media networks retaliated in full force, taking Google's YouTube and Google Video to court. Since the start of the lawsuits two years ago, Google has "agreed to remove more than 100,000 video clips produced by Viacom properties, including MTV Networks, Comedy Central, BET and VH-1, according to a YouTube statement." [24] Of course without an extensive filtering system, people often find ways to sneak copyrighted content onto these services. A recent report titled "Is Google Promoting Video Piracy?" form the NLPC (National Legal and Policy Center) found "Google Video hosted apparently pirated copies of current major films as "Sicko" and "Evan Almighty." Both were posted without the permission or knowledge of the copyright owners. This follows a lawsuit against Google by media giant Viacom seeking $1 Billion in damages." [25] As of June 12th, 2007, Google is preparing to test it's video screen technology that will hopefully flag potential copyrighted material once they are uploaded. [26]
Other online video hosting companies like Veoh, VideoEgg, DailyMotion, GoFish are also stepping up their anti-piracy awareness in fear of lawsuits. Because of this, pieces of copyrighted content are scattered in random locations across the net. Video aggregation sites like the infamous PeekVid and recently popular TV-Links.co.uk compile these hard to find links into one location. In return for these services, these webmasters earn revenue from the pervasive amount of advertisements on their websites.
Conventional means: FTP, Webservers, IRC, USENET
Owners of web and FTP servers have the ability to publish copyrighted content accessible by the internet audience. Since most of these servers are rented by individuals for personal or small business use, these methods of distribution are much slower than dedicated file hosts such as YouSendIt. If something popular is discovered to be hosted on a non-password protected server, the surge in bandwidth during a short period of time can easily cause a system crash. Most of these uploaded copyrighted content stored for either backup or limited sharing among known relations. Unfortunately, search bots or page crawlers such as Googlebot, frequently indexes pages containing these files. There are certain searches techniques one can use to pull up copyrighted content such as songs, movies, or TV shows. Using IRC (Instant Relay Chat) Channels and USENETs to acquire copyrighted content still can be done, but definitely have fallen below main stream usage. Even though both methodologies prove to be extremely fast ways to download files, both require above average computer know-how and connections within online communities that share such content.
 |
 |
 |
 |
|---|---|---|---|
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
Every copyable form of media, from mass printing back in the 15th century to the cassette tape technology in the second half of the 20th century, was illegally exploited for profit. Before the popularization of digital formats and the increased accessibility of the internet, illegal distribution of physical copyrighted material was the prevalent form of piracy. Today's global physical piracy can be categorized into three sections: individual license violation, corporate to end-user violation, and reseller/distributor violation.
Individual license violation
The simplest form of physical piracy is committed by the everyday computer user. Factoring intentionality out of the equation, these transactions involve little to no net profit and is pertinent to all kinds of media. People who do not understand or do not care to understand licensing for a specific media product oftentimes overuse or misuse their given rights. Of course, different forms of media have different user agreements. A list of things one can and cannot do with a purchased DVD differs from what one agrees to when installing a computer program. True, some of these rights are innate. The ability to watch a DVD or start Microsoft Word whenever you want comes without question prepackaged in the original deal. After all, one is paying money for ownership.
Many restrictions concerning duplication and distribution, however, are not explicitly outlined in the perplexing user agreements. For example, installing single copy of a popular software on multiple computers is a perfect example of license overuse. The SIAA dubbed this behavior "softlifting." [27] Other forms of manipulative techniques for personal financial benefit are listed as follows. Falsifying one's identity to obtain additional upgrade features or manufacturer discounts, using academic or non-retail software for commercial purposes, copying/distributing licensed software and locked media with immediate relations are all considered individual license piracy. Because these interactions are on a local level, authorities rarely bother to trace this form of physical piracy.
Camcording is a huge issue the movie industry has to face on a daily basis. The term refers to the process where individuals capture featured films with portable recording devices. According to the MPAA, "ninety percent of pirated copies of movies are still playing in theaters. Once a camcorded copy is made, illegal movies often appear online within hours or days of a movie premiere." [28] Recently, stronger legislation have been put in place to discourage people from committing this crime. President Bush in 2005 signed the Family Entertainment and Copyright Act into law. It "makes camcording in a theater a federal felony and establishes new penalties for pirating works that have not yet been released commercially. First-time violators can be sentenced from up to three and five years in prison, and fined up to $250,000 for these kinds of crimes." [29] While some of the amateur camcorder pirates keep these recordings for at home viewing pleasure, most confront the risk for profit or other forms of personal gain. As mentioned before in a previous section, if the moles inside the movie industry do not leak the screener before a specific movie hits theaters, the release groups than depend solely on these lower quality camcorder versions to publish on the internet. These pirates also sell these recordings to "illicit source labs where they are illegally duplicated, packaged and prepared for sale on the black market, then distributed to bootleg dealers across the country and overseas. Consequently, the film appears in street markets around the world just days after the US theatrical release and well before its international debut." [30] In this case, these camcorder pirates can also be categorized in the reseller/distributer group because they are also a vital part of that physical piracy chain.
Corporate to end-user
Corporate to end-user piracy involves the misuse of software licensing within businesses and other organizations, such as schools, universities, and government funded programs. Unlike individual license piracy, the misuse of software licenses in this case are backed by the administrations representing these respective institutions. In the process of increasing productivity by installing better software while keeping costs to a minimum, the higher ups sometimes overlook the obvious legality issues behind allowing the proliferation of intangible things like computer programs.
There are three main forms of corporate piracy. The first form involves installing single-licensed software on multiple computers. Like individual license overuse, when company IT departments hands out free copies of Office 2007 or Adobe Photoshop to their employees, the end-users are benefiting at the loss of Microsoft and Adobe. Many organizations chose to buy volume licensing for expensive software titles. Because it is fiscally inefficient to purchase a copy of software for every single employee, companies oftentimes use keyed servers & keyed programs to reduce costs. This way, only a set amount of licenses needs to be bought for a bigger pool of users; however, thanks to the management of the keyserver, only that set number of users can access this program at any given time. Client-server overuse occurs when this keyserver fails to control the number of people who can access a program at the same time. Finally, hard-disk loading means illegally installing licensed software on computers' hard drives before they are given to employees or sold to costumers. Again, in this case, the end-user is put in a situation where they are unaware that their usage of certain computer programs is unlawful.
Because corporate to end-user piracy improves profit margins (or increases losses from the perspective of the programmers) at a much larger scale than the illegal individual sharing of copyrighted content, the software companies have more incentives to seek compensations. Anti-piracy organizations specializing in hunting down software pirates such as the SIIA (Software & Information Industry Association) and the BSA (Business Software Alliance) have been assisting today's most prominent software companies like Apple, Microsoft, and Adobe fight this and other types of piracy for quite some time now. While both the SIIA and BSA publish reports concerning the latest piracy statistics worldwide, the SIIA even has elaborate online form for company whistle-blowers to report the misuse of software licensing within their organizations. There is even a up to $1 million reward depending on how the pervasiveness of piracy. [31]
Reseller and distributor
Over a period of 18 months, LEK surveyed 20,600 movie consumers from 22 countries and found "62 percent of the $6.1 billion loss (reported by the movie industry) result from piracy of hard goods such as DVDs, 38 percent from internet piracy." [32] Despite recent telecommunication advances and increasing numbers of broadband computer users, compared to online digital piracy, physical piracy still plays a larger role in the global piracy market. The reason for this phenomenon is largely due to the well built infrastructure and well engraved ideologies in select regions of the world. People in countries like Armenia, Moldova, and Azerbaijan, where over 90% of the software are obtained illegally, do not believe in paying for software. [33] Lifetime habits, after all, are hard to change. Of course, larger piracy-ridden countries like China, India, and most of Southeast Asia also play huge roles in fostering the continual growth of this illegal act. Resellers and distributors of copyrighted material contribute to the largest portion of today's worldwide physical piracy.
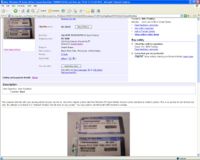
Unlike corporate and individual piracy, resellers and distributors work in closely knit, well built networks of sellers and buyers, all of whom have the ultimate profit seeking goal in mind. In a way, these collections of physical pirates analogous to the previously discussed online release groups. With speed and style in mind, these people deliver top notch replications of the latest unreleased content in a matter of hours after something is leaked. Reseller and distributor physical piracy can apply to all different forms of media. From software to movies, from music to games, all digitally formatted content have the risk of being physically copied and sold. Selling copied or counterfeit software for a reduced price as street vendors or in counterfeit stores, running unlicensed movie theaters or rental facilities, illegal direct resell and auctions of improperly licensed media are all considered physical piracy.
Case Study #1: What is wrong with this picture?
In this eBay auction, the seller is attempting to sell a valid Windows OEM license. He states in the description of the auction "the computer died but your winning bid the license can live on. Since the original system died, this Windows XP Home Edition license can be activated on another system. This is an auction for one license key only. No software is included. It is branded Toshiba but will work on any system. You may need to call Microsoft's 800 number to activate." Whether or not the seller made a genuine offer is besides the fact, for when one posts the a readable picture of the serial number, what is there left to "purchase"? $39.95 is a heavy price to pay when one can just copy down the number. Surprisingly, there were 12 bids on this auction when this screen shot was taken.
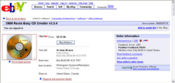 |
 |
 |
 |
|---|---|---|---|
 |
 |
By understanding methodologies behind these commonly used utilities and practices, we can have a better understanding of piracy's role in the lives of digital natives.
Piracy & Law
The chain reaction that instigated copyright regulations dates back to the fifteenth century. Gutenbergâs printing press marked the beginning of a new era of information distribution. True, this device facilitated the mass production and dissemination of human knowledge; however, it also carried repercussions. The formerly tedious task of duplication by hand was sped up to a rate that warranted tighter controls. When this technology arrived in England, the "need for protection of printed works was inevitable." [34] In 1710, the English Parliament passed the first official law concerning copyrights. The Statue of Anne "established the principles of authorsâ ownership of copyright and a fixed term of protection of copyrighted works." [35] Almost three hundred years have elapsed since this passing of this statue. Although some ideological remnants still remain, todayâs US copyright law "has been revised to broaden the scope of copyright, to change the term of copyright protection, and to address new technologies." [36]
Present day US copyright regulations stemmed from the first days of nationhood. When Americaâs founding fathers composed the United States Constitution in 1787, they gave Congress the power "to promote the progress of science and useful arts, by securing for limited times to authors and inventors the exclusive right to their respective writings and discoveries." [37] This line of text in Article I, section 8 bestowed upon the State fundamental rights to a monopoly over the copyright industry. It was the governmentâs job to asset, distribute, and control all copyrights. "The First Congress implemented the copyright provision of the U.S. Constitution in 1790," modeled quite similarly to the Statue of Anne. [38] Since then there had been three major revisions which occurred in the years 1870, 1909, and 1976.
With arrival of the digital age, Congress amended the copyright act to "prohibit commercial lending of computer software" in 1990. [39] This revision did not solve all the problems, for technology was evolving at a rapid pace. Computer savvy individuals were finding ways to bypass government copyright regulations. For example, under copyright laws up to the No Electronic Theft (NET) Act of 1997, people who intentionally distributed copyrighted software without receiving monetary benefits could not be prosecuted. The NET Act amended this loophole. [40] Following NET, 1998 was also a big year for copyright in the technological realm. The â98 Digital Millennium Copyright Act (DMCA) laid the foundations for RIAAâs cases half a decade down the line. Besides making "it a crime to circumvent anti-piracy measures built into most commercial software," the DMCA most importantly "limits internet service providers from copyright infringement liability for simply transmitting information over the internet." [41] Known as the "safe harbor provision," DMCA Title II (OCILLA) creates a "safe harbor" for internet service providers (ISPs) from being liable for content stored or transmitted via their servers as long as they take swift steps to remove the copyrighted content when asked. This Online Copyright Infringement Liability Limitation Act also gave plaintiffs the right to subpoena user information from the ISPs to carry out individual lawsuits.
As of January 2007, there are two portions of the United States code detailing domestic copyright regulations. USC Title 17 provides a comprehensive breakdown of every copyright guideline while section 2319 of Title 18 lists possible consequences for criminal infringement of a copyright. Under these laws, not everything conceived by the mind is eligible for copyright. According to chapter 1 section 102 of Title 18, the United States copyright law protects "original works of authorship fixed in any tangible medium of express." [42] This includes "literary, musical, dramatic works, pantomimes, choreographic, pictorial, graphic, sculptural works, motion pictures and other audiovisual works, sound recordings, and architectural works." [43] Ideas, not yet formulated on such "tangible mediums," thus, do not qualify. When a work is classified as copyrighted, section 106 of chapter 1 gives only the proper owner of the work the rights to reproduce, prepare derivate works, distribute, publicly perform, and publicly display the creation. In addition, these exclusive rights must be granted by the owner in order for third parties to use the copyrighted material.
When one or more exclusive rights such as the ones listed above have been breeched by an individual or a corporation, this respective party is considered to have committed a "copyright infringement." Although there are limitations to the power of these exclusive rights, such as cases where the violation has been deemed legitimate under the four conditions of "fair use" or other exceptions for special educational organizations, in most cases where the copyrighted content has been duplicated and/or distributed without the prior consent from the owner, infringement most likely occurred.
Consequences for infringement vary from case to case. The prosecution may choose to sue for measures at its discretion; however, the US Code does outline maximum and minimum sentences for different scenarios. Section 504 for Title 17 allows for the plaintiff to charge the defendant for actual and statutory monetary damages. Detailed evidence proving losses directly linked with the case is needed to recover actual monetary damages. As for statutory damages, the allowable compensation range from $200 to $150,000 per each infringed copyrighted work. If the prosecution can further prove that the defendant has used the copyrighted material either "for purposes of commercial advantage or private financial gain" or have reproduced or distributed content "which have a total value of more than $1,000," criminal charges found in section 2319 of Title 18 may apply. According to this section of US Code, if the defendant has been found in violation of copyright for personal financial gain, the maximum sentence is 5 years imprisonment for the first offense. Similar subsequent offenses carry 10 years imprisonment per offense. If the defendant has been found in violation of copyright for which the content had a total value more than $1,000, the maximum penalty is 3 years imprisonment for the first offense and 6 years for each additional offense in the future. These criminal charges are additions to monetary damages incurred from section 504 and even possible attorney fees of the plaintiffâs party from section 505 of Title 17.
Fair Use
The United States Fair use doctrine is a method of defense that can be employed when an individual is being accused of copyright infringement. Fair use allows for legal incorporation of copyrighted content in a new piece of work without prior agreement from the original author. [44] United States Code, Section 107, states usage of another's work "for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright." However, because this law can be applied to situations with drastically different circumstances, the ruling of a specific case is hard to discern. To solve this problem, Section 107 "Limitations of exclusive rights" lays down four factors to be considered when judging the validity of Fair use: "the purpose and character of the use, including whether such use is of a commercial nature or is for nonprofit educational purposes; the nature of the copyrighted work; the amount and substantiality of the portion used in relation to the copyrighted work as a whole; and the effect of the use upon the potential market for or value of the copyrighted work." [45] The judge presiding over a case involving Fair use must weigh these four factors in a balancing test.
| Fair use | Copyright infringement |
|---|---|
| Advances public knowledge | Fails to do so |
| Transformative use | Less transformative use |
| Little to no commercial use | Commercial use |
| More creative, less purely factual | Less creative, more purely factual |
| Copying published works | Copying unpublished works |
| Small portions of the work copied | Huge portions of the work copied |
| Derivative work does not harm potential market | Derivative work harms potential market |
There are four main factors that determine whether or not a case can qualify as fair use. Factor one -- "purpose and character" states, if the usage of a work advances public knowledge, is very transformative, and has little to no commercial purposes, then it is easier to argue for fair use. Factor two -- "nature of the copyright work" states, more creative, less purely factual usages of published works have stronger protection against copyright infringement. Copying unpublished works without the author's consent usually weakens the defendant's case for fair use. Factor three -- "amount and sustantiality of portion defendant used" is more straightforward than the first two factors. The larger the portion of copyrighted work used, the more prone the ruling will be in favor of copyright infringement and vice versa. The final factor -- "effect of defendant's use on potential market of copyrighted work" plays the most important role in determining the right to Fair use. If the derivative work endangers the original work's potential market opportunities, then the court will most likely be in favor of the prosecution. Criticism or parodies that may put the original work in a bad light are allowed even though it might damage the potential market. [46]
Piracy Among Digital Natives
Reasons for Piracy
- Saving time & money
- Digital natives are used to having immediate access to digital media. They aren't familiar with having to go to a record store and buy the latest CD or even having to record on a VCR a favorite show -- they can get the materials almost as quickly as they come out.
- Supply & demand + youth popularity
- Method of self expression
- Curiosity & standing trends
- Weak repercussions
- Online disinhibition effect
- Anonymity
Online Piracy: The Ultimate Generation Gap, 2003
- FOX News report on youth piracy
"The generation before us had to pay for music," said recent college grad Joshua, 24, of New York City. "Now you have no reason to purchase the music or movie in physical form. Everything is digital."
"Kids really don't care," said college freshman Ben, 18, of Upper Nyack, N.Y. "We all copy music and download movies because the chances of them cracking down on us specifically are slim."
"The lawsuits are both futile and counterproductive," said Fred von Lohmann, senior staff attorney at the Electronic Frontier Foundation. "Not only will they not stop file sharing, but they'll alienate customers."
"We're hopeful we haven't lost this generation," said Bob Kruger, enforcement vice president of the Business Software Alliance, which fights software piracy.
"It makes me feel kind of bad â like, 'oh no, I'm doing something illegal,'" said Melissa, the Florida teen. "I'm probably downloading a little less."
Charismatic Code, Social Norms, and the Emergence of Cooperation on the File-Swapping Networks
- Strahilevitz's analysis of P2P networks
"Virtually everyone who participates in one of the file-swapping networks is breaking the law in the process. Ordinarily, people are unlikely to trust lawbreakers, especially anonymous lawbreakers. Yet a remarkable sense of trust permeates these networks. ... [I]t is possible to observe significant levels of cooperative behavior, very little by way of destructive behavior, and substantial trust among the anonymous users of these networks. Furthermore, the networks have survived and thrived largely because of their users' dogged willingness to engage in unlawful activities."
Charismatic code-- "a technology that presents each member of a community with a distorted picture of his fellow community members by magnifying cooperative behavior and masking uncooperative behavior."
- "the applications harness the actual members of the community to become actors for norm enforcement purposes by magnifying the actions of those who cooperate and masking the actions of those who do not"
- "the applications act as a substitute for the community of actors and enforcers, inculcating in their users those norms most likely to lead to the success and expansion of the networks"
- "the applications act as a substitute for the community of actors and enforcers, inculcating in their users those norms most likely to lead to the success and expansion of the networks"
Distorted image-- (Gnutella network) "Charismatic code is the primary tool in that effort. Because of the way the networks are structured, the actions of those who share content are quite visible, while the actions of those who do not share content are virtually invisible. ... The architecture of the networks is such that although many users on the networks do not share, the networks create an appearance that sharing is the norm. This dynamic - the magnified visibility of sharers and the invisibility of non-sharers - exists on every successful file-swapping application I have seen."
"By the same token, these affinities normalize file-swapping: Members of the file-swapping networks stop being identified as 'rogue software pirates' and start being identified as 'people who, like me, have excellent musical taste.'"
Reciprocity-- "Technologies that magnify cooperative behavior and mask uncooperative behavior can succeed by tapping into deeply held social norms. In this instance, the file-swapping networks have been successful in large part because they have managed to tap into internalized norms of reciprocity. ... The networks' creators are drawing upon reciprocal intuitions that their users are likely to possess. Once again, the software is designed to exploit those intuitions."
- MusicCity and KaZaa's upload/download page
- Forced reciprocity implementation in 2001
Piracy & Tech Culture
Newly developed technologies of the last decade are giving users unprecedented freedom and control over media. Since embracing novel technologies and keeping current with the latest trends are crucial to the cultural standard of digital natives, such innovations provided the foundations for today's piracy.
- Software innovations
- Fast, efficient transfer protocols
- User friendly file sharing applications
- Online advertisement system
- Software communications boom
- Hardware innovations
- The personal computer
- MP3 players
- Portable multimedia players
- Storage medium technologies
- "Hardware synergy"
At heart, below the layers of accessories and fancy gadgets, the youth generation of today are not so different from the previous generations. Your typical teenager has a rebellious streak. Such teenage mentality drives counter-mainstream adult ideologies, which incites piracy.
- Newspaper article concerning Canadian piracy
"Hollywood can help itself by doing business with iTunes Canada and providing a library of legal content to download. That, and some stronger legislation from Ottawa, would go a long way to keeping us honest."
"Based on a survey polling wired Canadians in February, we not only bootleg directly from the screen, but we also like to download pirated booty - a lot. A whopping 93% of those downloading movies in this country are doing so illegally. And it's not just tech-savvy teenagers. Nearly 50% are over age 46."
"And pinning it on in-theater theft seems to fly in the face of a 2003 study done by AT&T, which concluded that Hollywood was prone to insider attacks, which resulted in leaked screener copies of 77% of 312 movies studied."
"It's commonly known that Montreal is a hot spot," says Dewolde. "In Canada there's no law against camcordering, so it's hard to stop these guys. The worst they can get charged with is trespassing. It's a huge issue."
"At first blush, it looks as if Canadians are more liable to piracy than their counterparts in the U.S.," says Phil Dwyer in a release. "In reality, many of these illegal downloads are taking place because of the lack of legal alternatives. The market is more mature in the U.S., and the experience there shows that if you give consumers a legal, convenient and fairly priced alternative to piracy, the majority will use it."
"We're pretty polite pirates. Give us a legal way to download movies and you'll see a sea change. No doubt many people have looked longingly at the growth of content on iTunes before downloading that torrent."
- Transcript of a round table discussion about counterfeiting in general
Roz Groome - "What has been highlighted are the different strains of harm that are going on. Physical harm, financial harm and social harm - the connection between counterfeiting, piracy, organised crime and other antisocial behaviour. Then also, there is economic harm for the industries and to the Treasury, because no tax flows back on counterfeit goods. People need to realise that they are not just lining the pockets of the rich and famous. For every musical hit there are ten failures and most musicians do not earn what Robbie Williams earns. In terms of creativity, and in terms of ensuring that consumers pay for the product, it is important to ensure that the money flows back to the people who are responsible for creating it and many of those people will not be rich and famous."
Michelle Childs - "Jo has done some interesting research about the motivation of consumers to purchase counterfeit goods. It raises some interesting competition questions. When you are talking about motivation to buy fake DVDs, 56 per cent of respondents bought them because they wanted to see a film as quickly as possible. So perhaps consumers are giving market signals. Perhaps they are saying that some of the old ways of doing things, such as having windows for releasing DVDs in different markets or only releasing music in certain formats, are not what they want and are not going to work."
Jo Bryce - "The answer might be to fill that market gap, rather than to get tough with criminal sanctions."
"If anything, they seemed to believe that the rip-off that was taking place was in the price charged for legitimate goods, rather than the counterfeit ones."
Mike Smith - "The counterfeit manufacturing and duplicating of CDs and DVDs and selling them through markets is highly visible. But on the internet, your children, 17 or 18 year olds, are swapping files and it is not so freely visible."
Mike Smith - "These young people are music enthusiasts, so it is ironic that, by swapping and downloading these music files, they are hacking into the profits of the record companies and taking money that should, by rights, be paid to the songwriters and artists."
Mike Smith - "There is an argument that the future may perhaps not consist of record sales, except in a more niche, particularly high-fidelity market. Essentially music may be seen as a commodity, as a utility, as something that you get streamed to your mobile phone and that you can access constantly, wherever you go. Maybe you will pay a monthly subscription and get your music constantly coming into your life, so that it almost seems like a free commodity. What the record companies need to work out is how the people that are still manufacturing and marketing most of that music also manage to get paid for it - how our artists get paid and the people writing the songs get paid."
Mike Smith - "No. So there is a degree of education to be done. There is also, to a degree, an acknowledgement that we are trying to turn back the tide and we cannot; itâs too late. We need to acknowledge that this is possibly the future and we need to adapt our business practices to reflect that."
Roz Groome - "They will not, but I tell you who is concerned: their parents. We have conducted a massive litigation campaign against egregious uploaders. These are not people downloading, they are uploading. They are behaving like mini free retailers. They are making available thousands of files to millions of people, constantly. Everything is available on filesharing software; everything is out there. I have spoken to the parents and they are horrified. They have copied their CD collections on to their computers to enjoy them, to put them on their iPods or whatever. Then their children have come home from school and downloaded some file-sharing software on to the family computer system, which has then made available to the world their entire CD collection. Incidentally, it is not just their CDs but anything that happens to be in their shared drive. This can include the family photographs, the Expedia receipts; I have seen bank account details, it is all there. That is where consumer education needs to come in. The people doing this need to see the harm it is causing."
Jeff Randall - "Once you can access music for free, people assume it is free. They do not think it through and they do not really care. That would be my view. It is a terribly cynical view, but the music industry, clearly, is facing that problem because that is what people are doing."
Mike Smith - "The music industry has to adapt in order to survive. What we are trying to do with BPI is legitimate protection of our copyrights. We have to do that, but the world is changing dramatically, and the way that a record company gets its revenues is not going to be reliant solely upon sales of records. We are going to have to become music companies, not record companies, and we may come to look upon records as being a loss leader."
Mike Smith - "All this could be a positive force. The internet could be the best thing that ever happened to the music industry."
Repercussions
For those who download through peer-to-peer (P2P) networks, the MPAA and RIAA have brought up the many potential risks one faces when accessing these servers. In the parental resources section of the MPAA website, the organization warns about four dangers of P2P programs: âSubject users to pornography, open personal files on your home computer to strangers online, increase the risk of a computer virus, lure kids into illegally downloading movies and music, which can lead to jail time and finesâ [47].
The first three concerns the MPAA notes are typical risks users face when acquiring content through such systems. Many online hackers exploit the P2P search system for monetary gains. By analyzing the trends of high demand movies or music, these profiteers simply manipulate the file names of the viruses and malware they want to spread to match the names of popular song artists and movie titles. Average users who are unaware of these tactics often times are gullible enough to execute these masked programs without realizing the fileâs identity. Even the ever-popular P2P software Limewire admits to the existence of viruses and other harmful material on their networks. In its online FAQ, the programmers warn Limewireâs users, âif you attempt to download a virus-infected file using LimeWire, you will be vulnerable to any viruses contained in that fileâ [48].
In addition to harmful materials one can download, many of these free P2P programs are packaged with third party spyware programs that will slowly but surely retard the speed and reliability of a computer. Like the infamous AOL installation back in the day, a handful of these shareware clients come bundled with various harmful third party applications. By means of a deceptive installation wizard or simply packing other software with the executable, oblivious individuals get much more than what they originally wanted.
Finally, users face the possibility of legal consequences due to copyright infringement. Since most P2P search requests will pull up media across the whole copyright spectrum, the MPAA does not want children to get the impression certain copyrighted content can be acquired without charge. The legal consequences does not discriminate by age. From a warning to a petty fine of $200 to $150,000 and 5 years in jail, the potential cost of piracy is very real [49].
Solutions
Eliminating piracy in the foreseeable future is a next to impossible task. There will always be people seeking ways to circumvent laws for a variety of reasons. There is hope, however. Even though wiping out piracy is not feasible, reducing this theft of digital material can be accomplished.
Raising Awareness
- Getting the message across to the new generations of Digital Natives
It is human nature to want to fit in with the rest of the populace. For example, if the majority of Trevorâs peers does not condone or commit piracy, it is highly unlikely Trevor will spend Friday nights at home downloading the latest blockbuster for he will be at the movie theatre watching the film with his friends. Thus, it is necessary to embed piracyâs immoral ideologies as early as possible in the heads of rising digital natives.
Although the representatives of the entertainment industry are currently pushing massive anti-piracy educational campaigns onto the public sphere, their efforts are not enough. The facts about piracy need to be incorporated into public school curriculums across the country. High school government classes should stress the consequences of copyright infringement. Parents should take part in addressing the dangers of piracy before they teach their children how to use computers. With a solid piracy awareness educational program in place, next generations of internet users will be ready to make rational and informed decisions about electronic theft.
- Programs in place for kids in secondary schools
- Programs in place for college students
- Other information sources
- Opposing viewpoints
Improve Business Strategies
Steps the software, entertainment, and gaming industries can take to adapt to the stubborn mindsets of digital natives.
- Adapting to the new digital environment
- Embrace the inevitable online music movement
- Develop better technologies to aid sales
- Providing legal, more attractive alternatives
- Reduce material costs of current physical albums
- Renew incentives to collect
The main incentive to obtain pirated files instead of purchasing them from a legitimate seller is because of the undesirable high prices of genuine media. In a study conducted by the RIAA, the consumer prices of producing a CD nearly rose 60% between the years of 1983 and 1996. Fortunately, the price of blank CDs fell 40% during this period, otherwise âaverage retail price of a CD in 1996 would have been $33.86 instead of $12.75â [50]. The RIAA notes because âthe amount of music provided on a typical CD has increased substantially, along with higher quality in terms of fidelity, durability, ease of use, and range of choices,â not to mention todayâs insanely over the top marketing strategies, the prices of production has been consistently on the rise.
This price trend also is occurring in the DVD sales industry. With the DVD player penetration rate in American households up from 23.6% in 2001 to 76.2% in 2005, DVDs are definitely on demand [51]. The average price of a DVD title, however, rose from $20.52 to $21.35 from 2001 to 2005 while the price of blank DVDs were falling lower and lower [52]. Consumers who are always hunting for deals turn to free P2P services or cheaper pirated versions of media because the real stuff is simply too expensive.
- Good examples
- Apple iTunes Music Store
- The New Naspter
- BitTorrent and MPAA Join Forces [53]
Adjust Enforcement Techniques
Parts of this section were adapted from Chen Fang's freshmen seminar paper.
The RIAA announced in July 2003 its intent to start gathering evidence in order to sue end users for illegally downloading copyrighted content via file sharing networks. Several months later, the big day finally came. On September 8th, 2003, the RIAA issued the first 261 lawsuits in what was to become an onslaught of charges. By May of 2006, newspapers have reported "the RIAA had sued more than 182,000 individuals for illegal downloading of music." [54] Although there were several cases that were fought extensively by the defendants, on average, each suit was settled for around $3000. The Motion Pictures Association of America, an organization that serves "as the voice and advocate of the American motion picture, home video and television industries," was not far behind in its user litigation endeavor. [55] Around one year after the RIAA's announcement, the newly appointed CEO of MPAA, Dan Glickman, declared at a UCLA press conference that "the studios will begin suing online movie swappers in the next few weeks." [56] Commenting on the recording industry's pursuit of piracy, Glickman told USA Today - "we wanted to watch their progress first and have some time to evaluate options. In the short term, it caused them some problems, but long term they were helped greatly by the campaign."
Problems? Since the day the RIAA initiated its first wave of copyright infringement suits, there have been many complaints voiced by analysts over the practice of suing loyal consumers. Wharton legal studies professor Richard Shell proclaimed that the RIAA "has gone one step too far with its latest legal move. Industries have a completely different strategic relationship with customers than they do with rivals. And this sort of strategy does not play well in the court of public opinion." The questionable effectiveness of this controversial business strategy was hyped to an even higher level when some targets of the RIAA became simply ridiculous. Curious media networks, always hungry for another eye catching story, had a field day when people like Sarah Ward received her lawsuit in the mail. For some odd reason, Ward, a grandmother residing in Massachusetts was charged for downloading "hard-core rap music." [57] It turns out this wasn't the only obscure case, given that little girls and old grandpas were also part of the pool of 261 unlucky individuals hit by RIAA's first round of lawsuits. "Brianna Lahara, a twelve-year-old girl living with her single mother in public housing in New York City" and "Durwood Pickle, a 71-year-old grandfather in Texas" were both charged for downloading copyrighted content through illegal file sharing networks. [58] The profiling of stereotypically awkward individuals did not stop here. In the years following the first lawsuits, the RIAA had inspired many sardonic headlines - "RIAA drops case against mom; sues her kids", "RIAA Sues Deceased Grandmother," and "RIAA Sues Yet Another Person Without A Computer" just to list several examples. Though some of these cases did turn out to be mistakes, the majority of them actually were legitimate accusations. Nevertheless, the large majority of the populace on popular forums, blog sites, and the news media concur with Professor Shell's belief. In their opinion, chastising, ridiculing, and sometimes flat out mocking the RIAA's foolish actions made sense.
- Setting the examples (for the prosecution)
Setting Examples
A moderate level of user litigation theoretically is beneficial to the recording industry. However, the question of who should be sued is still left to be determined. Is it right to sue grandpas, grandmas, and little kids? Is it fair for the recording industry to issue the same settlement amount to a computer amateur who shared several media files and a computer guru who finally got caught? Contrary to popular belief, litigation of "innocent" little kids is in fact the right thing to do. Logically, this might not make sense, but if observed from a grander economic perspective, prosecuting downloaders who are sympathetic to the recording industries is the right way to go.
Currently, the RIAA has been known to mainly target uploaders or "individuals who were allowing others to copy music files from their shared folders." [61] The piracy awareness materials published by the MPAA have also suggested the movie industry is following somewhat the same policy. In a short video clip documenting what MPAA calls "the Piracy Avalanche," the narrator concludes with the following sentence: "By eliminating topsites, the Motion Picture Association is targeting Internet piracy at its source and putting a lock on the trigger of illegal downloading and distribution of copyrighted material worldwide." [62] "Topsites" according to the MPAA are centralized distribution centers where the chain of piracy starts. In their opinion, if these initial outlets of pirated material are taken down, then online movie piracy would be reduced a great extent. Although this hypothesis may be true, the execution of the plan is too far-fetched. The effort needed by the MPAA to terminate a topsite is far greater than the effort needed by a single computer-adept person to launch services in another location. Only with the full cooperation of governments around the world, will this proposal be successful.
In addition to the implausibility of targeting piracy at its deepest roots, the idea of suing domestic high uploaders also does not make sense. The RIAA claims that piracy "costs the music industry more than 300 million dollars a year domestically." [63] Although no one knows how this number is estimated, one fact needs to be clarified. From an economics point of view, the recording industry is only losing money when a user who originally intended to buy legal media forgoes this process to download illegally. A computer guru who never spent a single dime on the recording industry in his or her life technically does not count in this losses figure. Therefore, it is unwise for the MPAA and the RIAA to simply concentrate on people who upload a lot. To these individuals, getting a cease and desist notice from their ISP will not affect ideologies already imbued in their heads. On the other hand, if a computer novice who used to buy CDs and DVDs legitimately got the same warning, this wakeup call would much more likely turn them back into buying media the old fashioned way.
Line A shows a generalization of MPAA and RIAAâs current business practices. Assuming that computer gurus upload a lot more than a computer notice who is trying Kazaa for the first time, the number of lawsuits filed increases as computer experience increases. Instead of only concentrating on bringing down the uploaders, the recording industry should increase the number of lawsuits aimed at the first time user. If there was a way to use bots scanning P2P networks to keep track of the reoccurrence of IP addresses, at the optimum situation (line D), the number of lawsuits should be directed to both computer illiterate sympathizers who are using the P2P network for the first time and old school uploaders who are fueling the illegal material. With this two prong attack, the recording industry will not only curtail the spread of piracy but also instill fear using illegal mediums to acquire media in the community of customers. "How well law regulates, or how efficiently, is a different question. But whether better or not, law continues to threaten a certain consequence if it is defined." [64] The RIAA and MPAA should continue to use the powers of law to deter piracy.
Employing New Technologies
- Using technologies to their advantage
- Preventing Movie Piracy (Camcording) [65]
- DRM
Using the Masses
Covenant i-Fan Model
Although the architecture of the internet allows for programmers to construct P2P infrastructures, the same architecture can also be used to control or at least disrupt these networks. The most common countermeasure the RIAA and the MPAA have used is hiring third party security companies such as Covenant Corporation to upload false media files to discourage users from downloading. Covenant Corporation uses its own servers to mimic users on P2P networks, uploading unusable copyrighted files to unsuspecting downloaders. Through this i-Fan system, Covenant Corporation also encourages users to distribute these files through their personal computers.
Covenant took a step in the right direction but failed to produce the necessary results because of the poor user base. i-Fan offers its users "free money" to help intentionally disseminate these spoof files, however, does not guarantee everyone assisting this project rewards. Over the course of the past three years, only six winners have been announced. [66] So where can the MPAA and RIAA harness a big enough user base to start the anti-piracy movement? iTunes. As of 2006, Wired magazine reported that iTunes has over 200 million active customers. [67] If the MPAA and RIAA can convince Apple to tack on something like i-Fan into its iTunes program, the recording industry will have a lawful and practical method of bringing down P2P networks.
The figure above provides a visual representation of what "iTunes Advantage" adds on to the existing infrastructure. The larger circle on the bottom right hand corner is the existing P2P network. Today, the only spoof computers that upload senseless material into the P2P network are the ones hired by the MPAA and RIAA. With iTunes Advantage, every user currently in the iTunes community has the option of helping to stop piracy. If this plug-in is turned on, iTunes will use built in P2P protocol to upload corrupted content to select P2P networks. To make the deal even more attractive, the recording industries might provide certain amount of iTunes store credit for every megabyte uploaded. With cooperation from Apple, the recording industry can modify the architecture of the internet to stop piracy.
Hong Kong Youth Ambassador Model
If you can't beat them, recruit them. Instead of hiring professional corporations to implement sophisticated anti-piracy mechanisms and paying an army of lawyers to prosecute the few who are caught, the Hong Kong government launched a revolutionary new anti-piracy program consisting of today's most talented, internet-adept populace -- our kids. Starting on July 18th, 2007, "the Hong Kong government plans to have 200,000 youths search discussion sites for illegal copies of copyrighted songs and movies and report them to the authorities. The campaign has delighted the entertainment industry but prompted misgivings among some civil liberties advocates." [68] The Youth Ambassadors program consist individuals as young as 9 to scour the internet for links to illegally uploaded copyrighted content. Governmental officials announced, "all members of the Boy Scouts, Girl Guides and nine other uniformed youth groups here, will be expected to participate." "We are not trying to manipulate youths and get them into the spy profession," Tam said. "What we are just trying to do is arouse a civic conscience to report crimes to the authorities." [69]
Youth Ambassador program has three main goals. One, the program is aimed to promote the importance of intellectual property rights. "Educating youths to respect copyrights is a central goal of the program, officials said. "A lot of Internet piracy is done by young people, particularly in their teens, and the difficulty is it's almost becoming a fashion to download music, download video," said Joseph Wong, the Hong Kong secretary of commerce, industry and technology." Two, by hiring today's youth, government officials hope to expand its abilities to monitor illegal internet activity. And three, if enough reports come in, the government hopes to reduce the amount of illegal BitTorrent seeds available online. [70] This project "was one of the main campaigns in a series of publicity and educational programs for IPRs protection launched by Commerce, Industry and Technology Bureau on May 29" of this year. In this original pilot run, 60% of all postings to illegal content on forums have been removed. [71] Hong Kong is setting an anti-piracy methodology for the rest of the world to follow.
Embrace Policy Amendments
One of the main motivations behind piracy resides in the desire to bypass barriers to obtain rare or restricted commodities. Whether for professional, creative, or leisure use, people are in constant search for new pictures, music, movies, games and other digital fads. Recently in the United States, thanks to stronger copyright laws, it has become harder and harder to legally acquire these works without going through the hassle of obtaining the correct licenses. Although the ideas patented by private industries were never available for free, public consumption, the Copyright Law revision of 1976 changed the default copyright standards for creative works. Before this fateful year, when an author created a new work of art, it was not automatically protected by copyright unless the author officially applied through the proper government channels. After these legislative changes, "creative works are now automatically copyrighted." [72] Now copyright was applied by default, for "once someone has an idea and produces it in tangible form, the creator is the copyright holder and has the authority to enforce his exclusivity to it." [73] These alterations to the law restrict the number of works available in the public domain, increasing the incentives to commit piracy.
Free & Copyleft-Like Licensing
Long before the popularization of personal computers, the internet and the onset of digital piracy, programmers and users alike have supported alternatives to copyright. Although forcing all goods and services in a society be offered for gratis is an extreme solution to the piracy, the action will not only stifle innovation but also crumble a society's economy, thus its infrastructure to exist. Instead, the present copyright laws can be adjusted to better accommodate the creative needs of future generations. Copyleft is a copyright license spin off that allows for the modification of would be copyrighted content. Copyleft "removes restrictions on distributing copies and modified versions of a work for others and requiring that the same freedoms be preserved in modified versions." [74] Currently there are several notable movements that have been offering such substitute licensing options: Free Software Foundation's GNU GPL, Open Source Initiative's Academic Free License, Creative Commons License, and quite a few less popular licenses like MIT, BSD, Uol/NCSA, and Apache.
Free Software Foundation & GNU GPL

In 1985, Richard Stallman founded a non-profit organization called The Free Software Foundation. It is "dedicated to promoting computer users' rights to use, study, copy, modify, and redistribute computer programs." [75] Since its establishment, the FSF widely known for its free software advocacy. Besides publishing a very popular GNU GPL (GNU Lesser General Public License), FSF also released one of the first open source operating systems called GNU (GNU's Not Unix). Today, GPL is used by numerous software programmers and corporations as the official license for their software. Popular Wikimedia foundation's wiki projects are all released under the GNU Free Documentation License.
Open Source Initiative's & APL

After a decade free software policy promotion, the FSF's goals became distorted by the large amounts of actual "zero cost" software running under its GNU license. This made FSF look like an anti-commercial, anti-market organization rather than a outlet of free expression and free speech. Around 1998, a sect of the free culture movement followers gathered together to push for a less ambigous goal. These people "advocated that the term free software be replaced by open source software (OSS) as an expression which is more comfortable for the corporate world." [76] Founded by Eric Raymond and Bruce Perens in February 1988, the OSI (Open Source Initiative) "sought to bring a higher profile to the practical benefits of freely available source code, and they wanted to bring major software businesses and other high-tech industries into open source." [77] Raymond suggested the development of open source software should following his "Bazaar" model, which included the following traits: users treated as co-developers, early releases, frequent integration, several versions, high modularization, and dynamic decision making structure. Popular projects like Apache, Linux, Netscape, and Perl follow this model. Right now the Open Source Initiative serves as a "community-recognized body for reviewing and approving licenses as OSD (open source development) conformant." [78]
Creative Commons & CC License

Creative Commons is a non-profit organization that allows for âauthors, scientists, artists, and educators easily mark their creative work with the freedoms they want it to carry.â [79] Founded by Lawrence Lessig in 2001, Creative Commons offers free licensing to the whole spectrum of individuals from every corner of the media background. These Creative Commons licenses come in several different flavors, offering selective protections such as forbidden commercial use or mandatory sharealike distribution. They enable âcopyright holders to grant some or all of their rights to the public while retaining others through a variety of licensing and contract schemes including dedication to the public domain or open content licensing terms. The intention is to avoid the problems current copyright laws create for the sharing of information.â [80] By using CC Licenses, producers of what would be considered protected intellectual property can release their works to the public in confidence, for consumers will know exactly what they can and cannot do with the licensed work.
Unlike the GNUâs GPL, which is mainly used by programmers to license software creations, Creative Commons licenses can be applied to all kinds of media. CreativesCommons.org provides custom-made online tools and straightforward directions to help users license their work. Once a proper license is chosen, the online community has access to three editions â one laymenâs terms for regular users, one in legal writing for lawyers, and one in code for computers. Comprehensive translations are also available for international users.
Reflections
Numbers Tell the Story
- Discuss the latest trends among Digital Natives relating to how they perceive piracy
- Gender differences
- Social-economic differences
- Family influences
- Group mentality phenomenon
Kids: Stealing Digital Data OK, 2004
- Newspaper article reports the 2004 BSA findings (same study was redone in 2006 and once more in 2007)
"Youth admits it's illegal, but download music, movies, games anyway"
"Of the 1,100 eight to 18-year-olds polled, more than 80 percent know that music, movies, games, and software arc protected by law, and more than 60 percent know the same applies to Web sites. Yet 53 percent of kids still download music and more than a third download games. Only 22 percent of kids, however, steal larger files such as software and 17 percent copy movies. A measly 29 percent think illegal copying is wrong. No wonder. Eight percent say their parents approve of the activity."
"Kids cite a number of reasons for illegal downloading, from not having the money to pay for software (51 percent) to the rationale that "lots of people do it" (33 percent). Twenty-six percent also view file stealing as a victimless crime, saying it "doesn't hurt anybody."
"Interestingly, 59 percent of kids say their knowledge of intellectual property comes from television. Other sources include parents and the Internet (44 percent), and friends (30 percent). Teachers ranked dead last at 18 percent."
Study: Students Don't Understand Copyright Rules
- Small study conducted by 2 college professors find students don't understand copyright laws
"AU School of Communications Professor Patricia Aufderheide and Washington College of Law's Peter Jaszi polled 51 graduate and undergraduate students who upload videos and held more extensive interviews with 15 of them."
"The majority of students (87%) who upload copyrighted material to user-generated video sites likeYouTube, Facebook or MySpace don't get permission from copyright owners, even though most (74%) believe it is fair to pay people for their use."
"The study concluded that students were, "universally underinformed and misinformed about the law." While 76% of the students said that the Fair Use doctrine allowed them to use copyrighted material, none could accurately define the doctrine."
"While they were generally concerned with staying on the "good side" of the law, they were "making up rules themselves" about what and how to use intellectual property. They also did not understand their own rights as creators of content."
Students' justifications of why they copyright content:
- Sharing a file is like talking with colleagues near a virtual water cooler environment
- Putting "all rights reserved" on a copyrighted clip protects him from the owner
- Gives the owner of the copyright free publicity/advertisement
Illegal Downloading Among Youth Drops, Reports New Study
- BSA's 2007 study on youth piracy, shows piracy down from 2004
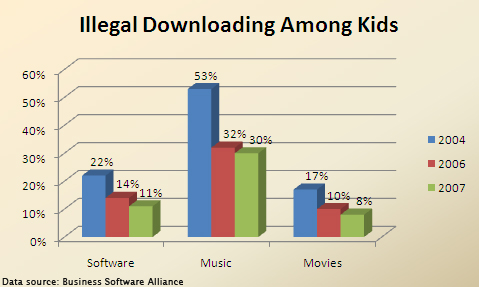
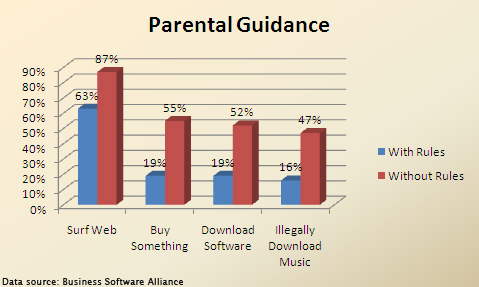
"The results of a recent nationwide survey released by the Business Software Alliance (BSA) show that illegal downloading of digital copyrighted works by youth (ages 8 to 18) has dropped by 24 percent in the last three years."
"The survey, first conducted in 2004, indicated that 60 percent of survey participants reported downloading software, music, movies, or games without paying for it; in 2006 the percentage of those who downloaded without paying dropped to 43 percent; and in 2007 the percentage decreased to 36 percent. Youth report that parental oversight is a significant motivator and key influencing factor in their online behavior."
Top factors that kids worry about when downloading digital copyrighted works:
- Fear of accidentally downloading a computer virus (62 percent)
- Getting into legal trouble (52 percent)
- Accidentally downloading spyware (51 percent)
- Fear of getting in trouble with parents (48 percent, increasing from 40 percent in 2006)
âThis study indicates that parents represent a growing and effective influence on the online practices of youth,â said Diane Smiroldo, vice president of public affairs for BSA. âBut, while decreases in downloading are encouraging over recent years, youth are still taking too many risks online. We hope that parents continue to take seriously their role in helping their children make the right choices online. Fortunately, the survey found that more than half of the students have been warned by their parents about dangerous, illegal online behaviors. Imposing rules and ensuring your children abide by them may be an old-fashioned concept for cyberspace, but it works.â
Illegal downloading among kids have dropped in recent years:
- 22% of kids illegally downloaded software in 2004, 14% in 2006, 11% in 2007
- 53% of kids illegally downloaded music in 2004, 32% in 2006, 30% in 2007
- 17% of kids illegally downloaded movies in 2004, 10% in 2006, 8% in 2007
Parental guidance plays a big role in kids' lives:
- 87% surf the web without parental rules, 63% with rules
- 55% buy something without parental rules, 19% with rules
- 52% download software without parental rules, 19% with rules
- 47% illegally download music without parental rules, 16% with rules
Other Side of the Debate
Is piracy really causing problems for the programming/entertainment industries?
- Russian teacher fined for MS piracy [81]
- When Piracy Becomes Promotion [82]
"The underground subtitling and circulation of Japanese anime helped to open the American market to Asian cultural imports."
"The global sales of Japanese animation and character goods, an astonishing 9 trillion yen ($80 billion) has grown to 10 times what it was a decade ago."
"The Cartoon Network features a wide array of anime series as part of its late night Adult Swim programming. ADV Films, a major importer of anime series for the American market, has launched a 24 hours Anime Network. TOKYOPOP, a Los Angeles-based company, will publish 400 volumes of translated manga (Japanese comics) for U.S. consumption this year. One can find whole shelves of manga in many Barnes and Noble or Borders bookstores, where they frequently outsell American-produced graphic novels."
"The clubs, such as the MIT Anime Club, functioned as lending libraries and dubbing centers as well as holding marathon screenings to attract new members."
"Japanese distributors winked at these screenings. They didnt have permission from their mother companies to charge these fans or provide the material but they were interested to see how much interest the shows attracted."
"Many U.S. media companies might have regarded all of this underground circulation as piracy and shut it down before it reached critical mass. The Japanese media companys tolerance of these fan efforts is consistent with their similar treatment of fan communities in their local market. As Temple University law professor Salil K. Mehra notes, the underground sale of fan-made manga, often highly derivative of the commercial product, occurs on a massive scale in Japan, with some comics markets attracting 150,000 visitors per day; such markets are held almost every week in some parts of the country. Rarely taking legal action, the commercial producers sponsor such events, using them to publicize their releases, to recruit potential new talent, and to monitor shifts in audience tastes. In any case, they fear the wrath of their consumers if they took action against such a well-entrenched cultural practice and the Japanese legal structure would provide for fairly small legal penalties if they did pursue infringers."
"More generally, as Yuichi Washida, a research director at Hakuhodo, Japans second largest advertising and marketing firm, has argued, Japanese corporations have sought to collaborate with fan clubs, subcultures, and other consumption communities, seeing them as important allies in developing compelling new content or broadening markets. In courting such fans, the companies helped to construct a moral economy that aligned their interests in reaching a market with the American fans desires to access more content."
- Piracy in developing countries
Piracy is no doubt a huge problem overseas. Although most countries have anti-piracy legislation in place, the enforcement of these laws are not up to par with global standards. Especially in developing countries where local governments have no incentives of protecting foreign intellectual property, whole industries have been built around the concept of illegally duplicating and distributing media for individual gains. The Motion Pictures industry in 2005 claimed that there were "more than 34,000 cases of piracy and assisted law enforcement officials in conducting more than 10,500 raids. These activities resulted in the seizure of more than 34 million illegal optical discs, 55 factory optical disc production lines and 3,362 optical disc burners, as well as the initiation of more than 8,000 legal actions." [83] Despite these proactive measures, MPA still projected a sum total of more than one billion dollars in lost potential revenue for 2005 in the Asia-Pacific region alone.
While the entertainment industry frantically tries to control piracy overseas, software businesses have a lighter view on this issue. Although software piracy is no better compared to media piracy abroad, there is less concern from the corporate side. In these developing countries, the biggest competitors for legitimate software companies are open source organizations. Since, software engineers are vying to attract a larger portion of the new population to use their product, strategists have have concluded piracy may actually help companies defeat the open source movement. Take the software giant Microsoft for example. It "acknowledges that piracy sometimes helps the company establish itself in emerging markets and fend off threats from free open-source programs." [84] In countries like China and India, even though a huge portion of the population operates on counterfeit versions of Windows and unactivated versions of Office, at the end of the day they are still using Microsoft made products. If the strategy to empower both the legitimate and illegitimate user base works out as planned, when a country's economy matures in the long run, the majority of the population will be more willing to buy Microsoft's genuine software. Just look at Vietnam, "which at more than 90% has the highest piracy rate in the world, has improved from 100% in 1994. The No. 1 software firm in Vietnam: Microsoft." [85]
The debate about whether or not severe anti-piracy measures are necessary in developing countries is an hot issue, for there are good supporting arguments for both parties. The value of a piece of software varies directly with the size of its user base. Without a substantial base of users, software products cannot survive. In these developing countries where the majority of the population cannot afford many of life's luxuries, asking them to dump several hundred dollars for a copy of Windows Vista is ridiculous. But, for every pirated of Vista bought Microsoft is loosing potential revenue. So, the final question to be asked is -- constituents a potential sale?
- Romanian President to Gates: Windows Piracy Built This Country [86]
Relevant Research
SIIA Anti-Piracy: What is Piracy?
10 Big Myths about copyright explained
The YouTube effect: HTTP traffic now eclipses P2P
Charismatic Code, Social Norms, and the Emergence of Cooperation on the File-Swapping Networks
Youth & Piracy
Majority of Youth Understand âCopyright,â But Many Continue To Download Illegally
Parents pick up piracy from kids
Online Piracy: The Ultimate Generation Gap
The Effects of Piracy in a University Setting
Study: Students Don't Understand Copyright Rules
Illegal Downloading Among Youth Drops, Reports New Study
Youth & Technology
US youths use internet to create
PDF: Teen Content Creators and Consumers [87]
Anti-Piracy
Anti-Piracy Gang Launches their own Video Download Site to Trap People
DRM-free iTunes Songs Have Embedded User Info, 2007
Darnstädt, T.: Die Gratis Kultur, in: Spiegel Online, 2007.
Organizations
(Software & Other Content) SIIA & the SPA: Anti-Piracy (SIIA Member List)
"SIIA and its predecessor organization, the Software Publishers Association (SPA), have the longest-running software anti-piracy program in existence. Started in the mid-1980s, SIIA's Corporate Anti-Piracy program identifies, investigates, and resolves software piracy cases on behalf of our members. As Internet-based piracy has emerged, SIIA again broke new ground and now has an extensive program for tackling software pirates operating over the Internet, ensuring that SIIA members receive the maximum protection possible."
(Commercial Software) BSA: Anti-Piracy (BSA Member List)
"The Business Software Alliance is the voice of the worldâs commercial software industry and its hardware partners before governments and in the international marketplace. BSA programs foster technology innovation through education and policy initiatives that promote copyright protection, cyber security, trade, and e-commerce."
(Gaming Industry) ESA: Intellectual Property
"The Entertainment Software Association (ESA) is the U.S. association exclusively dedicated to serving the business and public affairs needs of companies that publish video and computer games for video game consoles, personal computers, and the Internet. The ESA offers a range of services to interactive entertainment software publishers including a global anti-piracy program, business and consumer research, government relations and intellectual property protection efforts. ESA also owns and operates the E3 Media & Business Summit."
(Movie Industry) MPAA: Anti-Piracy
"The Motion Picture Association of America (MPAA) and its international counterpart, the Motion Picture Association (MPA) serve as the voice and advocate of the American motion picture, home video and television industries, domestically through the MPAA and internationally through the MPA. Today the association continues to advocate for strong protection of the creative works produced and distributed by the industry, fights copyright theft around the world, and provides leadership in meeting new and emerging industry challenges."
(Music Industry) RIAA: Anti-Piracy
"The Recording Industry Association of America (RIAA) is the trade group that represents the U.S. recording industry. Its mission is to foster a business and legal climate that supports and promotes our members' creative and financial vitality. Its members are the record companies that comprise the most vibrant national music industry in the world. In support of this mission, the RIAA works to protect intellectual property rights worldwide and the First Amendment rights of artists; conducts consumer, industry and technical research; and monitors and reviews state and federal laws, regulations and policies."
Stats & Studies
SIIA: 2006 Anti-Piracy Year in Review
BSA: 2006 Global Software Piracy Study: European Union
BSA: Fourth Annual Global Software Piracy Study
MPAA: 2006 US Theatrical Market Statistics Report
MPAA: International Theatrical Snapshot
MPAA: US Entertainment Industry Market Statistics
RIAA: 2006 Year-End Shipment Statistics
Pro-Piracy
Russian teacher fined for MS piracy
Profits from Piracy: Microsoft in China
Romanian President to Gates: Windows Piracy Built This Country
Pirated Music Helps Radio Develop Playlists
Possible Solutions
Suing Your Customers: A Winning Business Strategy?
Hong Kong enlists youth to fight piracy
Piracy in the News
Viacom the Latest Company to Misunderstand the Internet, Jason Kolb, 2007
YouTube-Viacom Page on TopTenSources, Various Editors, 2007
Viacom Terrorizes YouTube, Cory Doctorow at Boing Boing, 2007
LA Times: Is Copying a Crime? Well ..., 2006
Which Videos Are Protected? Lawmakers Get a Lesson, 2007
MPAA copyright victory is 'website killer', 2005
BitTorrent and MPAA Join Forces
Piracy stats don't add up, 2006
Indiana man jailed for selling counterfeit software on eBay, 2007
Movie Swappers Put on Notice, 2004
Poughkeepsie Online: Music Swappers Sued, 2003
In Court's View, MP3 Player is Just a 'Space Shifter', 1999
Anti-iTunes DRM demonstrations across the USA tomorrow, 2006
Apple, EMI Ink DRM-Free Music Plan, 2007
New law cracks down on P2P pirates, 2005
Is Google Promoting Video Piracy?, 2007
Top 50 Copyrighted Videos Google is Pirating, 2007
ISP Protects File-Swappers' Identities, 2007
AT&T moves to prevent Internet piracy on its network, 2007
Baidu faces new lawsuit over music piracy, 2007
NES piracy surfaces on Facebook, 2007
China, FBI Bust Piracy Syndicate, 2007
RIAA says lawsuits cannot be the complete answer to music piracy, 2007
Bill would force "top 25 piracy schools" to adopt anti-P2P technology, 2007
BBC News - Pop Star Prince gets togh on Web Pirates, 09.13.07
RIAA Pre-Litigation Letters
Targeted: 23 Colleges
State University of New York at Morrisville (34 pre-litigation settlement letters), Georgia Institute of Technology (31), Pennsylvania State University (31), University of Central Arkansas (27), University of Delaware (23), Northern Michigan University (20), Rensselaer Polytechnic Institute (20), George Washington University (19), Ohio State University (19), New Mexico State University (17), Eckerd College (16), University of Minnesota (16), California State University - Monterey Bay (14), University of Kansas (14), University of Missouri - Rolla (14), University of San Francisco (13), Case Western Reserve University (12), Northern Arizona University (12), San Francisco State University (12), University of Tulsa (12), Franklin and Marshall College (11), Western Kentucky University (11), and Santa Clara University (10)
Targeted: 19 Colleges
Dartmouth College (13 pre-litigation settlement letters), DePaul University (19), Drexel University (26), Northeastern University (10), Northwestern University (16), North Carolina State University (43), Rochester Institute of Technology (19), Stanford University (19), Texas Christian University (7), University of California - Davis (34), University of California - Irvine (23), University of California - Los Angeles (37), University of California - San Diego (9), University of California - Santa Cruz (15) , University of Chicago (18), University of Nebraska - Lincoln (33), University of Oregon (17), Western Washington University (15), and Wichita State University (22)
Targeted: 13 Colleges
Brandeis University (15 pre-litigation settlement letters), Duke University (35), Iowa State University (15), Massachusetts Institute of Technology â MIT (23), Northern Illinois University (50), Syracuse University (20), Tufts University (15), University of Georgia (19), University of Iowa (25), University of Southern California (50), University of South Florida (50), University of Tennessee (50), and the University of Texas - Austin (35)
Targeted: 22 Colleges
Bates College (7 pre-litigation settlement letters), Brown University (12), Central Michigan University (24), Colby College (5), College of William & Mary (12), Cornell University (19), Fairfield University (15), Florida International University (16), Indiana University (28), Keene State University (19), Kent State University (19), Morehead State University (10), Ohio University (50), Oklahoma State University (16), University of Massachusetts â Amherst (32), University of Maryland System (25),University of Michigan â Ann Arbor (23), University of New Hampshire (17), University of New Mexico (16), University of Pennsylvania (17), University of Rochester (22), and Williams College (9)
Targeted: 23 Colleges
Boston University (50 pre-litigation settlement letters), Columbia University (20), Dartmouth College (11), DePaul University (18), Drexel University (20), Ferris State University (17), Ithaca College (20), Purdue University (38), University of California - Berkeley (19), University of California - Los Angeles (21), University of California - Santa Cruz (17), University of Maine system (27), University of Nebraska - Lincoln (25), University of Wisconsin system (66, including the following individual campuses: Eau Claire, Madison, Milwaukee, Parkside, Platteville, Stevens Point, Stout, and Whitewater), Vanderbilt University (20), and Virginia Polytechnic Institute & State University (16)
Targeted: 13 Colleges
Arizona State University (23 pre-settlement litigation letters), Marshall University (20), North Carolina State University (37), North Dakota State University (20), Northern Illinois University (28), Ohio University (50), Syracuse University (37), University of Massachusetts â Amherst (37), University of Nebraska â Lincoln (36), University of South Florida (31), University of Southern California (20), University of Tennessee â Knoxville (28), and University of Texas â Austin (33)
Legal Notes & Guides
Cornell Law School Legal Information Institute - US Code: Title 17, Copyrights
Cornell Law School Legal Information Institute - Constitution: LII
NET: The No Electronic Theft Act
DMCA: The Digital Millennium Copyright Act
Family Entertainment and Copyright Act
Cornell Law School Legal Information Institute - US Code: Title 17, Chapter 1, Section 107, Fair Use
Frequently Asked Questions (and Answers) about Copyright and Fair Use
Resources from Gutman Library
The following resources are pulled from Harvard's library system. You need a Harvard University ID and PIN to access them.
Don't Shoot The Messenger: Copyright Infringement In The Digital Age, 2003
U.S. to step up piracy battle, 2007
France Debates Downloads, With Teenager As Top Expert, 2006
Record industry sues fans for illegally downloading music from the internet, 2004
Discussing Cyber Ethics with Students Is Critical, 2003